Proxy Settings Segregations
Because there are many settings in the global level definition, there is a need to segregate some of these settings to facilitate security policy management and possible exceptions on devices that do not support certain configurations.
For example, some RDP devices do not support the TLS security level, and must be isolated in a separate configuration if the global level is not configured in Automatic mode. Another example is Linux devices that by strategic decision, or technical limitations, do not support automated privilege elevation with SUDO.
To isolate these Devices and Credentials in segregated configurations, we must first understand the password segregation hierarchy.
Devices and credentials cannot be included in more than one segregated parameter.
The segregating layer has the option of keeping the current parameter unchanged. Therefore, there is no obligation to define all parameters for each layer.
Note that in the Color depth field, (which is displayed in all segregation layers) you can choose which color depth you want to use in VNCHTTP, VNCX11 and VNC sessions to suit the performance you want. The options range from 8 bits to 32 bits.
Segregation levels
Segregations respect hierarchy and rewriting order. Override system default settings, acting as a chain of adjustment layers where the next layer will always have the power to rewrite under the previous one:
- Global parameters
- Access groups segregated parameter
- Device segregated parameters
- Credential segregated parameters
- Parameters segregated by origin
Thus, a parameter defined in the Global layer can be overwritten by Access Group segregation, which in turn can be overwritten by Device segregation, and so on.
Through the module Settings ➔ System Parameters ➔ Segregated Parameters, you will have access to the creation of the segregated parameters and access to all segregations registered for proxy sessions. We must configure it following this step by step:
Segregation for Access Groups
Click on the Actions menu and choose New segregation for groups a new window will open called Parameter segregated access groups containing the tabs Remote Session, Recording, Security and Groups:
Name: Give your segregation a name.
Status: Define whether this segregation will be Active or Inactive.
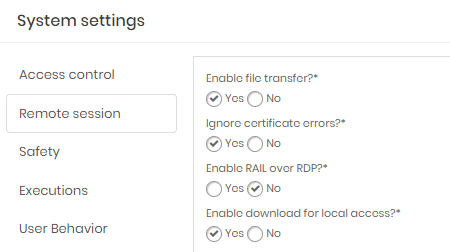
Remote Session Configure which type of remote session will be included in the segregation parameters in the groups and which will be enabled.
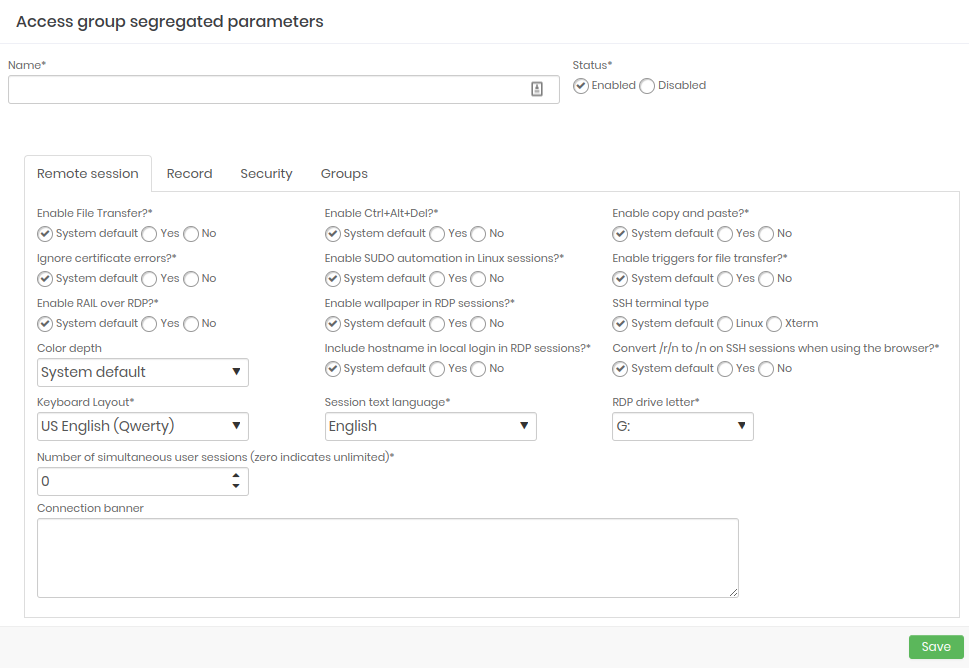
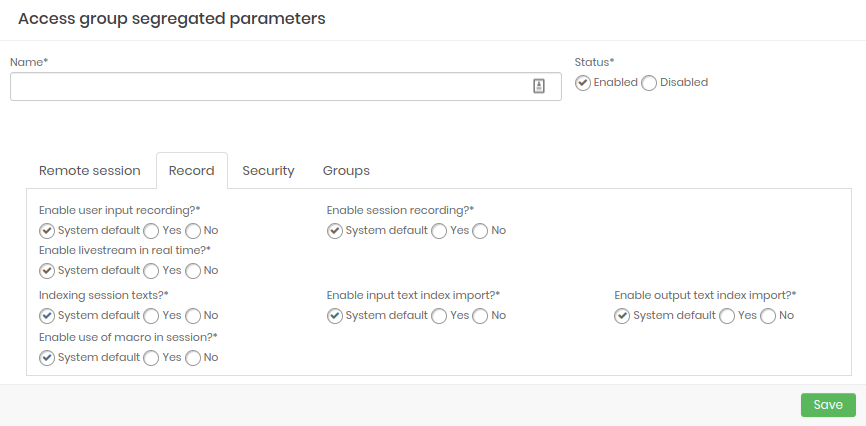
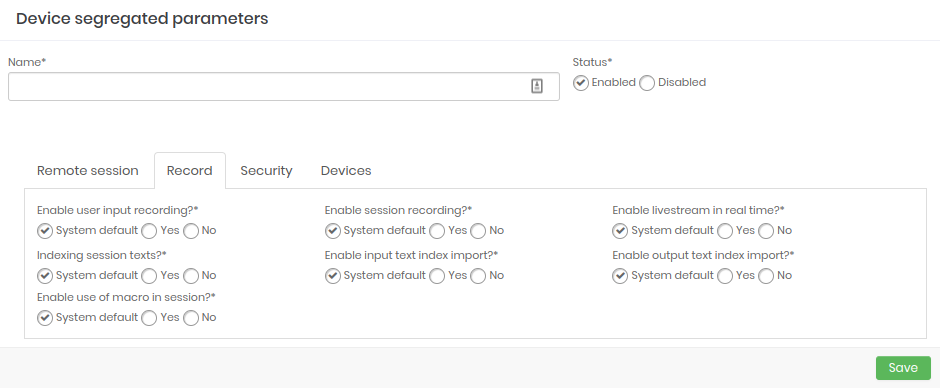
- Recording: Configure which parameters will be enabled when starting a session recording.
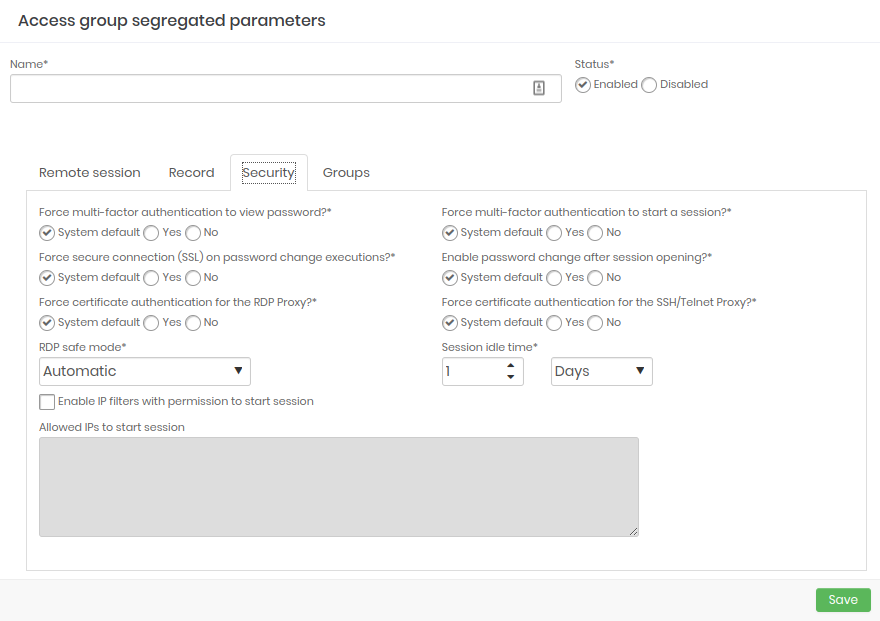
- Security: Configure the strength of the groups' security.
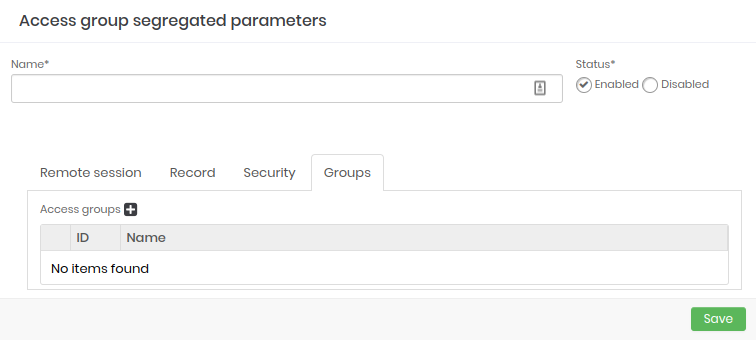
- Groups: Configure and add which access groups will be part of the segregation.
Device segregation
Click on the Actions menu and choose New segregation for devices a new window will open called Device segregated parameters containing the tabs Remote Session, Recording, Security and Devices:
- Name: Give your segregation a name.
- Status: Define whether this segregation will be Active or Inactive.
- Remote Session: Configure which type of remote session will be included in the segregation parameters on the devices and which will be enabled.
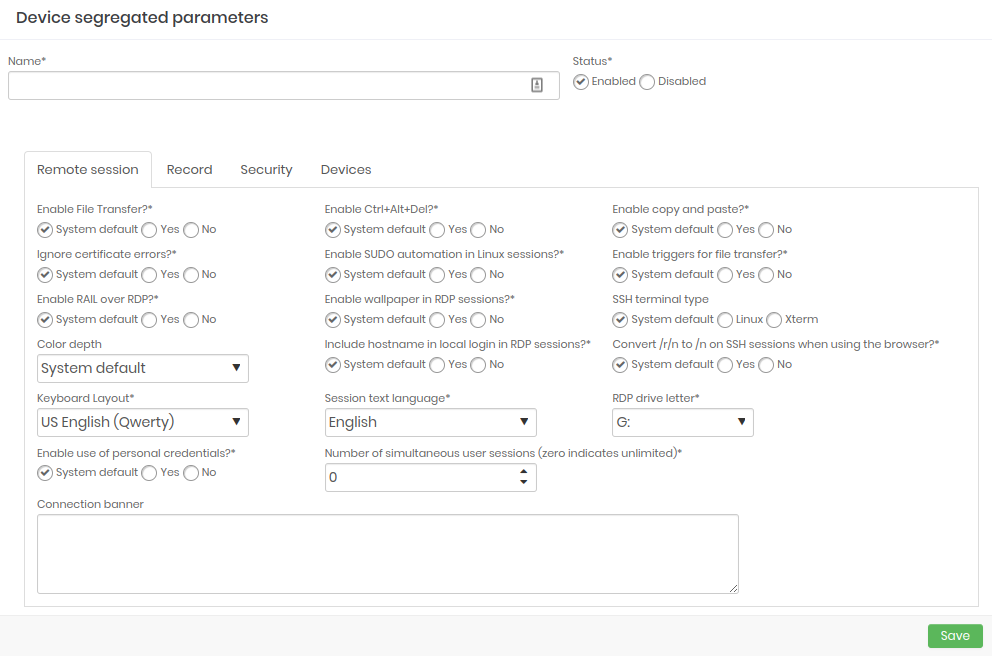
- Recording: Configure which parameters will be enabled when starting a session recording.
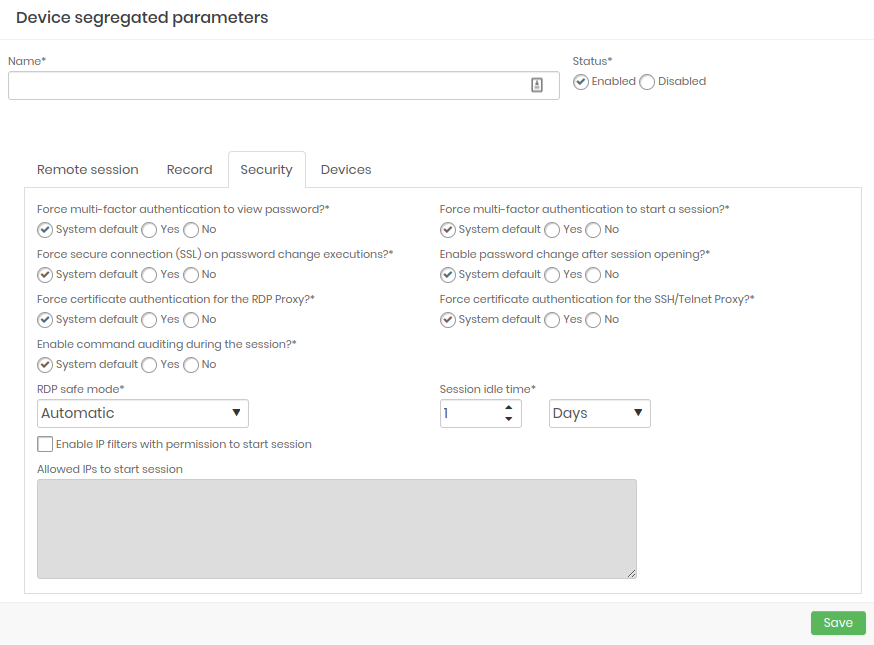
- Security: Configure the strength of security on devices.
Session inactivity time
It is possible to specify how long a senhasegura session can be idle, that is, without any user interaction. In the Session inactivity time field, define the amount and whether it is in minutes, hours or days.
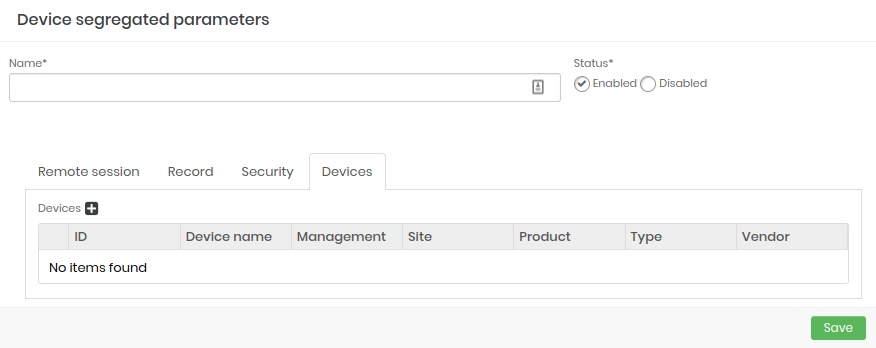
- Devices: Fill in an existing device in the system and add it.
Segregation for credentials
Click on the Actions menu and choose New segregation for credentials a new window will open called Credentials segregated parameters containing the tabs Remote Session, Recording, Security and Credential:
Name: Give your segregation a name. Status: Define whether this segregation will be Active or Inactive. Remote session: Configure what type of remote session will be included in the credential segregation parameters and what will be enabled.
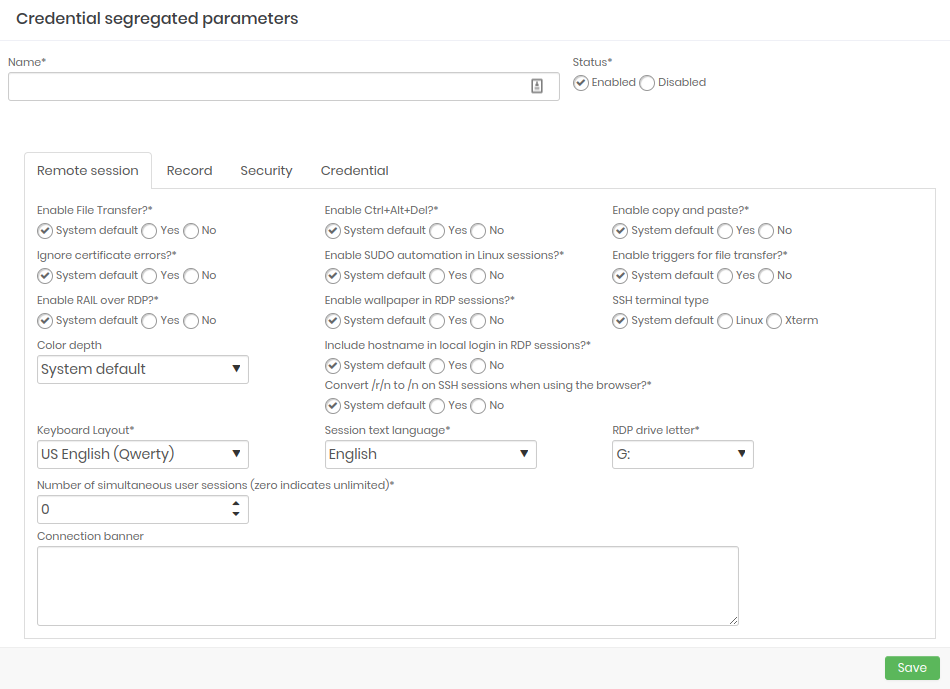
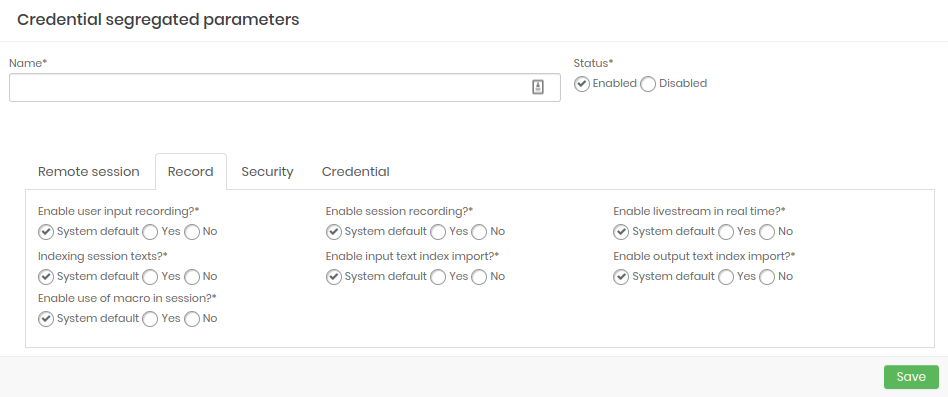
Recording: Configure which parameters will be enabled when starting a session recording.
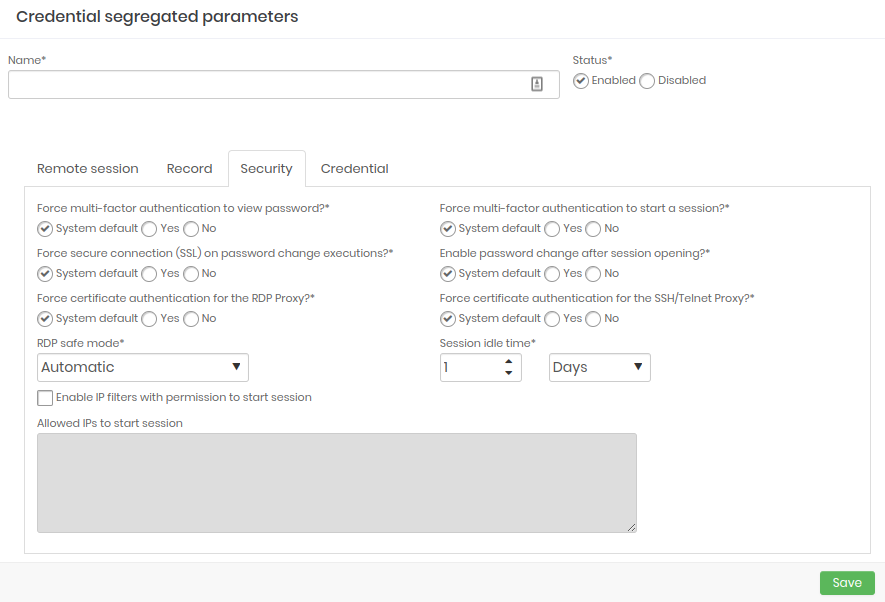
Security: Configure the strength of credential security.
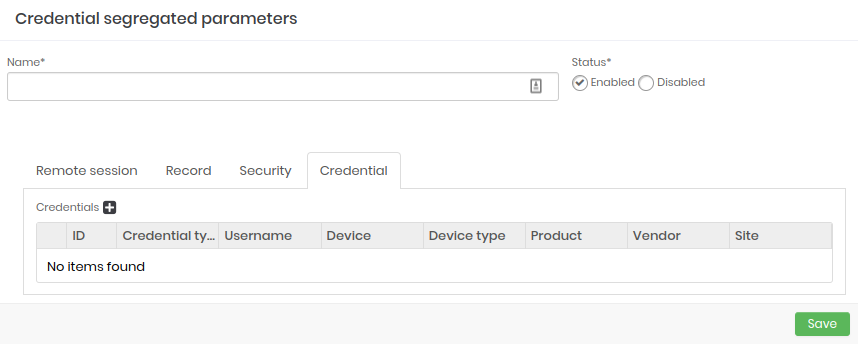
Credential: Configure and add which access credentials will be part of the segregation.
Segregation by origin
Click on the Actions menu and choose New segregation by origin a new window will open called Parameters segregated by origin containing the tabs Remote Session, Recording, Security and Origins:
- Name: Give your segregation a name.
- Status: Define whether this segregation will be Active or Inactive.
- Remote session: Configure which type of remote session will be included in the segregation parameters at source and which will be enabled.
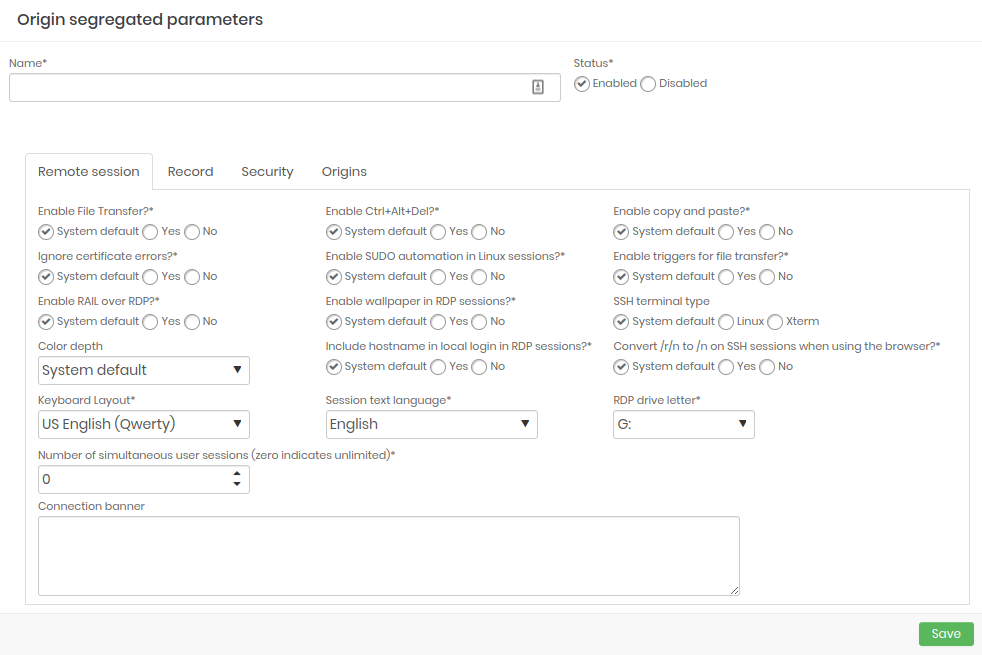
- Recording: Configure which parameters will be enabled when starting a session recording.
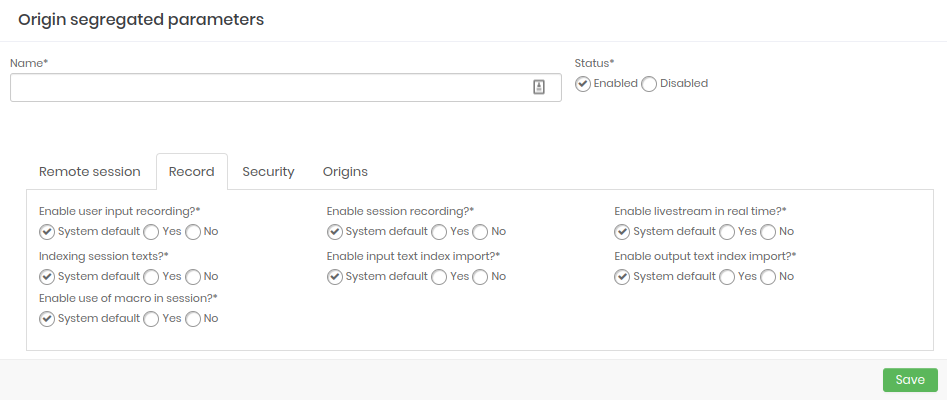
- Security: Configure what the security strength will be at the origin.
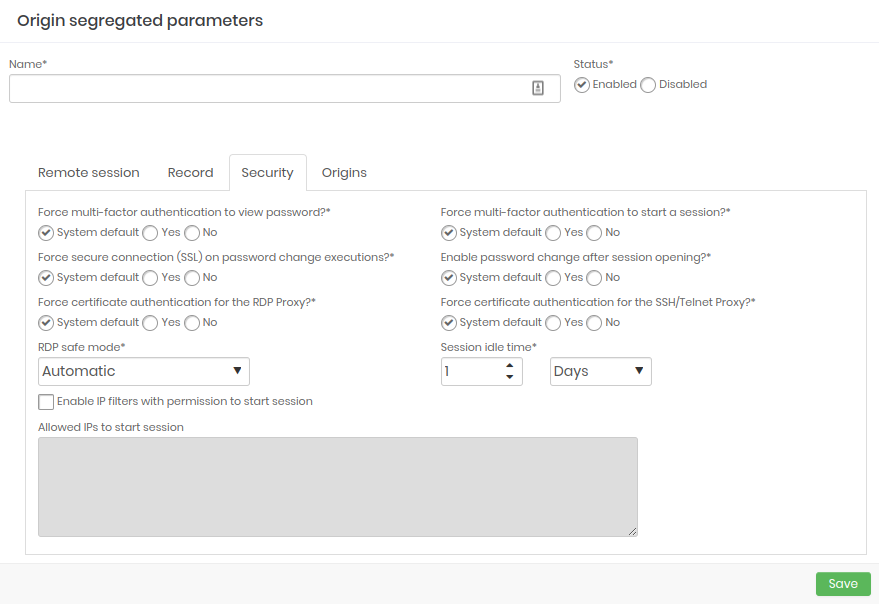
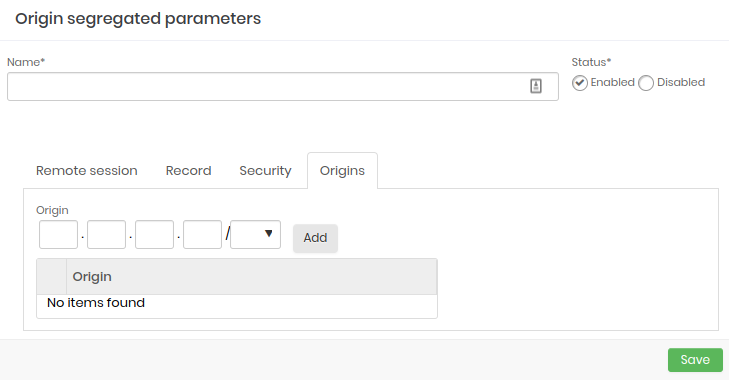
- Origins: Configure and add which access sources will be part of segregation.
With each proxy session, senhasegura will always frame the requester to an Access Group that allows the use of a Device Credential. And this user always starts from a source workstation. Hence, senhasegura will always be able to determine an appropriate combination of parameters for this session.
The image proxy-100 shows that the Global setting allows file transfer.
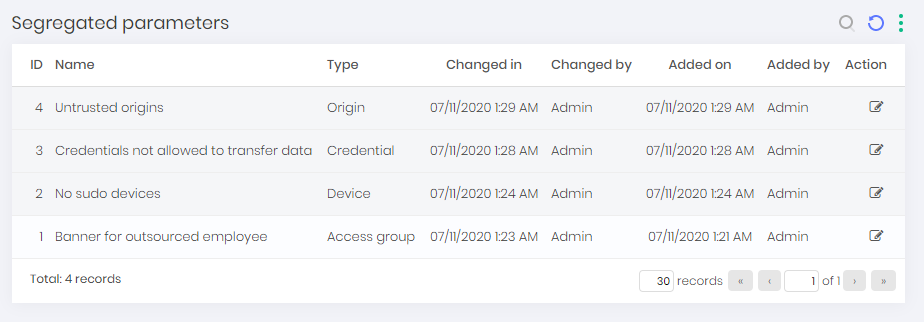
The image proxy-110 demonstrates that there are segregations for all layers, and each segregation has a name that makes clear the intention to use.
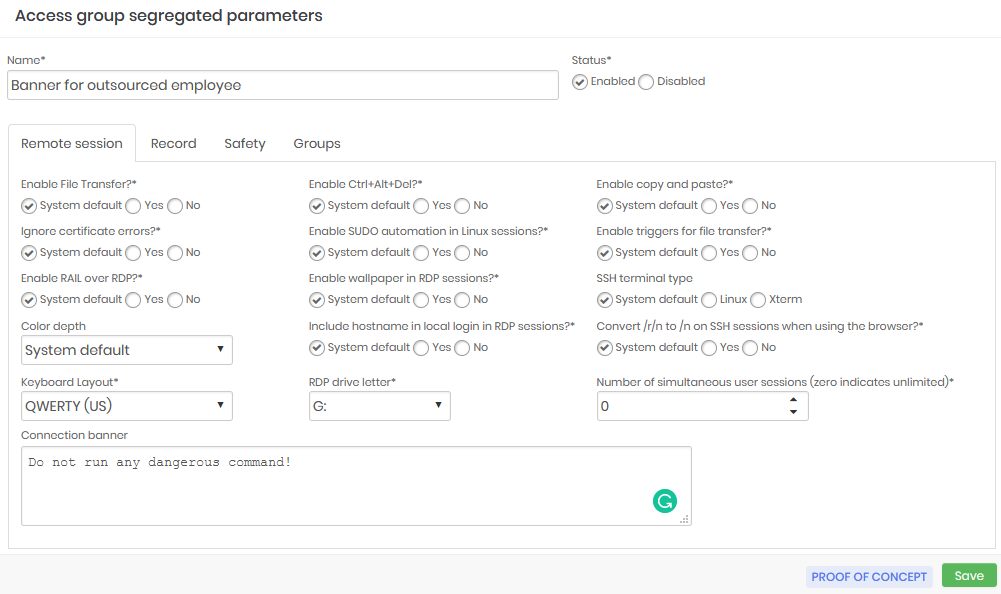
The banner segregation example kept all other parameters unchanged. Only the banner has been set.
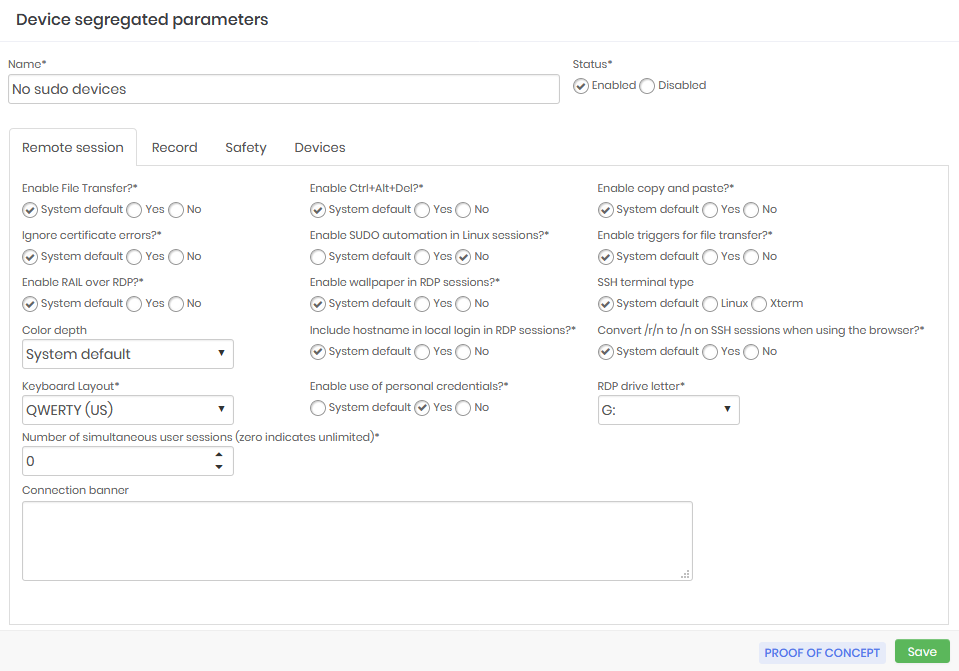
Device segregation example inactivated automated privilege elevation execution and allowed the use of personal credentials.
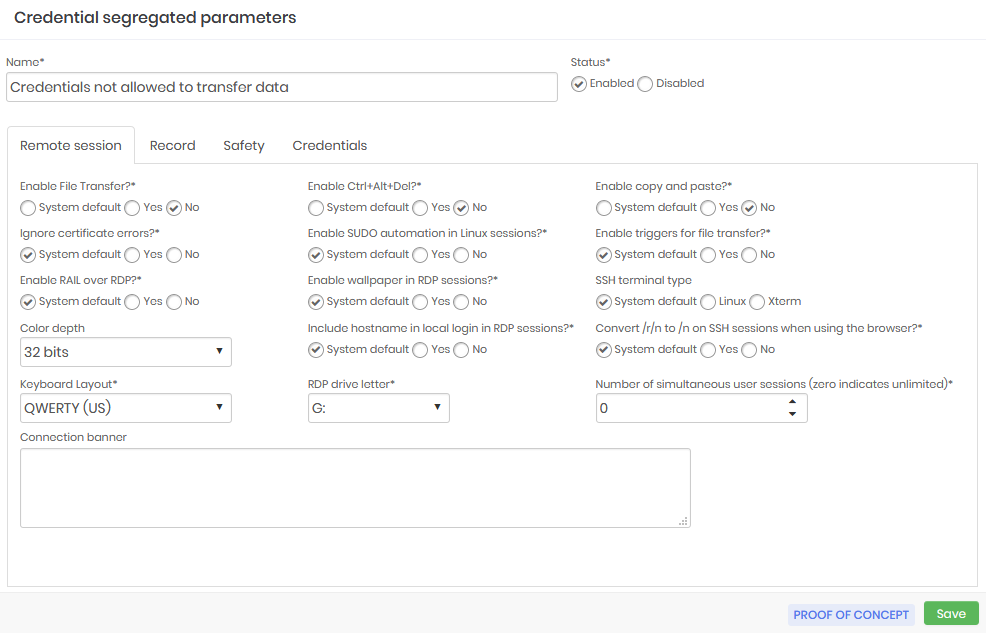
The credential segregation example does not allow file transfer, clipboard use, and does not allow the use of <Ctrl+Alt+Del> key combination.
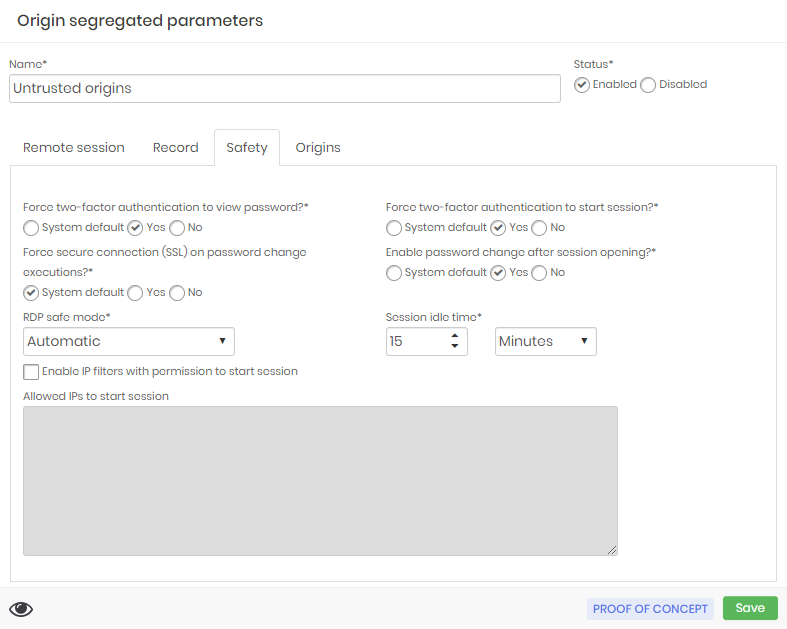
Source segregation example is forcing the use of the 2FA to view passwords and start proxy sessions and allows immediate password recycle after the proxy session is opened.
Note that there is a possibility that a session may have to consider some of these rules, all, or none at all. Making the configuration possibilities very flexible.