RDP Proxy
The senhasegura RDP Proxy is an RDP server running on the default port 3389. Its purpose is to perform the proxy between the operator user and the target RDP device.
Any device that offers the RDP protocol connection can be connected as long as it is aligned with the security levels.
Support for Windows RDP versions 5.2 and higher;
Support for Microsoft®Windows®2003 and higher;
Support for Linux XRDP servers versions 0.9.x and higher;
Support for RAIL session connection;
senhasegura authenticates on the target device using the native protocols of the requested session.
It is possible to specify how long a senhasegura session can be idle, that is, without any user interaction. In the Session inactivity time.
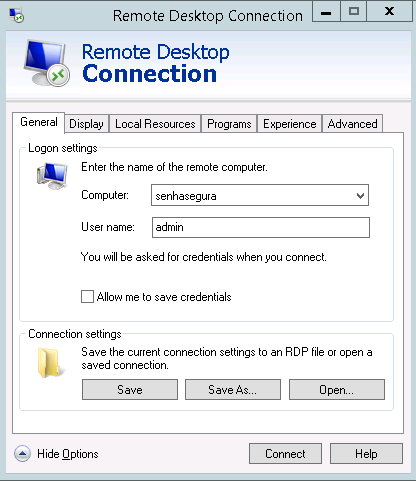
Connecting to a remote device
Using any RDP client, make a connection to the senhasegura server. Once connected to senhasegura RDP Proxy, you must fill the authentication data and the data of the remote device to connect.
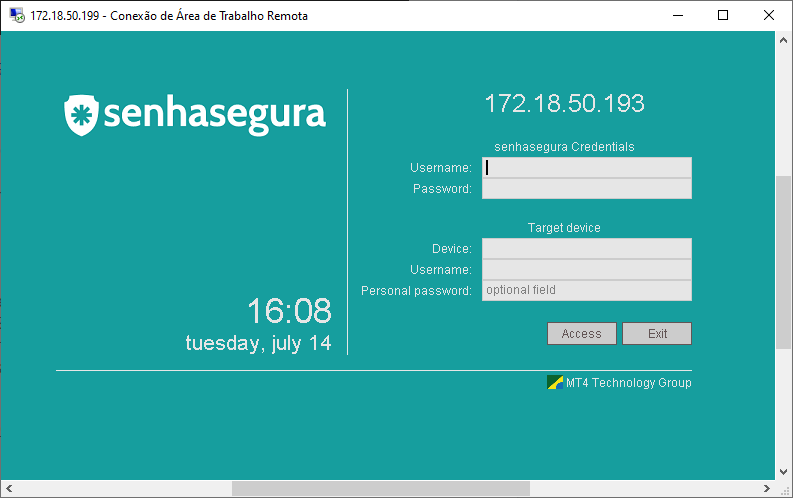
If the device accepts the use of personal credentials, provide the personal credential in the indicated field.
Access using Multihop
To facilitate access to the target device use a connection syntax that contains the destination access credential.
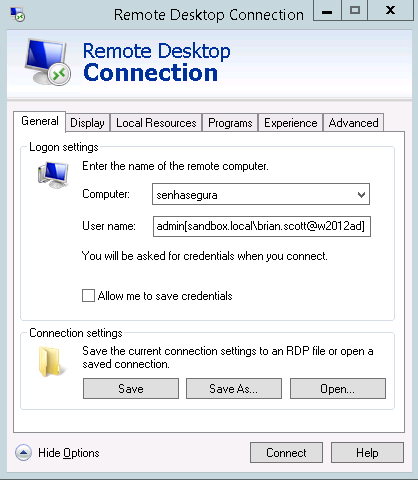
Take a look into its syntax variations, replacing the following strings with:
valtUser: senhasegura user
targetUser: credential you wish to use for access
domain: domain of the device to be accessed
device: device you want to access
Connection containing the user and device
valtUser[targetUser@device]
Connection containing the user, device and domain
valtUser[domain\targetUser@device]
Connection containing the user, device and access token
valtUser[domain\targetUser@device]token
Users with configured 2FA tokens will also be presented to the token prompt in the next step.
File transferring and clipboard area
senhasegura RDP Proxy uses the native RDP protocol, every shared resource between the client-side and the destination side will work as normal RDP connection even with the senhasegura monitoring layers.
File transfer must be enabled in the remote session parameters to work. Go to the Settings ➔System parameters ➔ System parameters ➔ Remote session menu and choose the Yes option in parameter *Enable File Transfer?**.
To transfer a file from the client-side to the target device, copy the desired file and paste it into a folder into the target device. senhasegura will then log this action and if any file transfer plugin is active, it will be triggered before the file reaches the target destination.
For text data stored at the clipboard area, the data will be logged at session indexed texts, but no plugin will be triggered.
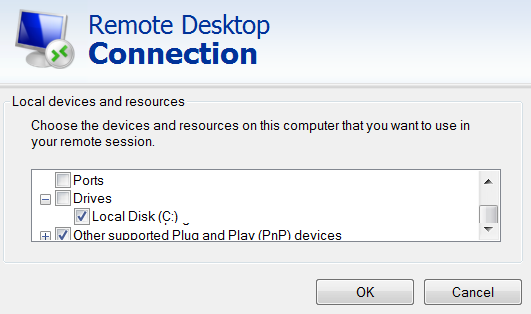
You can also transfer local resources to the target machine using the remote area connection of Microsoft® Windows®.
Interactivity blocking
If the administrator activates interactivity blocking, the operator user will be warned by a message in the upper corner.
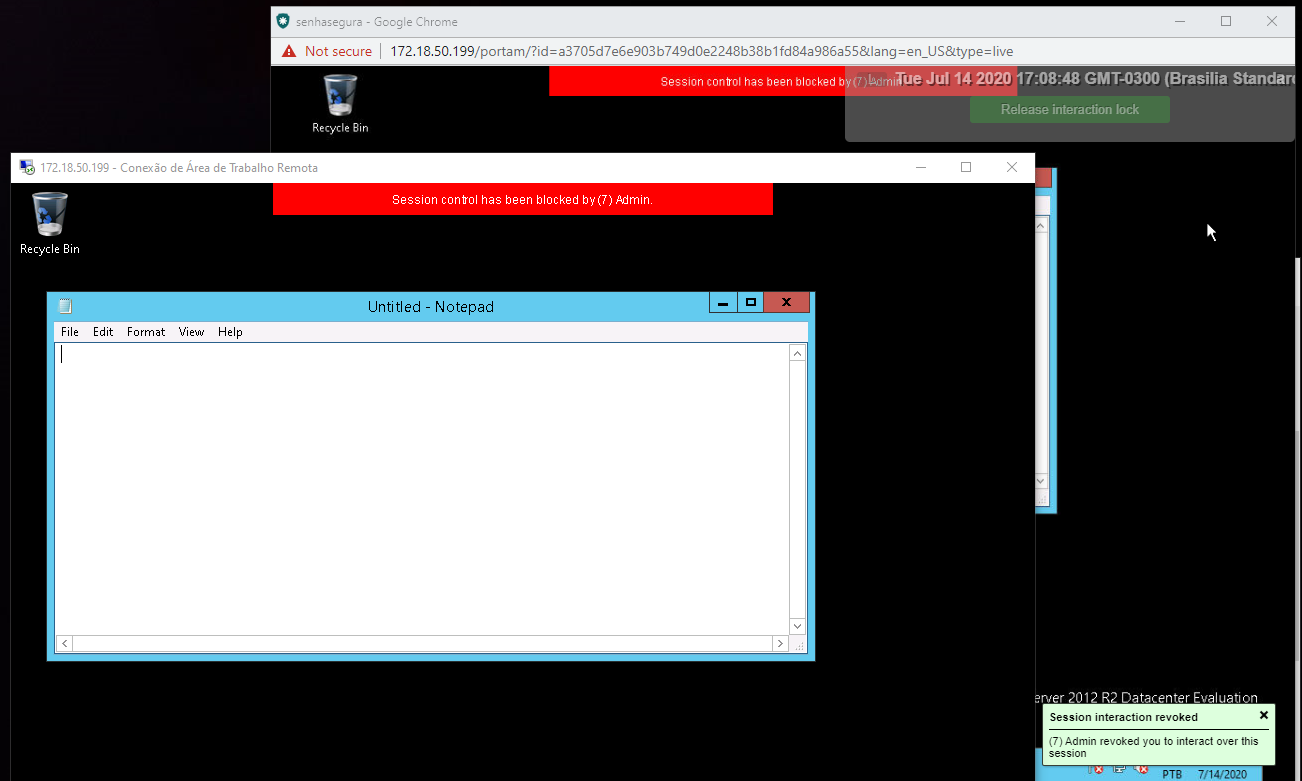
And if the administrator compulsorily terminates the session, the user is also warned.
