GO Endpoint agent
The senhasegura.go can be customized. The image displayed and the description of the items may vary from version to version, or on the administrator's decision to release some features to users or not.
In the header, you can see the default credential selected by the user along with the domain. This default credential will be used for privilege elevation actions inside and outside of the senhasegura.go interface.
In case the standard credential does not have any registered domain, the machine name will be shown in its place.
If active, you have the offline options of senhasegura.go and the single sign-on shortcut (SSO) to the web portal. We will explain this functionality further below.
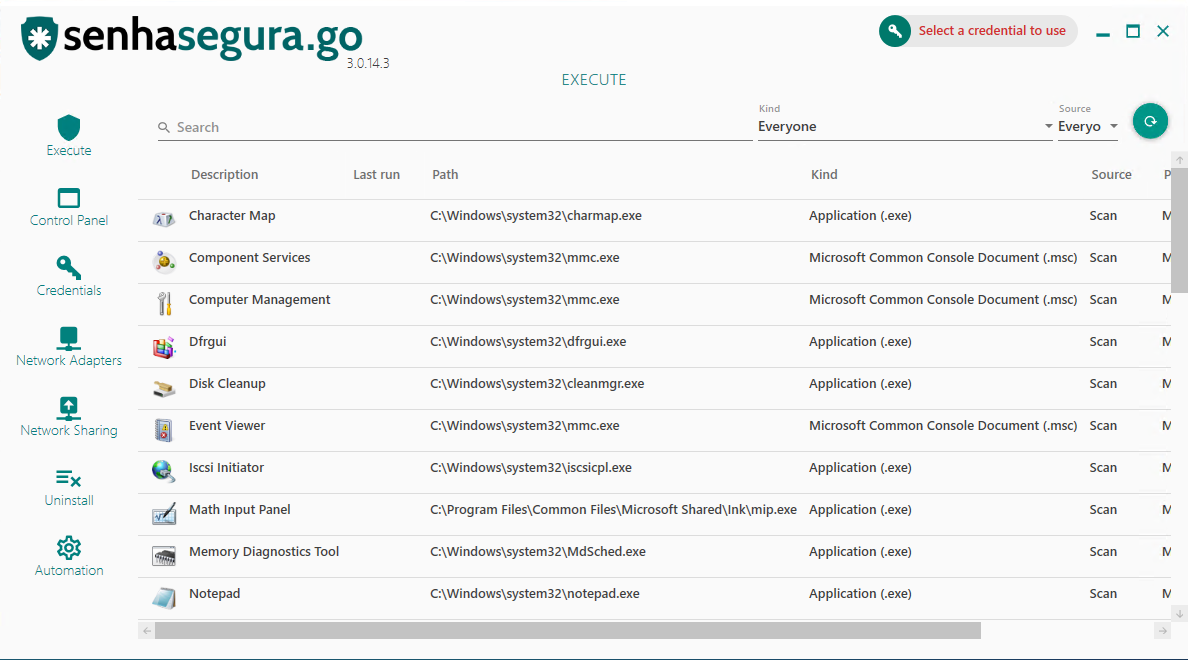
In the left sidebar, you have access to the submodules of senhasegura.go.
Execute: General application privilege elevation;
Control Panel: Privilege elevation for control panel applets;
Credentials: The application certification has a fixed value called Trusted Only, in a way that the certificate that has this rule will be validated;
Network adapters: List of workstation network interfaces. The administration of these interfaces is performed in this sub-module, not by the Control Panel;
Network sharing: Shared network directories used by the user. The credentials will be used to access the directory without the need for exposure or mapping;
Uninstall: Applications available for workstation uninstall;
Automation: Automation macros made available to the user by the administrator;
For each sub-module, the central area will display its listing and provide filter fields above its header.
Using credentials
Users of senhasegura.go will always be linked to the account used to log in to Windows.
this Windows username must have an equivalent user in the senhasegura , as presented in the installation activation process.
This senhasegura user account is passive to all access group controls. That is, users can use the access workflow, emergency access, and credential segregation.
Therefore, if the user depends on an approval process to view or use a credential, this rule also applies to the use of the credential by senhasegura.go .
From senhasegura.go you can make use of the credential, view, or copy your password. These actions are equivalent to proxy use, viewing, or copying via the web interface. All these actions will be audited and forwarded via SIEM.
Performing an elevation of privilege
There are several ways to perform a privilege elevation, each has a different approach on how to perform the elevation. They are:
Elevation through access tokens;
Elevation through group memberships. For each elevation type, we also have JIT access.
The global parameter will be defined as the approval workflow pattern for all applications that do not have a configuration within an access list.
In GO Endpoint Manager ➔ Settings ➔ Parameters:
Workflow
Workflow settings
Check box options select which of these options you want to apply:
- User can elevate applications
- Requires justification to elevate applications
- Requires approval to elevate applications
Options to define the Amount of Pass or Fail:
- Approvals required
- Disapprovals required to cancel
Check box options select which of these options you want to apply:
- Allow emergency access
- Level approval
Workflow Approvers
On the GO Endpoint Manager ➔ Settings ➔ Approvers, it's possible to manage and create new approvers for Endpoint Manager. Any approver here will be a global approver for any rule that requires approval to elevate applications with the Endpoint agent.
Access request settings
Must specify governance code when justifying?*
Select whether Yes or No
Always add user manager to approvers?*
Select whether Yes or No
Elevating an application from the list
In the Execute sub-module there is a list of applications available for elevation. This list is initially formed by a scan of applications from the start menu. Therefore, not all applications will be present.
The refresh button located in the top right corner of the list will make a new search to start for new applications.
If an application is not present on the list, you can drag its shortcut or execution binary into the list. EXE, LNK, MSC and MSI files are accepted as executable. Locating the desired application, just double-click on its register to start the elevation. Another way is to right click under the registration and choose the way to run the application.
Run as with privileges: Will run the application with elevated privileges within a dedicated session of the selected credential;
Execute: Will only run the application within a dedicated session of the selected credential;
When running the application, notice that the applied theme differs from the logged-in user. This occurs because the application is being executed in another profile. You can validate.
Elevating an application outside senhasegura.go
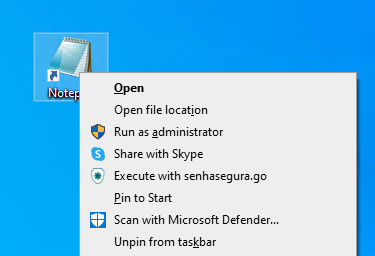
All the executable application or shortcuts have in their context menu an action "Execute with senhasegura.go ". With this action, you can run an application, if the credential has been selected previously. In case there isn't a selected credential, you'll be alerted to select one.
In these cases, the elevation that will be used is Run as with privileges, which the application runs with all the administrative privileges.
Elevating privileges for Control Panel applets
In the sub-module Control Panel you'll have access to the available applets on the Control Panel. All the available applets allow the elevation as much as the applications.
Till the version 3.0.14, by a technical limitation, isn't possible to perform a session recording of the control panel applets. However, the auditing use is registered on senhasegura .
Managing network interfaces
In the Network adapters sub-module you will see the list of network interfaces available for configuration.
The principle is the same as the Control Panel applets. By double-clicking or accessing the context menu of the registry, you have access to the settings panel of the network interface.
Till the version 3.0.14, due to a technical limitation, session recording for network interface applets is still not possible. However, the usage audit is registered in senhasegura .
Access to shared folders
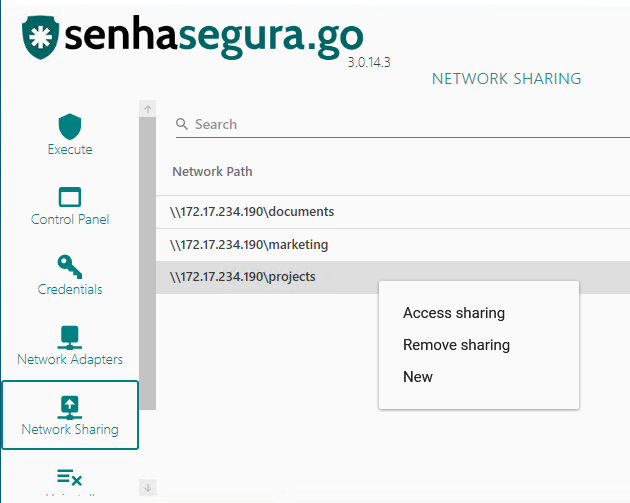
On the sub-module Network Sharing the user can access a network shared folder using the selected credential. This credential doesn't necessarily be a domain credential.
The folders accessed through senhasegura.go are registered, and can be accessed again because of the credential cache managed by Windows. These folders won't be mapped as a unit.
Folders accessed previously can be removed from the list through the option Remove sharing of the same context menu.
To add a new folder, click on the right button and choose the option New from the context menu.
Once authenticated the access to the folder, Windows can create a local cache with the network access allowing the folder to be accessed without using senhasegura.go . The main purpose of senhasegura.go is to automate this access without showing the password to the user.
Uninstalling Applications
The uninstallation of applications is performed by the Uninstall sub-module. In this sub-module the list of installed applications will be displayed.
To uninstall an application, have a privileged credential selected and right-click on its registration and select the action Uninstall in its context menu.
At this point, you have been presented to the main features of senhasegura.go .
There are also several features to explore, but before we can understand them we will learn a little more about the reports on the web platform and next we talk about the senhasegura.go advanced features.
Synchronizing Policies and Credentials
Policy and credential changes that occur on the senhasegura server will be automatically updated in the senhasegura.go interface through its services every 5 minutes.
Sometimes it may be necessary for this update to be immediate. Then the senhasegura.go user can choose to click on the systemtray icon and select the Update credentials or Synchronize policies options.