Audit and traceability
Reports
Introduction
senhasegura enables automated control of privileged credentials access monitoring that results in reports that can be evidenced for an audit process.
The Reports can be found in a central repository on the menu, granting an easy source of evidence to periodic audits. The reports give complete information about "who, when, where, why, ..." executed the actions through the senhasegura .
All those logs and reports give the company a high level of security governance, including:
Privileged activity logging of all actions performed by administrators and regular users with a complete audit trail of who performed each action;
Centralized privileged activity auditing and reporting with reports and dashboards;
Privileged session reports with search across all text typed and displayed during a session and a video;
A forensic search of actions and events identified during a session;
Definitions
senhasegura uses a specific terminology for its functions and functionalities. Thus, some terms must be understood before starting to use the solution:
Access groups: used to grant and manage viewing and access to vault credentials;
Auditor: User with a profile for the issuance of specific reports in the senhasegura solution;
Equipment parameters: behavior settings that can be adjusted in the solution for each type of equipment;
Global parameters: behavior settings that can be adjusted globally in senhasegura ;
Governance ID: it is used to associate an activity performed in senhasegura to a Changes Management item, such as a Help Desk ticket, for instance;
Password custody: possession and use of credentials stored in the senhasegura solution by the user;
Protected information: any type of privileged information, such as hashes, RSA keys or digital certificates;
Password parameters: Behavior settings that can be adjusted in the solution for each credential;
Password policy: set of rules determined to improve the security of a company's users and devices;
Password strength: a measure that assesses a password's effectiveness against attacks, and it is based on estimating the number of attempts to guess it;
PCI: PCI Security Standards Council is a global forum for the ongoing development, enhancement, storage, dissemination and implementation of security standards for account data protection;
User: In-house employees, interns or third parties who use or may require access to the company's systems;
The reports
This section aims to present the reports that senhasegura provides and how to use them.
This manual is divided in the following parts:
PCI Reports: information required by PCI standards to identify possible areas of non-compliance;
Traceability: information on all changes made to data registered;
Accesses to the system: information on user accesses;
Events: information on various events related to credentials;
Credentials: information on the use of the credentials stored on the vault;
Access Control: information on actions perform by the users and access groups;
Permissions: information on the permissions related to the screens, roles, profiles and permissions;
PCI Reports
Some of the PCI DSS requirements demand companies to implement controls that assign a unique identity to each person with access to a computer, as well as fully monitoring network resources and customer payment data. The purpose of these reports is to display information required by PCI standards, and thus enable the auditor to identify possible areas of non-compliance. Accessing the menu Reports ➔ PCI you will see the following reports:
Password expiration
This report shows the expiration dates of all credentials passwords that are registered in senhasegura . This report is important for the comparison between the company's password policy and the real application of the password expiration date.
The Password expiration report will print the following information:
Credential: the username and password that will be detailed;
Device: the credential is used to access;
Password policy: that is configured to set the password change period;
Password change: status of the automatic password change;
Last change attempt: is the date of the last time the system tried to change the password based on the policy setted;
Last attempt status: shows if the last change attempt performed the change or not;
Last change successfully: is the date of the last time the system changed the password automatically;
Next change: is the date based on the policy that the password should be changed;
Expiration: is the date limit to perform the password change;
Password age: is the number of the days the password is being in use;
Status: shows if the password is expired or not;
Password expiration Dashboard
It is also possible to have a general view on the number of expired passwords on the dashboard menu, to view this board access: Dashboard ➔ PAM ➔ Password changes.
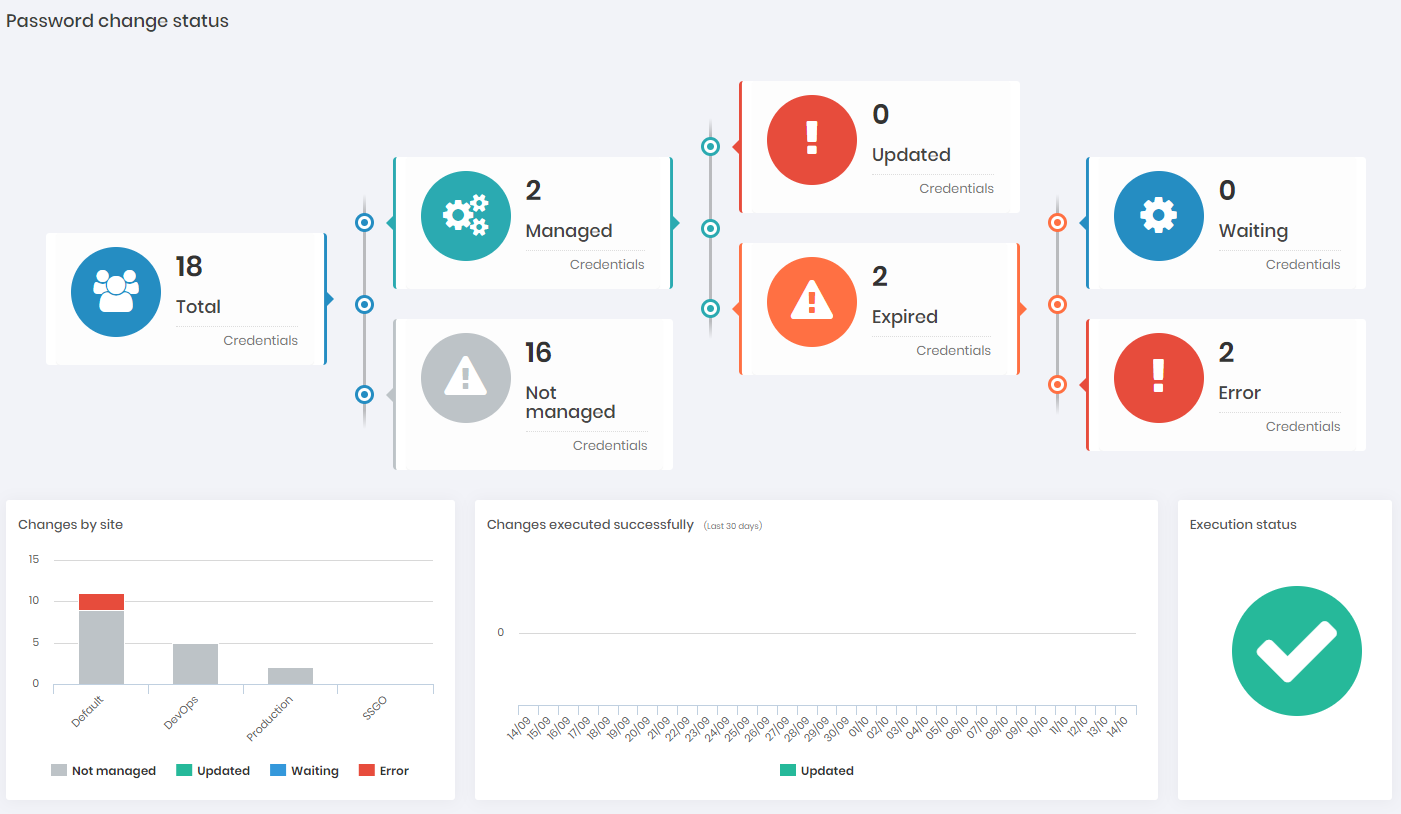
The credential quantities and their status are presented considering the following rules:
Child credentials will only be considered on this dashboard if their respective parent credentials have the automatic change active. In some cases the system does not schedule a specific change for the child credential, creating and executing the change at the time of executing the parent credential change. The "Waiting" and "Error" dashs will not necessarily display the sum of "Updated" and "Expired", as they depend on the behavior of each change.
The Password expiration report will print the following information:
The following counts managed/non-managed credentials:
Updated:
: Over 25% managed credentials
: 5% to 25% managed credentials
: Under 5% managed credentials
Expired:
: None expired
: At least one expired
Not managed:
: Credentials without automatic password change enabled
Execution status:
: No problems
: Any problem with up to 2 robots simultaneously (all active)
: Any problem on the 3 robots simultaneously.
The following counts expired credentials that have the "password change" flag activated:
Waiting:
: More than 75% of managed credentials
: Less than 75% of managed credentials
Error:
: Without errors
: With at least one error
Credentials by users
This report shows all credentials that every user registered in senhasegura system can have access. This report is relevant for the comparison between the user's access privileges set by the company's policy and current conceded privileges.
The Credentials by users report will print the following information:
Name: is the name of the user that will be detailed;
Username: is the username used to access senhasegura ;
Device: is the devices the user has access privileges;
Credential: is the credential the user has privileges to use to access the device;
Department: is the company's department the user belongs;
Access group: is the access group the user is a member;
Part of password: is the level of privilege the user has in relation with the credential's password: can see the complete or just a part of the password;
View: show if the user has permission to visualize the password;
View reason: shows if the user have to enter a reason to view the credential;
View approval: shows if the user have to be approved to view the credential;
Session: show if the user can perform a session using the credential;
Session reason: shows if the user have to enter a reason to perform a session using the credential;
Session approval: shows if the user have to be approved to perform a session using the credential;
Password custody
This report shows all the passwords that are under custody of any user registered in senhasegura system. This report is relevant for the comparison between the users access privileges set by the company's policy and the current privileges and access conceded.
The Password custody report will print the following information:
User: is the name of the user that will be detailed;
Credential: is the credential under the user's custody;
Device: that the credential under custody access;
Begin of custody: is the date the user take the credential's custody;
Last view: is the date of the last time the user view the password;
End of Custody: is the date the user lost the custody over the credential;
Duration: is the period the credential was under the user's custody;
Password custody Dashboard
It is also possible to have a general view on the users and the number of custody conceded on the dashboard menu, to view this board access: Dashboard ➔ PAM ➔ Custody.
Password query
This report shows all the attempts to view a passwords by the users registered in senhasegura system. This report is relevant for the comparison between the users access privileges set by the company's policy and the current privileges and access conceded.
The Password query report will print the following information:
Name: is the name of the user that will be detailed;
User: is the username used to access senhasegura ;
Department: is the company's department the user belongs;
Status: shows if the password view is enabled for the user;
Total: The number of views perform by the user.;
It's also possible to see more details about the queries clicking on the action icon of the register.
Remote sessions
This report shows the history of remote sessions performed by users registered in senhasegura system. This report is relevant for the comparison between the users access privileges to perform remote sessions set by the company's policy and the current privileges and access conceded.
The Remote sessions report will print the following information:
User: is the name of the user that will be detailed;
Credential: used by the user to perform the remote access;
Device: which was access and the port used;
Session ID: is the identification code of the particular session;
Start: is the day and time the session started;
Final: is the day and time the session finished;
Duration: the total time of the session;
Protocol: used to performed the session;
Origin: of the access performed;
Remote sessions Dashboard
It is also possible to have a general view on the remote sessions performed by the users on the dashboard menu, to view this board access: Dashboard ➔ PAM ➔ Remote sessions.
Denied access
This report shows the history of the denied access performed by users registered in senhasegura system.
This report is important for the comparison between the users access privileges to perform remote sessions set by the company's policy and the current privileges and access conceded.
The Denied access report will print the following information:
Operation: is the action the user attempt to perform;
User: is the name of the user that attempted to operate the action;
Credential: the user attempt to use to perform the access;
Device: the user attempt to access;
Access request: is the day the user requested the access;
Access rejection: is the day the approver denied the access;
Approvers: is the users that are selected to approve the access requests from that user;
It's also possible to see more details about the denied access clicking on the action icon of the register. % Redefinindo a pasta atual do capitulo
Traceability
In a productive environment changes as constants and important to improve the process, however, is important to know "why, how and by who" the changes happened.
The purpose of these reports is to display information on all changes made to data registered in senhasegura .Accessing the menu Reports ➔ Traceability you will see the following reports:
Access groups
This report shows the history of the changes made on the access groups registered in senhasegura system. This report is important to know what changes were made and by which user to understand if the privileges of each group still in compliance with the access flow set by the company's policy also if the users are in the right groups receiving the permissions they need to execute they activities.
The Access groups report will print the following information:
Name: is the access group name that will be detailed;
User: is the name of the user who performed the changes;
Username: is the username used to access senhasegura ;
Operation: is the description of the changes performed by the user;
Origin: is the senhasegura module used to perform the change;
IP: of the user device to perform the change;
Date/Time: the changed was performed;
It's also possible to view what exactly was changed through a comparison between the original data to the recent alteration clicking on the action icon of the register.
Password policies
This report shows the history of the changes made on the password policies registered in senhasegura system. This report is important to know what changes were made and by which user to understand if the passwords expiration and viewing periods still in compliance with the company's policy and security expectations.
The Password policies report will print the following information:
Name: is the password policy name that will be detailed;
User: is the name of the user who performed the changes;
Username: is the username used to access senhasegura ;
Operation: is the description of the changes performed by the user;
Origin: is the senhasegura module used to perform the change;
IP: of the user device to perform the change;
Date/Time: the changed was performed;
It's also possible to view what exactly was changed through a comparison between the original data to the recent alteration clicking on the action icon of the register.
Password strength
This report shows the history of the changes made on the password strength registered in senhasegura system. This report is important to know what changes were made and by which user to understand if the passwords has the level of complexity and strength in compliance with the company's policy and security expectations.
The Password strength report will print the following information:
Name: is the password strength level name that will be detailed;
User: is the name of the user who performed the changes;
Username: is the username used to access senhasegura ;
Operation: is the description of the changes performed by the user;
Origin: is the senhasegura module used to perform the change;
IP: of the user device to perform the change;
Date/Time: the changed was performed;
It's also possible to view what exactly was changed through a comparison between the original data to the recent alteration clicking on the action icon of the register.
Credentials
This report shows the history of the changes made on the credentials registered in senhasegura system. This report is important to know what changes were made and by which user to understand if the new and current credentials still have the access permissions and settings in compliance with the company's policy and security expectations.
The Credentials report will print the following information:
Credential: that admit the changed;
Device: where the credential admitted the changes;
User: is the name of the user who performed the changes;
Username: is the username used to access senhasegura ;
Operation: is the description of the changes performed by the user;
Origin: is the senhasegura module used to perform the change;
IP: of the user device to perform the change;
Date/Time: the changed was performed;
It's also possible to view what exactly was changed through a comparison between the original data to the recent alteration clicking on the action icon of the register.
Devices
This report shows the history of the changes made on the devices registered in senhasegura system. This report is important to know what changes were made and by which user to understand if the new and current devices still active and have the access permissions, credentials and settings in compliance with the company's policy and security expectations.
The Devices report will print the following information:
Device: that admit the changed;
User: is the name of the user who performed the changes;
Username: is the username used to access senhasegura ;
Operation: is the description of the changes performed by the user;
Origin: is the senhasegura module used to perform the change;
IP: of the user device to perform the change;
Date/Time: the changed was performed;
It's also possible to view what exactly was changed through a comparison between the original data to the recent alteration clicking on the action icon of the register.
Protected Information
This report shows the history of the changes made on the protected information in senhasegura system. This report is important to know what changes were made and by which user to understand if the new and current information stills integer, available and with access restrictions to the correct users in compliance with the company's policy and security expectations.
The Protected Information report will print the following information:
Name: is the protected information name that will be detailed;
User: is the name of the user who performed the changes;
Username: is the username used to access senhasegura ;
Operation: is the description of the changes performed by the user that could be a change or a new enter;
Origin: is the senhasegura module used to perform the change;
IP: of device the user performed the change;
Date/Time: the changed was performed;
It's also possible to view what exactly was changed through a comparison between the original data to the recent alteration clicking on the action icon of the register. % Redefinindo a pasta atual do capitulo
Access to the system
Organizations make efforts to protect their networks, infrastructure and especially data, to achieve this it is necessary to control the access to the security system like senhasegura as well. This control can protect the users' access to privileged credentials, as well as assets that aren't allowed according to their permissions.
In the other hand is important to know the time the access is being performed and how long the sessions on senhasegura system is being managed by the users, this can be useful to understand if the access policy is being followed or if the privileges are being abused.
In this section, you can print reports related to all the access to the senhasegura system with information such as users logged on the system, the first and last login of a user and more. Accessing the menu Reports ➔ Access to the system you will see the reports:
Logged users
This report shows the users that are currently logged in senhasegura system. This report is important to know who is using the system, from where the access is performing the time the session started when the user must log again. This report helps to understand if the current information complies with the user's access restrictions, the company's access policy and security expectations.
Name: is the user name that will be detailed;
Username: is the username used to access senhasegura ;
IP: of device the user performed the access;
Login: is the time and date the access started;
Last: request is the time and date the user execute the last an action (before the report was displayed) in the system;
Expiration: is the time and date the user will be requested to login again in the system to continue its actions;
Access history
This report shows all system users access history information. This report is important to know how long the user is being active on the system and the number of logins it's was performed by the user till now. This report helps to understand the system doesn't have an enabled user that shouldn't be and more information is in compliance with the list of enabled users, user's access restrictions, the company's access policy and security expectations.
The System access history report will print the following information:
Name: is the user name that will be detailed;
Username: is the username used to access senhasegura ;
Access: is the number of access performed by the user since his first login;
First Login: is the time and date the user login in the system for the first time;
Last Login: is the time and date the user login in the system for the last time;
Logged: indicate if the user detailed is using the system on the moment;
Adapter: indicate the access type;
It's also possible to see more details about the user's system access clicking on the action icon of the register.
Source access
This report shows all system users' origin access information. This report is important to know from where the access being originated if it is a trustful or unusual origin. This report helps to understand if the access to the system is being performed trough sources allowed and trusted in compliance with the list of allowed sources, user's access restrictions, the company's access policy and security expectations.
The System sessions origin report will print the following information:
Origin: IP is the IP used to access the system;
Username: is the username used to access senhasegura ;
Name: is the user name that will be detailed;
Department: is the company's department the user belongs;
Session start date:is the time and date the user login in the system from the source;
Day of session start week: is the day of the week the session started from the source;
Session end date: is the time and date the user logout of the system from the source;
Session week end day: is the day of the week the session ended from the source;
Duration: indicate how long the session from the source lasted;
Events
senhasegura executes, automatically or by a user, events such as password change, backups, insert of new information and more. Those events are relevant to be tracked to what was executed by the system because those events are configured by the administrator, it is important to know if the system settings expected by the company's security policy is being achieved.
The events report can print data about how the system is working by the settings. Accessing the menu Reports ➔ Events you will see the following reports:
Password operation
This report shows all the passwords operations performed by the system. This report is important to know how the system is executing the operations related with passwords set by the administrator. The password's operations should achieve the company's password policy and security expectations.
The Password operation report will print the following information:
Origin IP: is the IP used to access the system;
Device: where the password operation was performed;
Credential type: of the password which admitted the operation;
Status: related on how the operation finished;
Operation: the password admited;
Schedule date: is the time and date the operation was scheduled to be performed;
Execution date: is the time and date the operation was executed;
Last attempt: is the time and date the system tried to execute the operation;
Attempts: is the number of the times the system tried to execute the operation;
Requester: is the name of the user, task or set that request the operation for the system;
It's also possible to restart an operation that finished on error or need to be performed again clicking on the action icon of the register restart execution or view the attempt details clicking on view attempts.
Password view
This report shows all the password view senhasegura intercede for users requests. This report is important to present all the access flow the system supports and the access type configured by the administrator, this can be useful to compare the access flow and system access settings with the company's access policy and security expectations.
The Password view report will print the following information:
Date: the view as performed;
Operation: the system intercede;
User: that requested the access;
IP: used to access the system;
Credential type: of the password which was viewed;
Device: is the asset the password viewed gave access;
Username: is the user the password viewed belongs to;
Reason: is the type of justification the user gives to view the password;
Governance ID: it is the code used to track the view in senhasegura ;
Reason: is the justification text the user gives to performed the view;
Message: is what the system print to the requester related with the permissions and more;
Origin: indicate the platform used to access;
It's also possible to see more details about the views clicking on the action icon of the register.
Password view Dashboard
It is also possible to have a general view on the Password view performed by the users on the dashboard menu, to view this board access: Dashboard ➔ PAM ➔ Behavior.
Performed backups
This report shows all the backups performed by senhasegura request to be exported. This report is important to prove the backup is being produced correctly and in the time and date set by the companies's backup policy and the security expectations from the companies and standards.
The Password view report will print the following information:
Type: of backup. Indicates if the data recover the full data or partial;
Reason: how the backup was performed ;
Start: is the day and time the data started to be transferred to backup;
End: is the day and time the data stopped to be transferred to backup;
Requested: by is the name of the user who requested to export the backup;
It's also possible to download the backup performed clicking on the action icon of the register.
Audit tracking
This report summary all the trails senhasegura register for the actions performed in the system. This is easy and fast consult report to view the trail records.
The Audit tracking report will print the following information:
Operation: the system intercede;
Entity: the operation was performed;
Entity name: the operation was performed;
Origin: is the senhasegura module used to perform the change;
User: is the name of the user that will be detailed;
Username: is the username used to access senhasegura ;
IP: of the user device to perform the change;
Change: Indicates if the operation was a change or not;
Date/Time: of the trail was registered;
It's also possible to see more details about the registered tracks, clicking on the action icon of the register % Redefinindo a pasta atual do capitulo
Credentials
Credentials automatically rotation is used by administrators to access critical systems across the organization, because of this kind of situation, auditing and monitoring privileged accounts are so important.
Through this senhasegura enabled reports that can be used to understand how the credentials are being used, the groups which can manipulate the credential and more. Accessing the menu Reports ➔ Credentials you will see the following reports:
Credentials overview
This report summarizes all the credentials' trails senhasegura register in the system. This is easy and fast consult report to view the trail records.
The Credentials overview report will print the following information:
Username: of the credential detailed;
Credential type: of the one detailed. The types can be local user, local administrator, domain user and others;
Status: indicates if the credential's username available to use;
Creation date: is the day and time the credential was registered on the system;
Expiration date: is the day and time the credential was disabled on the system;
Last change: is the day and time the credential was modified;
Last view: is the day and time the credential was viewed;
Last use: is the day and time the credential was used to access;
Password use
This report shows all the credentials registered in the system and the last time the credential was used to perform access. The report is significant to verify if a credential is being managed by the users that have permission to do it; if the access is being performed in an allowed time according to with the company's access policy and the security expectations from the company and standards.
The Password use report will print the following information:
Credential: of the password used;
Device: the password is used to access to;
Operation: performed using the password;
User: that accessed using the password;
User IP: used to use the password;
Date/Time: is the day and time the password was used;
Origin: is the platform the user used to use the password;
Target: is the device the password was used to access;
Users by group
This report shows all the system's users registered in senhasegura and the groups they are members. The report is significant to verify if the user has the necessary permissions, or have more, to execute its activities. The auditor can cross-check if the user access permissions are correct according to with the company's access policy, responsibility matrix and the security expectations from the company and standards.
The Users by group report will print the following information:
Name: of the user;
Username: is the username used to access senhasegura ;
Department: is the company's department the user belongs;
Access group: the user belongs;
Assignment date: is the date and time the user started to be a member of the group;
Assigned by: is the user who included the other one in the group;
Part of password: is the level of privilege the user has in relation with the credential's password: can see the complete or just a part of the password;
It's also possible to see more details about users by group, clicking on the action icon of the register
E-mail processing
This report shows all the emails senhasegura sent for users requests. This report is relevant to present all the access requests, this can be useful to compare the access flow and system access settings with the company's access policy and security expectations.
Policy definition
This report shows the history of the changes made on the password policies registered in senhasegura system. This report is important to know when was changed, the usernames and devices that admitted the changes to understand if the passwords expiration and viewing periods still in compliance with the company's policy and security expectations.
The Policy definition report will print the following information:
Date: day and time the changed was performed;
Policy: is the password policy name that will be detailed;
Type: of the credential which admitted the change;
Username: that admitted the changes;
Hostname: of the device which admitted the change;
Strength: is the level of complexity of the password that will be built;
Expiration period: is the limitation period to perform the password change;
View expiration: is the limitation period to view a password;
Message: is what the system print to the requester related with password policy change;
Access control history
It is necessary to control the access to the security system like senhasegura to prevent unauthorized access to privileged credentials, assets and more that are stored on the system.
In this section, you can print log reports of the users and group activities conducted trough senhasegura with information such as date of the activity, credential and user accessed and more. Accessing the menu Reports ➔ Access control you will see the following reports:
Access control logs
This report shows the access control history of the activities made by each system users and the approvals requirements when needed. This report is important to understand if the privileges of each user still in compliance with the access flow set by the company's policy also if the users need approval or not to execute activities.
The Access control logs report will print the following information:
Date: day and time the changed was performed;
Operation: performed by the user;
User: is the name of the user that will be detailed;
IP: of device the user performed the operation;
Credential type: of the password which was accessed ;
Device: that was accessed;
Username: that was accessed;
Reason: is the type of justification the user gives to access the credential;
Governance ID: it is the code used to track the access in senhasegura ;
Reason: is the justification text the user gives to perform the view;
Message: is what the system print to the requester related to the permissions and more;
Origin: indicate the platform used to access;
It's also possible to see more details about the access clicking on the action icon of the register.
Access group logs
This report shows the access logs through the access group perspective with logs of the group modifications made by each system users such as group creation, user removal and more. This report is important to understand if the privileges of each user still in compliance with the access flow set by the company's policy also if the users need approval or not to execute activities. As well input the non-repudiation, proving that the user's username was the one who performed the modification.
The Access group logs report will print the following information:
Date: the group was modified;
Operation: the user performed on the group;
User: is the name of the user that performed the modification;
Group: that was modified;
User group: is the name of the user that admitted the modification;
Message: is what the system print after the modification;
It's also possible to see more details about the access clicking on the action icon of the register. % Redefinindo a pasta atual do capitulo
Permissions
Privileges granted in excess or not revoked at the right time make malicious action easy. Privileged users need access to privileged accounts to perform daily routines for performing maintenance on systems, updating, and troubleshooting problems. However, these users may also misuse privileges to gain unauthorized access to information and cause damage.
Print a report that proves the privileges are being conceded to authorized users is crucial to an audit. The Permissions report in senhasegura shows what the systems users can see and do to the system and stored assets. Accessing the menu Reports ➔ Permissions you will see the following reports:
Screens by user
This report shows all the modules and its screens each senhasegura system users can see and interact. This report is important to understand if the privileges of each user still in compliance with the company's access policy also if the users have the information necessary to execute its activities.
The Screens by user report will print the following information:
Module: is the senhasegura functional characteristic, base to perform each functionality of the system;
Screen: is where each function is available to edit and execute;
User: is the name of the user that has the permission to see or interact with functionalities of the screen;
User status: indicate if the permission to interact with the screen is conceded to the user;
User roles
This report shows all the roles and role groups the senhasegura system users are configured. This report is important to understand if the privileges of each user still in compliance with the company's access policy also if the users can perform actions related with its permission level in the system according to with the company and security expectations. The User roles report will print the following information:
User: is the name of the user that has the role and are members of the role group;
Group: the role group the user is a member of;
Role: the permission the user can perform;
For a better understanding about roles and group roles see the System Users chapter on the Administrator Manual.
User profiles
This report shows all the profiles the senhasegura system users are configured with. This report is important to understand if the privileges of each user still in compliance with the company's access policy also if the attribution of profiles is correct and the right users are labelled with the suitable profile according to with what the company expect. The User profiles report will print the following information:
Department user: is the company's department the user belongs;
User: is the name of the user that has the profile;
User status: indicate if the user is being currently enabled or not on the system;
Department profile: is the company's department the profile belongs;
Profile: is the name of the profile that is being detailed;
Start: is the date the profile was attributed to the user;
For a better understanding about profiles see the System Users chapter on the Administrator Manual.
Role permissions
This report shows all the roles and role groups registered in senhasegura and the operations each one can perform. This report is important to understand if roles and groups are configured with the correct operations to give the privileges suitable for each user. The Role permissions report will print the following information:
Group: that holds the role that is being detailed;
Role: that holds the permissions that can be performed;
Permission ID: is the identification code of the permission the role concede;
Operation: is the permission or action the role allows the user to perform;
Profile permissions
This report shows all the profiles registered in senhasegura and the operations each one can perform. This report is important to understand if profiles are configured with the correct operations to give to each user the suitable profile. The Profile permissions report will print the following information:
Department: is the company's department the profile belongs;
Profile: that holds the permissions that can be performed;
Permission ID: is the identification code of the permission the profile concede;
Operation: is the permission or action the profile allows the user to perform;
Permissions and roles history
This report shows the history of the changes made on the roles' permissions registered in senhasegura system. This report is important to know what was made on the role and by which user to understand if the permissions of role still in compliance with the company's policy also if the users are in the right groups receiving the permissions they need to execute they activities.
The Permissions and roles history report will print the following information:
Date/Time: is the is the day and hour the role modification was performed;
Type: is the kind of modification performed;
User: is the name of the user that has the profile;
Message: is what the system print after the modification;
Permissions by role
This report presents the composition of permissions that each role has. The user can identify where a certain permission is being applied, facilitating the role definition to be applied to the user.
The report presents the information grouped by:
ID: Permission unique ID;
Permission: Permission unique nickname;
Module: Module to which permission belongs;
Type: Kind of action that the user will receive into the target entity;
Description: Brief description of the powers that permission grants;
Dashboards
An easy way to obtain information about the integrity and use of the system is through the Dashboards section. Some dashboards can be accessed from a user without permission to access and use credentials. In this way, you can create a generic user that can be on display for your security team monitoring. These dashboards are marked as "Showcase" in this documentation.
Access the dashboard through the menu Dashboard.
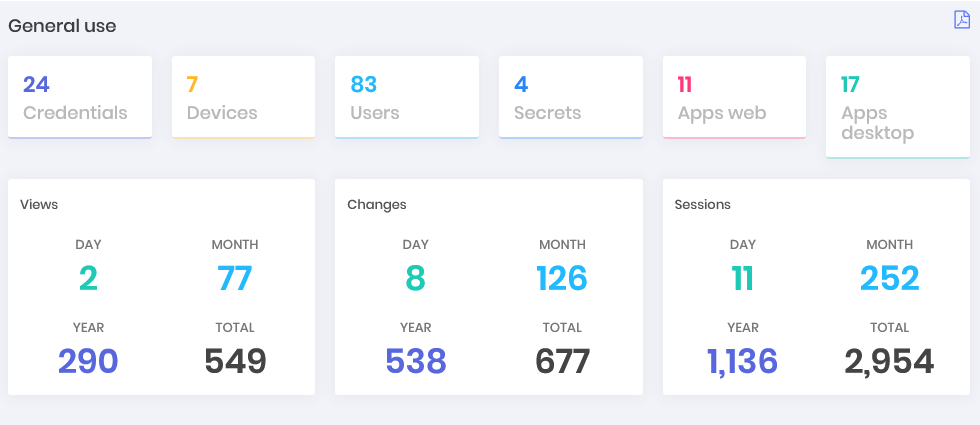
- General use: Follow the growth of credential records, devices, users, secrets, web clients and workstations managed by senhasegura . Also have visibility on how many queries, password changes and proxies sessions are being performed throughout the day, month, year and its total.
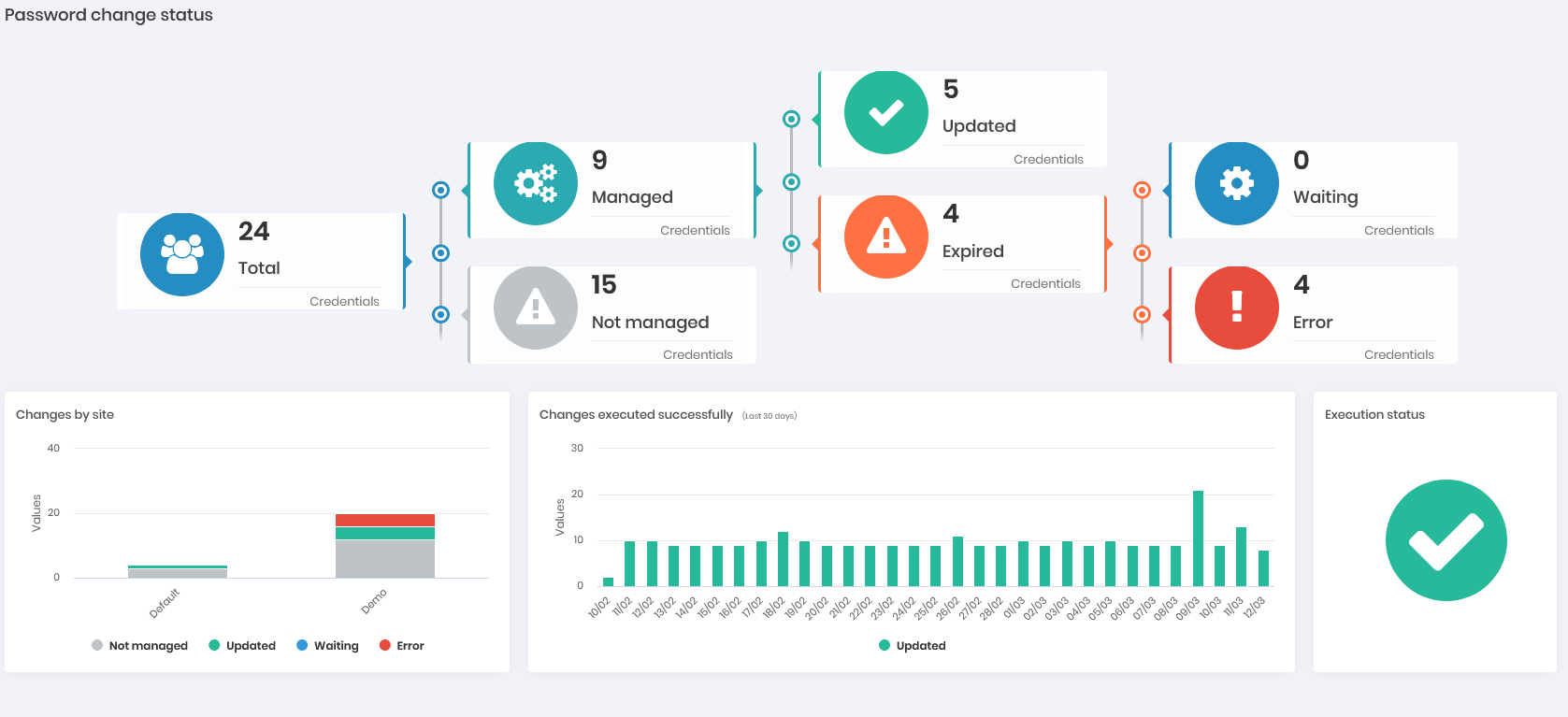
PAM
Password changes: Get visibility on how many credentials are managed by senhasegura and how many are configured with automatic password change and how many are not yet. Within the configured ones, how many are updated and how many have expired, as well as how many are waiting for the execution and how many had an execution error. With these data, see a segregation of these numbers by site and a graph showing the evolution of the exchanges that have occurred successfully over the days. (Can be displayed in Showcase)
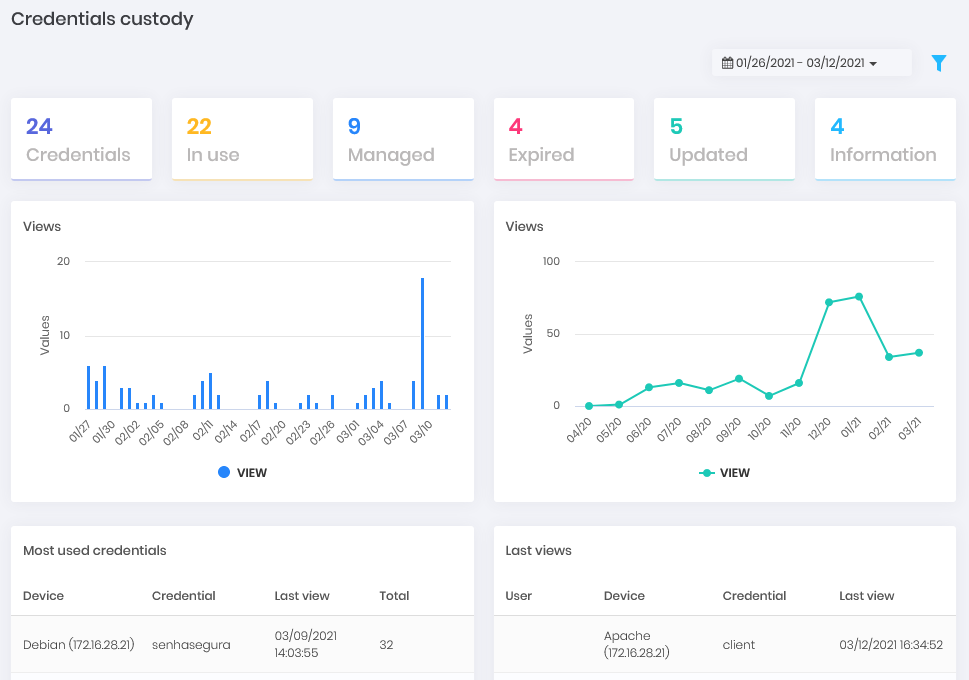
Password changes Dashboard Custody: In numbers and graphs, how many credentials managed by senhasegura are in use and the number of views per day. See also which credentials are in custody, which are the recent views and which are the most used.
Custody Dashboard Radar: In a sonar view, what are the proxy sessions that take place today and in the last 6 hours of the previous day. The proximity of the center is given by the minutes of login, where the smaller, the closer to the center you are. The peripheral division occurs by the time of occurrence. The colors vary according to the criticality of punctuation by the events of the session. The interactivity in the elements allows a drill down of the information.
Remote sessions: How many remote sessions took place within the various protocols served by the platform. Have a graphical view of the distribution by days and protocol. Active sessions are also broken down. (Can be displayed in Showcase)
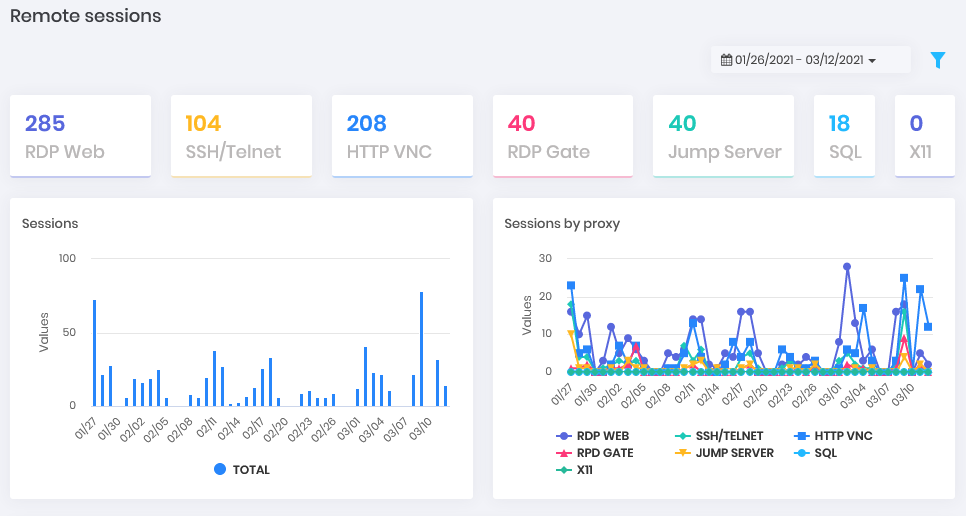
Remote sessions Dashboard Saved: How many sessions are physically persisted in senhasegura at the moment. How many were discarded by rotation and how many are marked not to be purged. Have this view by quantity, total duration and average duration. In the end, how much free space the platform counts to continue recording. (Can be displayed in Showcase)
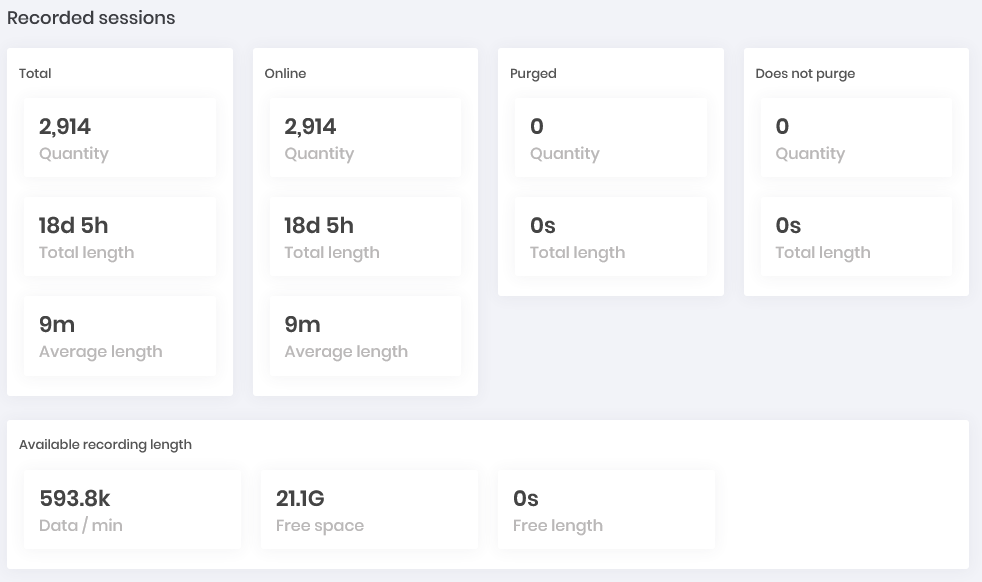
Saved Dashboard Commands: Within SSH proxy sessions, how many sessions were scored with audited commands and what is the cumulative severity of the days. Who are the users with the highest index severity and which are the source IPs with the highest command record audited performed.
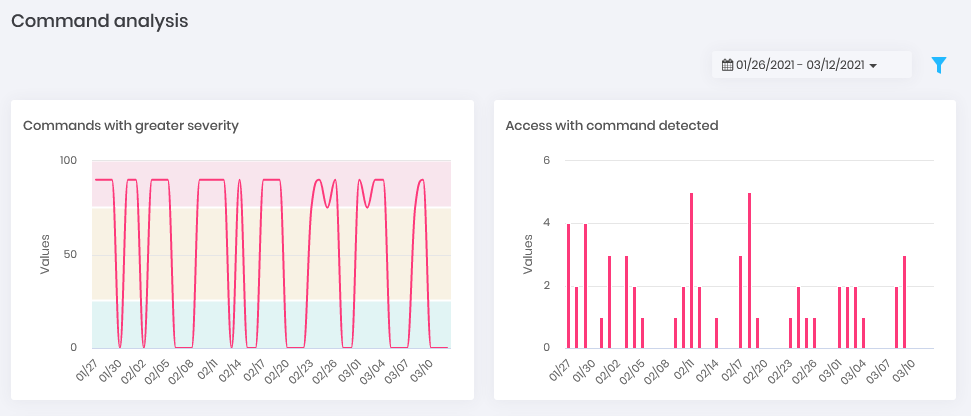
Commands Dashboard Behavior: Given the behavior of the user in relation to the data that he usually accesses and within the times when this normally occurs, what are the events that go beyond the standard. Get this view by day charts and ranking of accesses and password withdrawals.
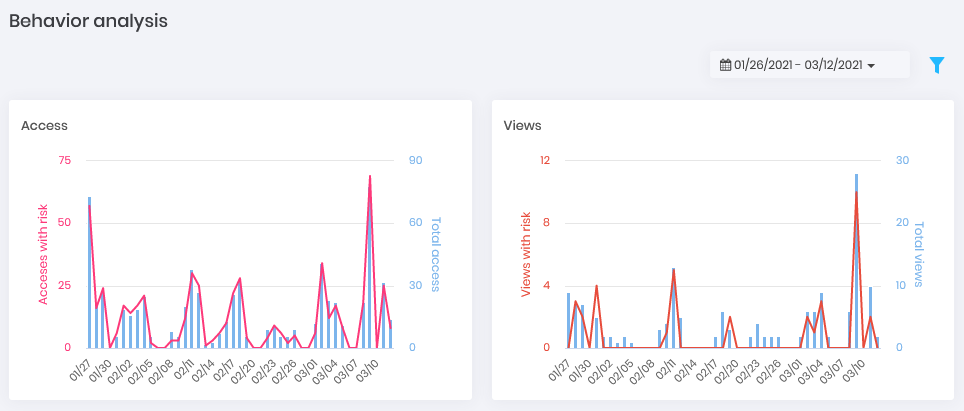
Behavior Dashboard Threats: Who are the users whose actions in accessing and withdrawing the password present the greatest risk to operations.
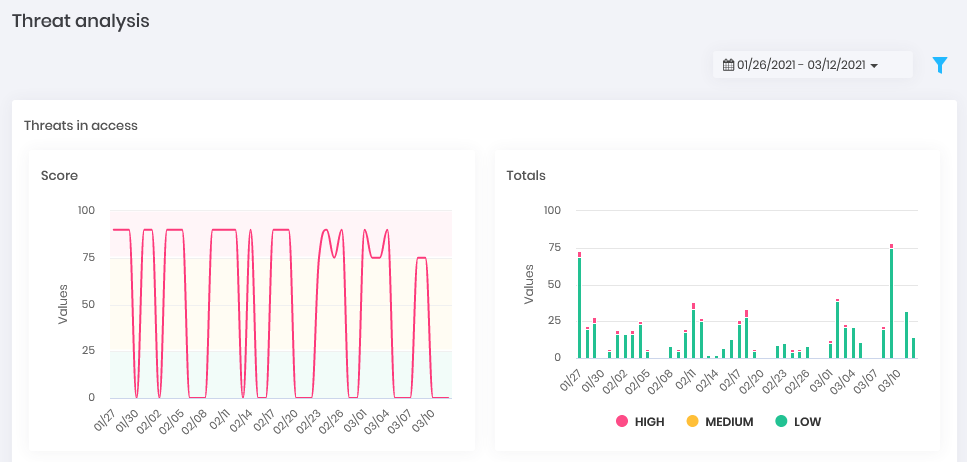
Threats Dashboard Disk Space: Have an evolutionary view on the platform's disk consumption. (Can be displayed in Showcase)
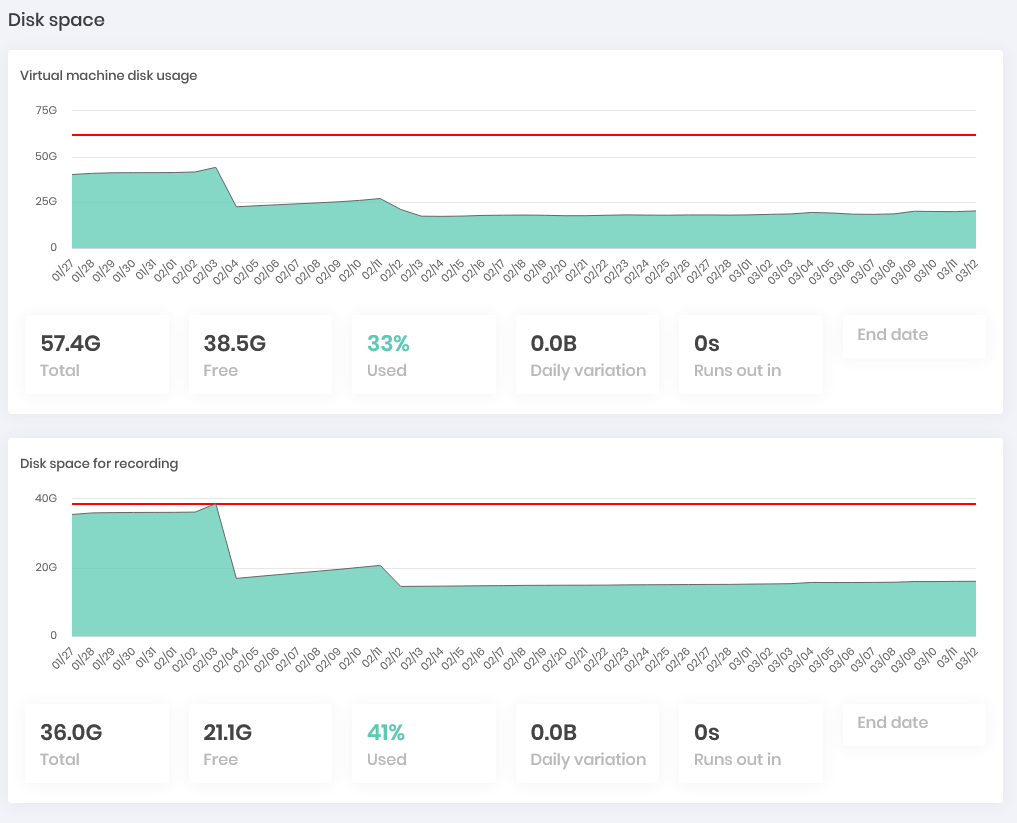
Disk Space Dashboard
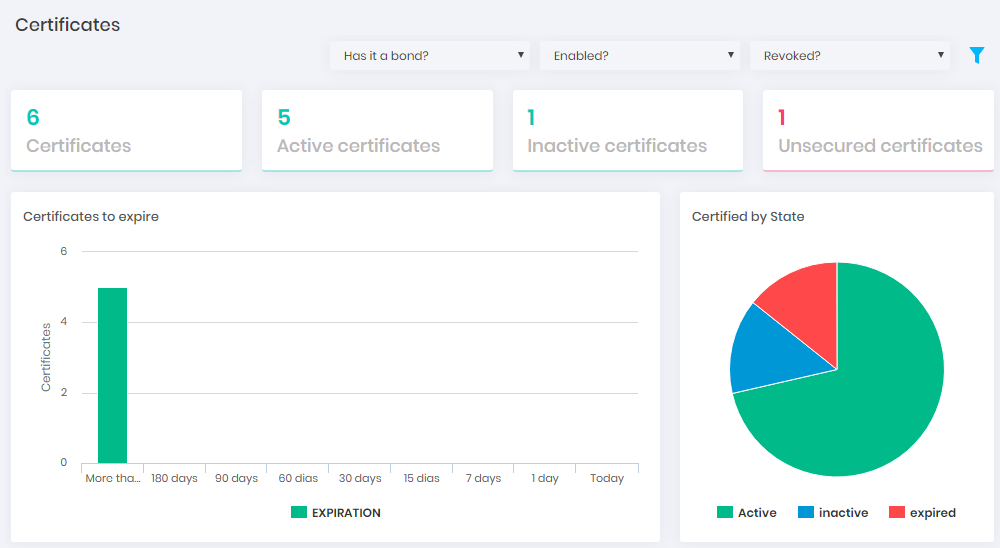
Certificates
This dashboard shows you how many certificates are being managed by senhasegura , how many of these are active, inactive and how many of them are considered unsafe. Have a graphical view to identify how many of these certificates are close to expiring in intervals ranging from more than 180 days to the current day. Other graphics help you to see how the certificates are distributed by environment, systems, CA, types, key size and other relevant attributes.
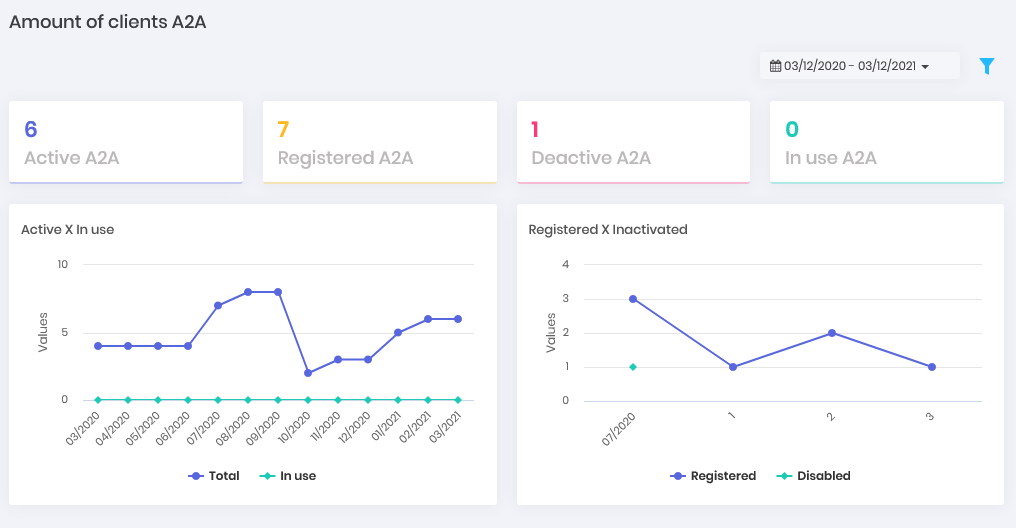
A2A
How many applications are using the platform to consume their managed data. Being segregated in how many are active and inactive, having a view of the evolution of use per day.
Task Manager
What is the success rate and error of execution of the tasks and how they are distributed by the environments and systems. What tasks are most performed and which target devices are most affected.
System consumption
Devices: How many devices are registered in senhasegura and how many are active, inactive and in use. How the device types are distributed and the evolution between active and inactive within a timeline.
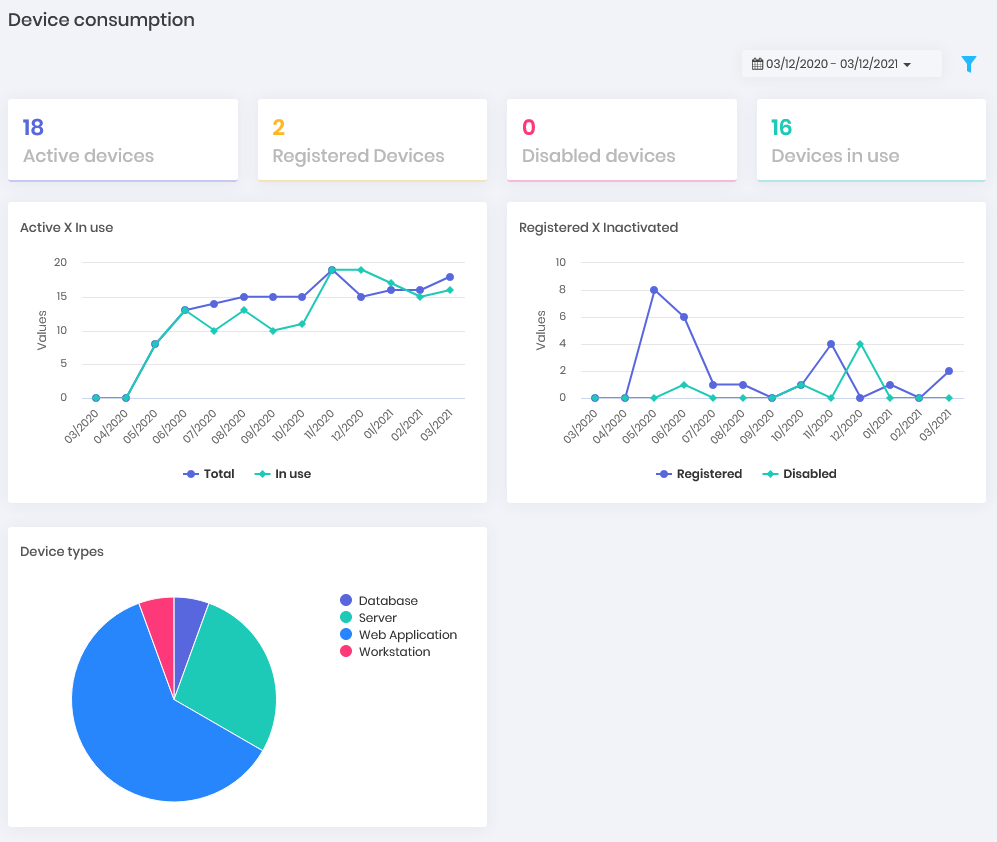
Devices Dashboard Credentials: How many credentials are registered in senhasegura and how many of them are active, inactive and in use. How is the evolution between active and inactive within a timeline.
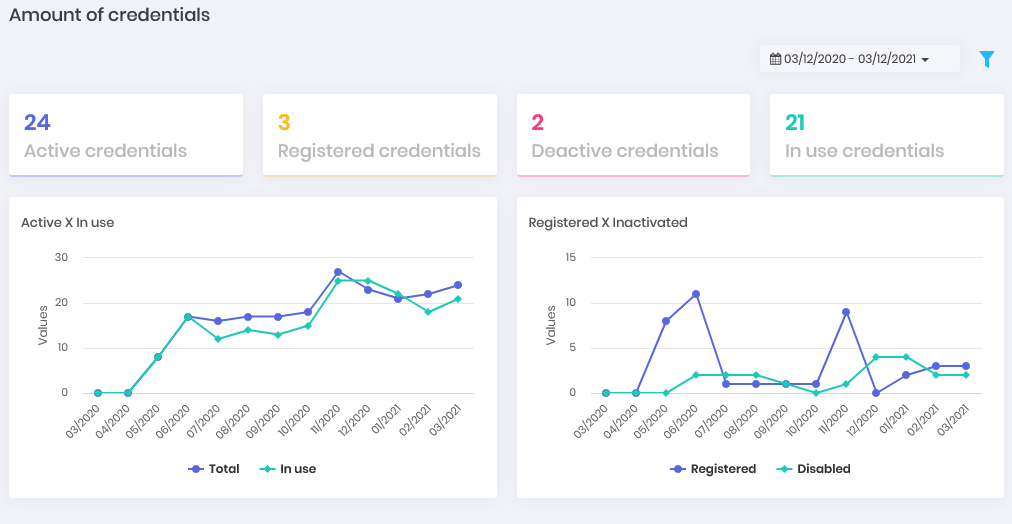
Credentials Dashboard Users: How many users are registered in senhasegura and how many of them are active, inactive and in use. How is the evolution between active and inactive within a timeline.
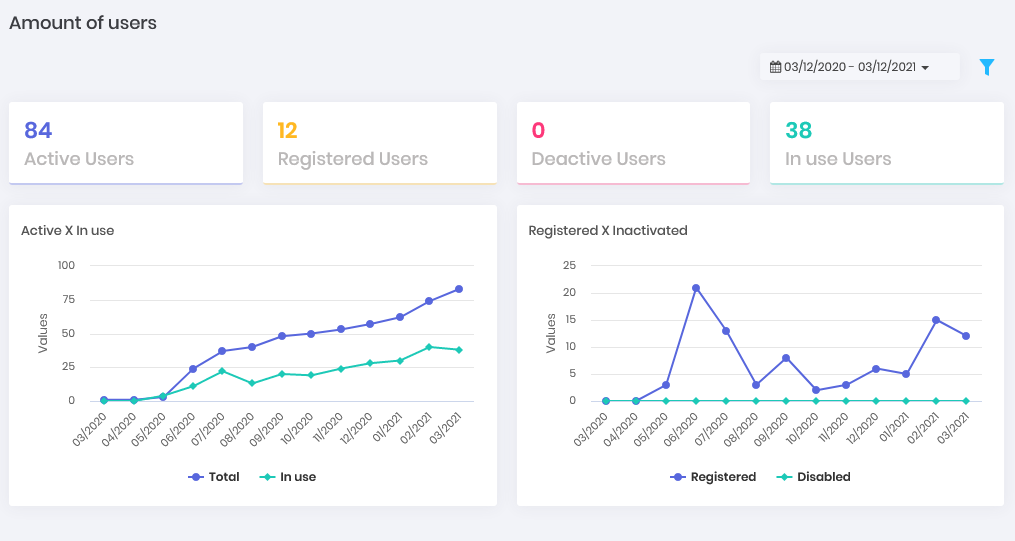
Users Dashboard Secrets: How many secrets are registered in senhasegura and how many of them are active, inactive and in use. How is the evolution between active and inactive within a timeline.
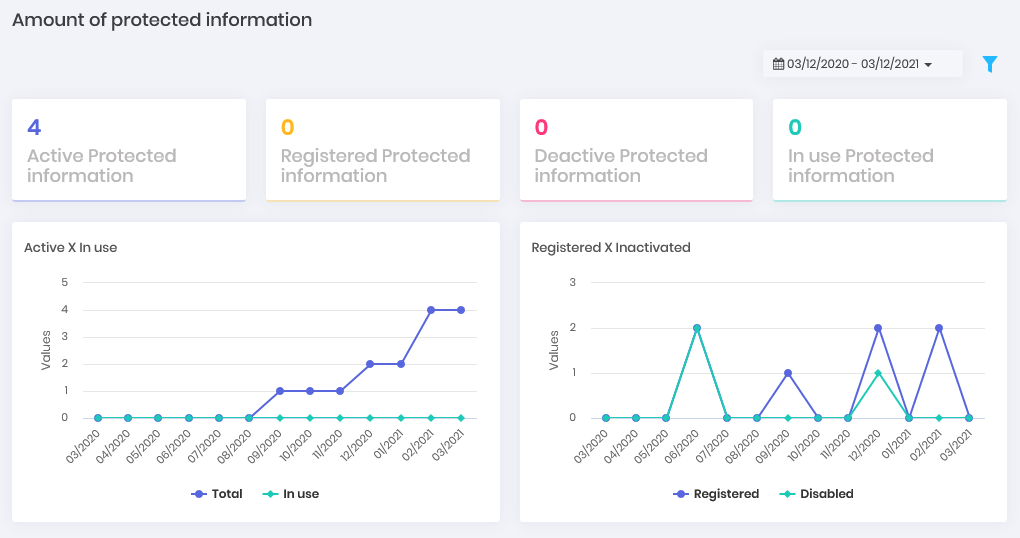
Secrets Dashboard Simultaneous: How many simultaneous proxy sessions take place on the platform and what type they are. (Can be displayed in Showcase)
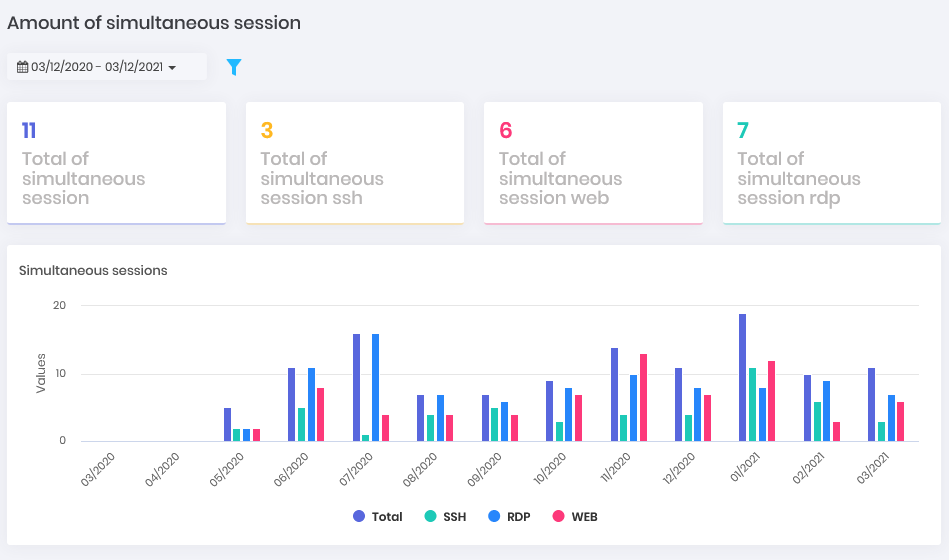
Simultaneous Dashboard
Behavior analysis
This section presents the reports that are compiled from the behavior that each user creates when using the senhasegura and the managed devices and credentials. This behavior is based on time, time, quantity and data segments used within a historical basis of all users or the user in question.
Although reports are focused on the type of anomaly, all user actions within the proxy session and password withdrawal activities are evaluated and scored considering all types of behavioral monitoring.
Excessive access
Menu Behavior ➔Behavior Analysis ➔ Excessive number of accesses.
It presents a ranking of credential accesses. Within each register it is possible to perform detailing through the registration action to have detailed access to the use of the credential.
The report of Excessive number of credential accesses presents the following information:
Target: credential destination device;
Credential: Credential that had excessive access;
Protocol: Protocol used in the session;
Privileged: Indicative of whether or not it is a credential for privileged use;
Accesses: Number of times the credential was used;
In turn, the detail report "Unusual access", accessible by the registration action, contains the following information:
ID: Usage identifier;
Origin: Ip of user who made use of;
User: Name of user who made use of;
Target: Target credential destination device;
Credential: Credential that had excessive access;
Protocol: Protocol used in the session;
Start: Login;
Ends: End of Session;
Duration: Session duration;
Privileged?: Indicative of whether or not it's a privileged use credential;
Origin?: Indicates if the origin is unusual to the use of the credential;
Destination?: Indicates if the destination is unusual to use the credential;
Credential?: Indicates if the use of the credential is unusual to the user;
Timetable?: Indicates if the time of use is unusual;
Duration?: Indicates if the session duration is unusual;
Risk: Is the risk score of this session given the amount of behavioral anomalies found;
Accesses at unusual time
Menu Behavior ➔ Behavior Analysis ➔ Accesses at unusual time.
Presents the list of all proxy accesses that occurred at unusual times. The following fields are present:
ID: Usage identifier;
Origin: Ip of user who made use of;
User: Name of user who made use of;
Target: Target credential destination device;
Credential: Credential that had excessive access;
Protocol: Protocol used in the session;
Privileged: Indicative of whether or not it is a credential for privileged use;
Start: Login;
Ends: End of Session;
Duration: Session duration;
Risk: Is the risk score of this session given the amount of behavioural anomalies found;
Accesses by unusual origin
Menu Behavior ➔ Behavior Analysis ➔ Accesses by unusual origin.
It presents a ranking of origins that scored more in quantity of accesses with anomalies, and its average risk score of these sessions. The detail will present the "Unusual Access" report, described above.
ID: Usage identifier;
Origin: Ip of user who made use of;
User: Name of user who made use of;
Target: Target credential destination device;
Credential: Credential that had excessive access;
Protocol: Protocol used in the session;
Privileged: Indicative of whether or not it is a credential for privileged use;
Start: Login;
Ends: End of Session;
Duration: Session duration;
Risk: Is the risk score of this session given the amount of behavioural anomalies found;
Accesses with unusual average length
Menu Behavior ➔ Behavior Analysis ➔ Accesses with unusual average length.
It is the relationship of proxy accesses with unusual length of time based on the pattern of user sessions. It presents the following fields:
ID: Usage identifier;
Origin: Ip of user who made use of;
User: Name of user who made use of;
Target: Target credential destination device;
Credential: Credential used for access;
Protocol: Protocol used in the session;
Start: Login;
Ends: End of Session;
Duration: Session duration;
Risk: Is the risk score of this session given the amount of behavioural anomalies found;
Unusual credential view
Menu Behavior ➔ Behavior Analysis ➔ Unusual credential view.
It presents a ranking of credentials that have suffered the most consultations with risk scores involved. The detail will present the "Unusual credential view" report, described above. The following columns are presented:
Device: Device hosting the credential;
Username: Credential that is ranked;
Password Type: Type of credential;
Additional information: Additional information from the credential, if you have;
Privileged?: Indicative of whether or not the credential is privileged;
Viewing data: Number of queries that were executed to this credential;
Total Risk: Sum of risk scores of the uses of this credential;
Views on unusual time
Menu Behavior ➔ Behavior Analysis ➔ Views on unusual time.
Presents all events where a user made a query on a particular credential at an unusual time.
ID: Usage identifier;
Origin: Ip of user who made use of;
User: Name of user who made use of;
Device: Target credential destination device;
Username: Credential that had unusual use;
Password Type: Type of credential;
Additional information: Additional information from the credential, if you have;
Privileged?: Indicative of whether or not the credential is privileged;
Viewing date: Date and time the consultation took place;
Risk: Sum of risk scores of the uses of this credential;
Views with unusual credential
Menu Behavior ➔ Behavior Analysis ➔ Views with unusual credential.
It shows all events in which a user made a query to a specific credential that he does not normally use.
ID: Usage identifier;
Origin: Ip of user who made use of;
User: Name of user who made use of;
Device: Target credential destination device;
Username: Credential that had unusual use;
Password Type: Type of credential;
Additional information: Additional information from the credential, if you have;
Privileged?: Indicative of whether or not the credential is privileged;
Viewing date: Date and time the consultation took place;
Risk: Sum of risk scores of the uses of this credential;
Views with unusual origin
Menu Behavior ➔ Behavior Analysis ➔ Views with unusual origin.
Presents all events where a user made a query to a particular credential from an unusual source.
ID: Usage identifier;
Origin: Ip of user who made use of;
User: Name of user who made use of;
Device: Target credential destination device;
Username: Credential that had unusual use;
Password Type: Type of credential;
Additional information: Additional information from the credential, if you have;
Privileged?: Indicative of whether or not the credential is privileged;
Viewing date: Date and time the consultation took place;
Risk: Sum of risk scores of the uses of this credential;
Audited command
Menu Behavior ➔ Occurrences ➔ Audited command.
Ranking of proxy sessions by audited commands that were executed. The details show which were these sessions.
Command: Name of the audited command that was executed;
Criticism: Criticism of command;
Sessions: Number of sessions in which the command was executed;
Sessions by command and device
Menu Behavior ➔ Occurrences ➔ Device.
Ranking of proxy sessions by audited commands that were executed on which devices and what credential was used. The breakdown shows which were these sessions.
Command: Name of the audited command that was executed;
Remote device: Target device of the command;
Sessions: Number of sessions in which the command was executed;
Sessions by command and credential
Menu Behavior ➔ Occurrences ➔ Credential.
Ranking of proxy sessions by audited commands that were executed and on which devices were executed and which credential was used. The detail shows what those sessions were.
Command: Name of the audited command that was executed;
Action during session: Action that was taken according to the registration of the audited command;
Remote device: Target device of the command;
Credential: Credential that was used;
Sessions: Number of sessions in which the command was executed;
Sessions by command and local user
Menu Behavior ➔ Occurrences ➔ Local user.
Ranking of proxy sessions by audited commands, target device, credential used and which account was used. The detail shows what those sessions were.
Command: Name of the audited command that was executed;
Action during session: Action that was taken according to the registration of the audited command;
Remote device: Target device of the command;
Credential: Credential that was used;
Local User: senhasegura user account that made use of;
Sessions: Number of sessions in which the command was executed;