Set Up Active Directory Authentication Server
Requirements
- Enable the Active Directory (LDAP) Authentication Provider
- Windows Server Active Directory (AD) with LDAP
- Device created in senhasegura for AD Server with LDAP
- Credential created with AD Server domain user to read the users from the domain
Step by Step
To set up the authentication in senhasegura via Active Directory, follow these steps:
Access the menu: Settings ➔ Authentication ➔ Servers
Click on the New Server report button
Fill in the LDAP server fields
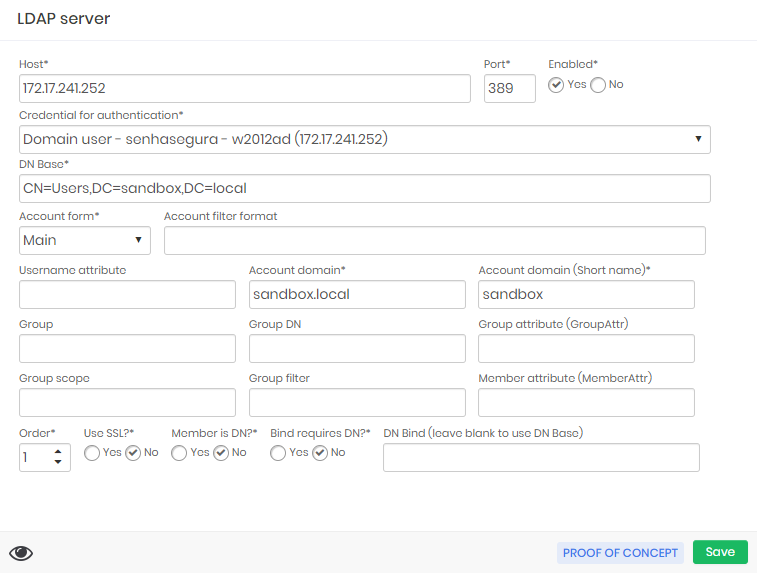
| Field | Description |
|---|---|
| Host | Hostname or IP of the AD server. Example: 192.168.20.20 We recommend always using the IP and not a DNS - Avoid use DNS. |
| Port | LDAP communication port number. The default protocol port number, 389 (LDAP unsecured), if Use SSL? is selected as "yes", be sure to use the correct port by default with SSL is used port 636. |
| Enabled | Indicates whether the server is enabled or not for use. |
| Credential for authentication | Credential that will be used to perform the user authentication on the server and users synchronization between servers. |
| DN Base | Distinguished Name Base of your server, this will serve as the basis for the LDAP queries. |
| Account form | The users query can be performed using the following formats:
|
| Account filter format | Account filter format parameters. |
| Username attribute | The attribute of the username to be searched. Example: "cn" |
| Account domain | Account domain name from the LDAP server used. |
| Account domain (short name) | Name of the domain to which the account belongs. |
| Group | Group name. |
| Group DN | Distinguished name of the group. |
| Group attribute (GroupAttr) | The attribute of the group to be searched. Example: "cn" |
| Group scope | Description of group scope, objective; |
| Group filter | String that will be added to the search filter when searching for a group. Example: ( OR=name_of_or,dc=domain,dc=local) |
| Member attribute (MemberAttr) | Distinguished name of objects in the group that you can find. |
| Order | Number to set server priority, lowest the number will have more priority to be used, in cases that one server fails the second in order will be used |
| Use SSL? | Indicates whether authentication will use the SSL connection or not. If using SSL, be sure to add the correct port |
| Member is DN | Indicates whether the member is DN or not; |
| Bind requires DN? | Indicates whether bind requires DN; |
| DN Bind (leave blank to use DN Base) | DN Bind Parameters; |
Once registered and active, senhasegura can use this server to authenticate users.
Click on the Save button to complete the registration
Click on the More options ( ⁝ ) and select Test Authentication
Fill with an user from the AD server that should be able to authenticate, type the user password and click Authenticate
If it shows you a green authentication alert, the Active Directory Authentication Server is now ready to be used.
Please check our common AD LDAP errors in case of some errors.