Domum
Introduction
This book will explain how to use, manage and analyze the data and functionality of Domum.
Symbols used in this cookbook
This book uses the following symbols to highlight information that should be taken into account for the best use of senhasegura :
Info - useful information that can make the use of the solution more dynamic
Caution - actions and items that cannot be ignored
commands: data that must be entered in the same way as described in this book- URLs : paths to access web pages.
<KEYS>: keyboard paths that will be used to perform actions.
Purpose
The Domum module is a "Remote Privileged Access" solution that offers the possibility for external hosts to gain access to an organization's internal resources, as well as providing a more secure home office environment for all of the organization's devices, controlling access by third parties and customers.
Without this kind of control and monitoring, one of the potential risks that organizations are vulnerable to is unauthorized access to enterprise resources, as a compromised server, for example, could be used to intercept communications and be a point of attack for other hosts within the organization.
Domum not only provides a secure external access for the organization but also an easy and fast procedure to grant external access to third-party users and employees because it is a VPN-Less solution, that is, the organization will not need to worry about setting up networks and VPNs for each user that needs to access the secure network from an external network, just configure their permissions in an access policy and give them a dedicated link for access.
That said, Domum can assist an organization in the following scenarios:
User origin management
Definition of remote access policies separate from other PAM users
Secure authentication with a dedicated link and token requirement
Visibility of remote activities
IT (Just In Time) accesses for third parties
Flexibility and possibility to expand operations around the world with governance through geolocation
Check out Domum's architecture below and, consequently, who the external hosts are and how access is made:
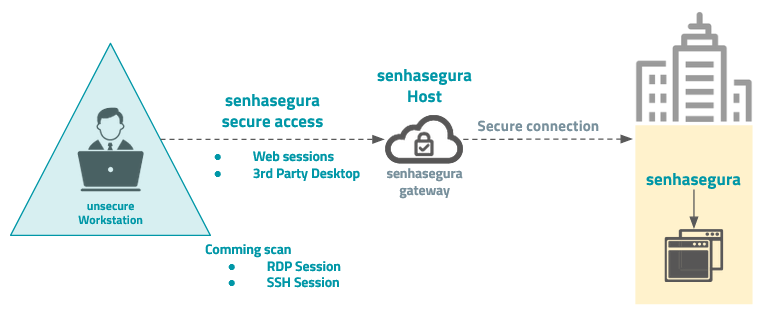
As presented above, Domum, through senhasegura , will provide secure access to Web sessions coming from third-party desktops, which in turn will connect to the senhasegura gateway1 through the HTTPS protocol without the need for VPN, which will then secure and provide access to the organization's internal resources.
In the Domum module, organizations can create their own Privileged Remote Access rules and execute and monitor them according to the needs of their respective operations.
The figure below demonstrates how different organizations can use the Host senhasegura to reach their institutional senhasegura instances, without any conflict between the gateways.
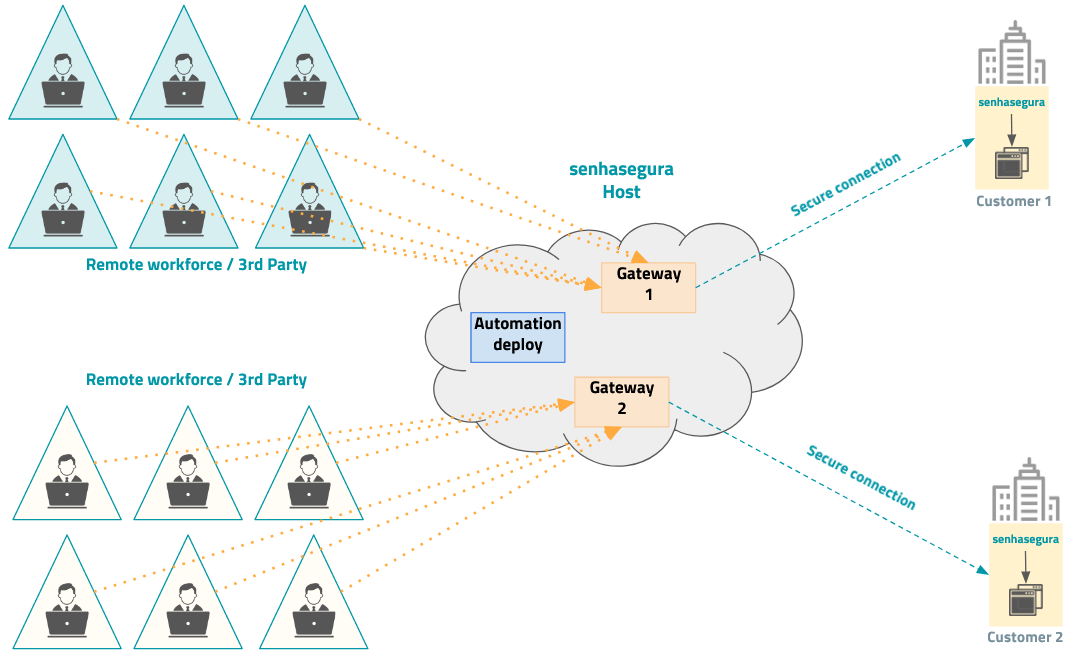
Players
Check below the main advantages for the main types of users:
User Administrator
Only one gateway to configure access to the senhasegura , instead of multiple VPN configurations for each remote user
Central monitoring of external access logs performed by third-party users and employees
Dashboard to assist a vendor KPI Analysis
Segregation of access management for third-party users and employees
Management of all allowed accesses for remote users
Real-time monitoring of all sessions in use
Video recording of the session
User behaviour
Logs
Restrictions by location
Remote User
No need to configure VPN (VPN-Less)
No Agent installation required (agentless)
No password required. Use of dedicated token.
Works from anywhere as long as it is allowed by the administrator
Proxy Session through Web Browsers
Unique desktop screen with all necessary information
Auditor
Dashboard with an overview of all the accesses made to Domum and the activities performed through it
Dashboards segregated by Vendor, specific Third Party User, Employee Group and specific Employee.
Third-party user and employee access logs to determine if permissions and credentials have been granted as determined in the external access policy
Remote sessions held through Domum, recorded and with the possibility of downloading the video file for auditing
Use cases
This section brings together the concepts presented in the previous sections and exemplifies how they can be adopted by the organization as needed for its policy and operations. The section refers to operating models to help the organization determine what types of external access approaches can be implemented. The approaches are as follows:
Third-party users: With the organizational network being such a critical asset, it is not ideal to grant external users access to it when their activities are restricted to only using the senhasegura . Even using methods such as VPN is still difficult to control and restrict access to just a few applications.
VPN-Less and Principle of Least Privilege: this type of user can have his access restricted to the Domum platform only, without ever having to be registered with senhasegura , receiving a link dedicated to his user for access to the platform. He will be able to visualize passwords and carry out remote access to the credentials assigned to him while working from home, from his own company's space or even from the organization where he provides his service, in an isolated manner from the network where the senhasegura is operating, using an access profile of an external user and minimal privileges.
External Access Policy: the organization must configure which assets the user must access and how this access can be carried out respecting the days and times determined in the policy.
Geo-location Blocking: Using the policy the organization can determine from which locations the request for access to Domum will be considered a secure request. For example, the access permission can be restricted only to the regions of the partner company where the third party user works and the organization where the user is providing the service. If the access to Domum comes from a region that is not authorized by the external access policy settings, the access will be blocked, regardless of whether the user has access permission or not.
Employees: this type of user may need access to the senhasegura to perform his activities when he is in working model that allows him to be outside his organization's premises, such as in his home environment or on a business trip. Users whose access to senhasegura is sufficient to perform their activities can be instructed to access the system through Domum, when they are not in the organizational environment, to save VPN resources, as well as restrict access only to the solution they need to use, senhasegura . In this way, the organization guarantees total access to your system through a safe and secure path, with a dedicated link that only that user can authenticate.
External Access Policy: employees of the organization that are performing their activities in an external network, the access group policies already applied in the PAM module are used during the access to the platform, ensuring that the policy already defined continues to be respected even in external access, i.e., when the user accesses the senhasegura through Domum the permissions and access group rules applied to his user remain the same.
Geo-location Blocking: Using the policy the organization can determine from which locations the request to use the Domum link will be considered a secure request. For example, the organization can determine that only the region where the employee lives or will travel for business are allowed regions. If the use comes from a region that is not authorized by the external access policy settings, the use of Domum will be blocked, regardless of whether this user has a registered user in the application and authentic permission.
Premises
For the Domum module to be used by the Administrator and the operator users, some premises must be met in the settings of the senhasegura .
Registering Access Reasons
For each credential release to a third-party user, the administrator must register the reason and the reason why he/she is granting the access. After installing Domum, the operations performed by the administrator must already be registered as a reason for access.
Domum Access Groups
The Domum module uses access groups that are separate from the other senhasegura access groups. To be able to register Vendors and third party users, the Domum access groups must already be registered.
Account for sending email
For the email containing the access link to be sent to the third-party users, the senhasegura instance must be configured with a default SMTP sending account.
If this account does not exist, the administrator will be presented with an error screen when trying to forward the access link.
To set up the default SMTP account, check the Orbit Web manual.
The senhasegura host provides an SMTP and SMS service for sending email and SMS to users. You can configure your instance to use these services.
SSO usage
Domum users' access configured by SSO login will only be possible using user and password.
The operator user will be able to log in using the SSO action in the corporative login screen and using user and password through Domun URL and in the corporative screen.
Features
The Domum workflow is quite simple and boils down to the administrator user defining and creating privileged remote access policies according to your company's needs. Domum will generate these accesses and they can be monitored and controlled by the Administrator. See below an example of the workflow and its respective steps:
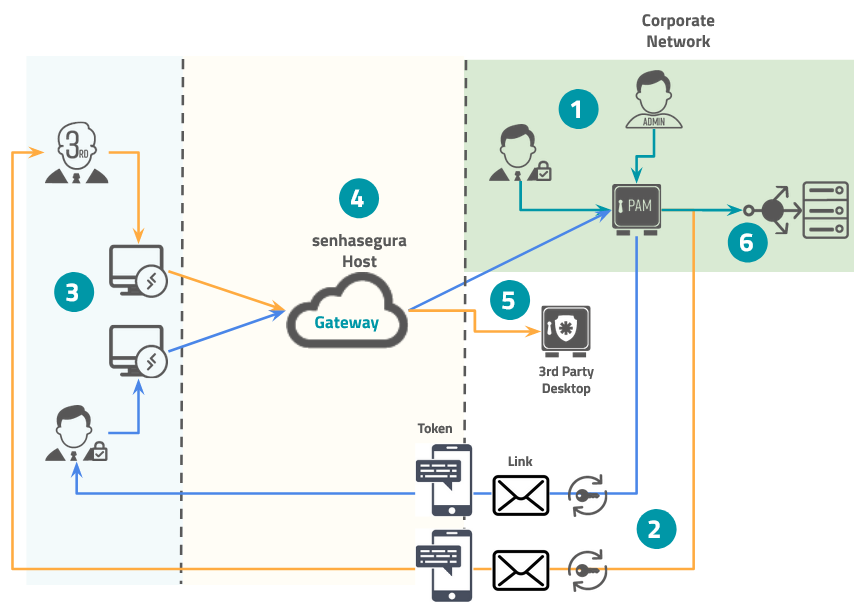
Administrator user defines and configures external accesses
The Domum will generate a personal link and a token via SMS or e-mail
The user accesses the link
The Domum Gateway communicates with the corporate environment
The user inserts the token received via SMS or e-mail to login
The user has authenticated access to the senhasegura where he can perform his operations
Administrator user
Before access can be granted to the external user, some settings need to be made within senhasegura by the System Administrator, which are:
Adjust the parameters
Create an access group for employees and third-party users
Register the vendor and third-party users
Register a reason why accesses should be granted
The following sections give a step-by-step example of how to implement these settings.
Domum Parameters
The basic functionalities of Domum can be seen at Domum ➔ Settings ➔ Parameters.
This screen will display the configuration parameters, use them as needed for your operations:
Employees domain: Domain that will be used for the employee access link
Third-parties domain: Domain that will be used for the thrid-party access link
Sending account: Indicates the e-mail account responsible for sending the external access link
Initial authentication token: By default email, indicates the way by which the first access token will be sent
To fill in the fields of the Gateway Configuration section, it will be necessary to previously perform the communication configuration between the instance and the Domum Gateway. Please check the Orbit Command Line manual to perform the steps of this configuration.
If you have changed any parameter, click on Save to make sure that the senhasegura admits the changes.
Upon successful completion of the configuration, the data will be automatically filled by an automation.
Registering a reason for access
The Administrator must keep track of the reason and rationale for granting the third-party user or employee access.
Go to the menu Domum ➔ Settings ➔ Access reason
In this report you can view all the reasons already registered, to register a new reason click on the button New.
Enter in the field, Name how the reason will be identified, for example: "Maintenance".
Click on Save.
The registered reason can be used for any third-party user or employee request, this record will be made available for all access request forms.
Creating an Access Group for Vendors
One of the first configurations that must be performed is the creation of an access group for the third-party users who performed the external accesses:
Go to the menu Domum ➔ Access Control ➔ Access Groups. On this screen, you will see the report of all the groups already created on the senhasegura and which types of permissions they are associated with. Click the New option.
cautionIt is important to remember that this group is not related to the access group of the PAM module, the settings determined in this form are independent.
In the field, Access group name enter a name for the group that is easy to identify, and if you wish write a short description of the group in the field, Description.
In the Settings tab, determine how this group should behave about to the password view permission:
Users can view a password: Determines that the credential password can be seen by the user;
Require approval to view a password: Check whether another user will need to act as an approver to see the password. Once active, you also need to define for how long this approval will be valid;
Approvals required for viewing: The number of approvals required to approve the operation;
Disapprovals required to cancel: The number of refusals to stop the operation;
Approval in levels: Check whether approvers will be triggered in tiers. This way you can define a hierarchy of approvers;
Also on the same tab, determine how this group should behave about the remote sessions permission:
Users can start session: Flag if member users are allowed to start a proxy session using the credentials that this group is allowed to access;
Require approval to start session: Flag whether another user will need to act as an approver to start the proxy session. Once active, you will also need to define how long this approval is valid for;
Approvals required: Number of approvals required to approve the operation;
Disapprovals required to cancel: Number of refusals to stop the operation;
Approval in levels: Flag whether the approvers will be triggered in tiers. This way you can define a hierarchy of approvers;
Then determine the Settings of the access request:
Governance ID required when justifying?: Flag if the applicant must enter an ITMS code at the time of justification;
Always add user manager to approvers?: Flag if the user responsible for the user's department should be automatically alerted as an additional approver to this group. Therefore, this user will be alerted together with the other approvers in the tab Approvers;
If you have determined that this group requires approvers, go to the Approvers tab. Note that approving users have a Level setting in their registry. This setting determines the calling sequence for approving the operation, allowing a hierarchy to be applied.
infoIf you are an approving user the requests from other users will be on the menu: Domum ➔ Access Control ➔ My Approvals. And if you are a user that needs approval you can view your requests in the menu: Domain ➔ Access Control ➔ My Requests.
To finish click on Save.
Registering Vendors and Third-Party Users
After you have created an access group for the third-party users and have registered an access reason, go to the menu Domum ➔ Settings ➔ Vendors and follow the instructions:
On this screen, you will see the report of all the vendors already registered at senhasegura , as well as the Contract Number, contract and other details. Click on the option New
In the field, Vendor enter the name of the vendor to be registered.
Then select the access group created earlier in the field, Access group.
If desired, enter in the fields Contract Number and Document ID, the contract data and document ID respectively.
Select in the field Start date the date on which the contract for granting access started.
In the Photo field, you can select an image to represent the vendor being registered. This image must be in format
.pngor.jpgand be up to 5MB in size. It will be presented in the Vendor Dashboard. (In the vendor report, click on the vendor registration action button and choose the Dashboard option to view).Go to the Location tab. On this tab determine if access from this provider's users will be considered legitimate if they originate from a particular location, this setting is not mandatory, but if it is your wish check the Restrict access to only those locations option.
- Select the Country and Region from which the accesses must originate to be considered secure, then click the Add button. You can define more than one location if you wish.
To finish click on Save.
With the vendor registration completed, you can register the user that is the service provider of this vendor, to do this go to the menu Domum ➔ Settings ➔ Third Party Users and follow the instructions:
On this screen, you will see the report of all third party users already registered at senhasegura , as well as which vendors they belong to and their contact data. Click on the option New
In the field, Vendor select the vendor you created earlier
Then, fill in the fields that refer to the user's personal data: Name, which will identify the user in the dashboards and reports, e-mail and Mobile phone, which will be how the senhasegura will send the access link to Domum, and the access token, in case the token is sent by SMS in the parameters.
cautionThis user must have a valid email account to receive the URL to access Domum. And a valid mobile phone number to receive the token, if the parameter for sending the token by SMS has been defined.
infoIt is recommended to use the SMS token sending parameter so that the access information is not concentrated in one place, making the process more secure.
In the Photo field, you can select an image to represent the user being registered, this image will be presented in his Dashboard. (In the third party users report, click on the action button of the user registration and choose the Dashboard option to view).
infoOn the Access tab you will get a report of all access requests for this user.
Click on Save to finish
Creating an Access Group for Employees
As previously stated, it is possible to grant access to Domum to employees in your company who already have access to senhasegura , but because of a scenario, for example, remote work or a business trip, they may need to perform their activities from an external network.
As Domum grants access to the senhasegura remotely and safely, it is possible to deliver to the employees an access link to Domum without the need to create a new user for them or to configure an external access group, since the secure login delivers to the employee the common access to the secure login that he usually has in the organizational environment, respecting the permission and the access group with which he is already registered.
Remember that accessing the senhasegura within the organizational environment using the company network will not have any change, the user will access the senhasegura as usual. However, when using external networks and being physically in a place away from your organization, you must use the Domum access link if you wish to use the senhasegura .
To grant the employee access, you must first create an employee group, this group will not configure permissions for viewing passwords or remote sessions, only allow authorized locations to be indicated for the origin of access for users who are members of this group. The access settings are the same as the access group configured in the PAM module, and other modules that the user uses, to which he belongs. To create an employee group go to the menu: Domum ➔ Settings ➔ Employee group and follow the instructions:
When you access this menu you will be presented with a report with the list of employee groups already created. Click on the button New to register a group of employees.
Enter the Group Name, this name will be used to identify the group for granting employee access and in access reports, session and dashboards.
Then click on the addition icon and select the users that will be part of this group. This action does not mean that the user can already receive the Domum access link, adding a user to the group only indicates that he must respect the group rules. It is through the employee group field, on the employee access consent form that users will be displayed for granting access, so include in the group everyone who may now or in the future receive access to Domum.
cautionThe users added to the group must have an e-mail address registered at the senhasegura for the Domum access link to be sent.
Go to the Location tab. In this tab determine if access from this provider's users will be considered legitimate if they originate from a certain location, this setting is not mandatory, but if it is your wish check the Restrict access to only those locations option.
- Select the country and region from which the accesses must originate to be considered secure, then click the Add button. You can define more than one location if you wish.
To finish click on Save.
Granting First Access
In the next steps the senhasegura will send emails and SMS messages to notify users. The email and SMS sending service must already been configured as we mentioned in the premises.
If the error "you will need to set up an SMTP account on senhasegura ." occurs, refer to the Orbit Web Interface manual to set up an email sending account.
Granting Access to Third-Party Users
After making the first settings you will be able to grant access to the already registered third party user. To grant access, go to the menu Domum ➔ Settings ➔ Third Party Users and find among the records the user to whom you want to grant access.
Click on the user registration action button and choose the Request Access option
In the general tab, describe in the field, Justification why you are requesting this access for the user.
Choose in the field, Reason, one of the previously registered motives.
On the Credentials tab, add the credentials that the user can access.
Go to the Access limitation tab and set the Access permission period:
Start: Date and time when access can now be granted
Duration: Value and time parameter (minutes, hours, days and months) that the access will remain valid.
Access permission days: Mark the days of the week that the access can be made
Access permission times: Check the periods that the access can be performed
Sessions: Check whether the sessions can be unlimited, i.e. can be done more than once, if not determine the maximum number of sessions.
To finish click on Save.
You can grant access also via the remote access screen and follow the instructions above: Domum ➔ Remote access ➔ Third-party access. Click on the report action button, under the New option, select the Vendor and the User, and click Next.
With this simply send the email containing the Domum access URL to this user, then go to the menu: Domum ➔ Remote Access ➔ Third-party access.
In this report find the record for the user you want to grant access to and click the action button and the Send Access URL option.
The third-party user will receive the link to access Domum in his e-mail address or SMS according to what has been configured.
Granting Access to Employee Users
With the employee, group created you can grant access to an employee by following the menu: Domum ➔ Remote Access ➔ Employees. In this report, you can see the list of employees who have already been granted access and even those with terminated access. To grant access follow these instructions:
Click the New button
Select the Employee group, created earlier, then select the User member of this group you wish to grant access to. Remember that only users who are members of the selected group will be available for selection.
In the Justification field, describe why remote access is being granted to this employee. This justification can be viewed in the user's access details.
Then select a Reason for granting this access.
Go to the Access limitation In this tab you should indicate how long this access will be valid. In the field, Start enter the date and time that the access will start to be valid, in the field, Duration enter a value and a duration metric (minutes, hours, days or months) for the access. Remember that the duration will be calculated from the date and time entered in the Start field.
To finish click on Save.
With that done go to the Domum ➔ Remote Access ➔ Employees menu. In this report find the record for the user you want to grant access to and click the action button and the Send Access URL option. The employee will receive the link to access Domum in his e-mail address or SMS according to what has been configured.
Receiving the Access URL
After granting access to the third party or employee user, they will receive in his/her e-mail (the e-mail address informed in the user registration form) the access link to the Domum platform.
It is important to remember that this link is for the exclusive use of the user who received it, it should not be shared with other users as this may result in a breach of confidentiality and the principle of least privilege.
A few seconds after receiving the e-mail the user will also receive the token for the first access to the platform. The token will be sent by e-mail or SMS, depends on the token parameter configured previously.
Employees will not receive the access token, their authentication will be done through their common access credentials. after successful authentication, the registration of an OTP token will be requested.
The Domum module does not support SSO authentication.
Click on the link or copy and paste it into your browser, insert the token provided. After the authentication is successfully done, the user will have to register a new Token OTP that will be required in all his accesses. If you enter the wrong token and the screen displays an error message automatically a new token will be sent to the user.
With the registration of the token complete, the user will be presented with the Domum interface which consists of a report with all the credentials he has been granted for remote sessions and password views, all according to the policy of the group this user belongs to.
For employees, after authentication, the senhasegura platform will be displayed, and the user will be able to use the modules and functionalities he already uses in the organizational environment, normally, according to his user permission and the access group he belongs to in each module.
In addition to the password view and start remote session actions, you can also check details such as days and times that access is allowed, the maximum number of sessions that can be done, as well as the list of credentials held by the user and the last accesses, performed.
Third user
When accessing Domum the third party user will see a report with a list of all the credentials, which were granted to him by the administrator.
This report will display the action buttons for viewing a credential's password or starting a remote session on a device.
Besides, a list will be available for the user to check which credentials are in his custody, and another list with the remote sessions held by him.
Panic button
This feature is intended to help administrators to take quick defensive action in times of incidents.
Using the Panic Button action button, the administrator will revoke all ongoing and future accesses to a Vendor.
If third-party users are using Domum to perform remote access or viewing a credential, they will immediately be logged out. Those who already have access but are not currently using it will not access Domum after this action.
Access: Domum ➔ Settings ➔ Vendors.
Search for the Vendor you want to revoke the accesses and click on the action button Panic Button. Be careful! Because all users associated with the provider where the Panic Button is triggered will lose their access to Domum. For the third-party users to regain access the administrator must request a new access for each of the users.
Batch import third-party
You can use batch import to speed up the registration of third-party users.
Some important points about this batch import:
The import is based on an Excel spreadsheet;
The purpose of this worksheet is to add new third-party users;
The vendor that the user is associated with must already be registered in the senhasegura ;
Third-party users who are already registered will not be updated.
The Excel template file is available on the same screen where you can import the completed file. Go to the menuDomum ➔ Settings ➔ Batch import third-party to access the imported file report.
Clique no botão do ação do relatório Importar.
In this form, click on the footer option Template file to download the template file.
Filling in the template file
Vendor: Name of the company responsible for the user to be added. Remember that this vendor must be already registered in the senhasegura .
Name: Identification of the third-party user to be added;
Email: E-mail address of the third-party user, to which the access link will be sent;
Phone: Telephone number of the third party user where the SMS with the access token can be sent;
Document: Identification document of the third-party user;
Enabled: Indicates if when the user is added to the senhasegura it will already be active or not..
After filling in the file, return to the form where you got the spreadsheet and load the file and click on Import data.
You can track the import process, status and time, in the third-party batch import report.
Audit
In this chapter, we will cover how to audit and observe dashboards of the accesses and entities registered in the senhasegura .
Dashboard
Monitoring Center
This dashboard shows an overview of Domum usage by vendors and third-party users, employees and their access groups. Go to the menu: Dashboards ➔ Monitoring Center. This dashboard will display blocks of information such as:
Use the filter in the upper right corner of the screen to see information relating to only one vendor.
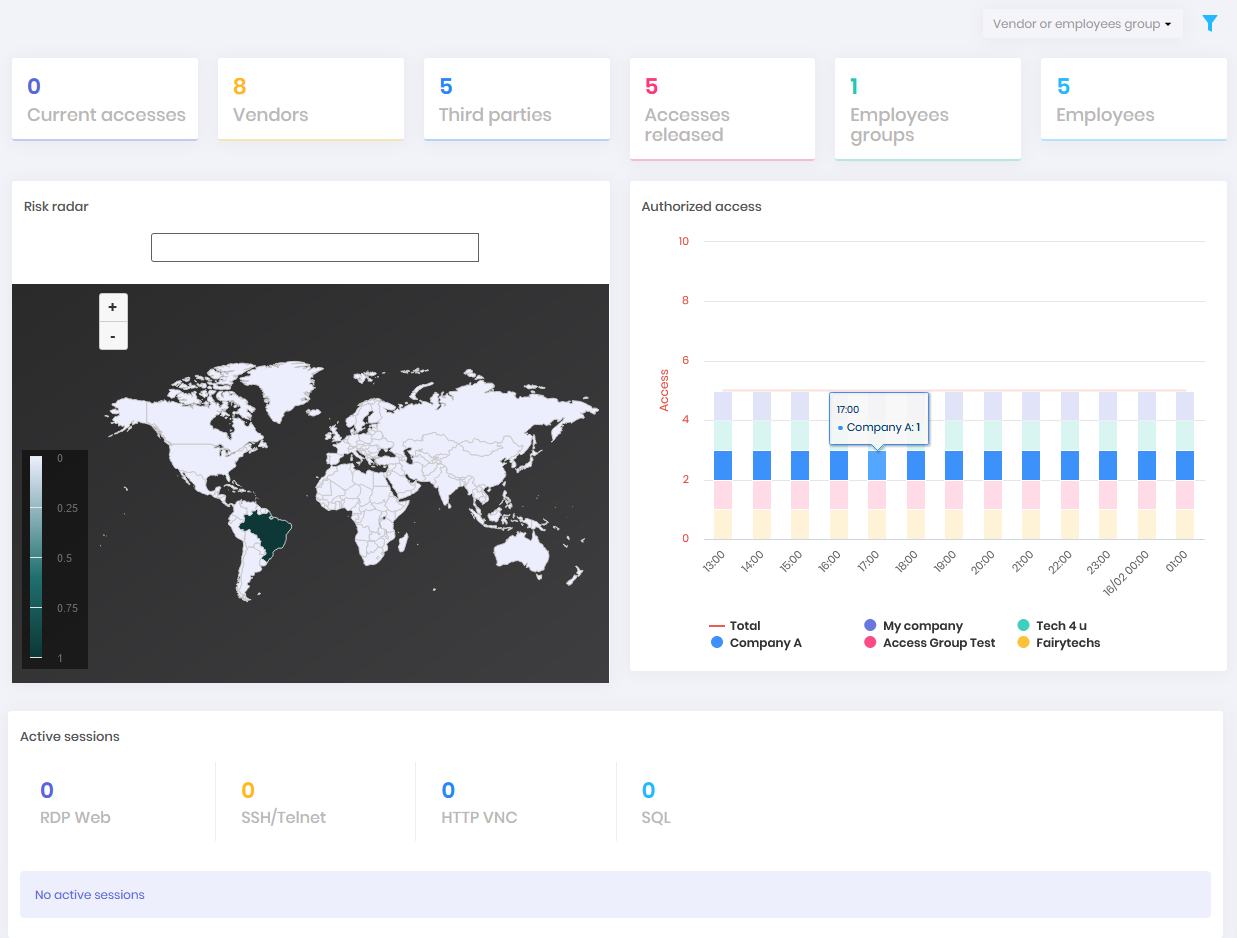
Current accesses: Displays the number of Domum accesses that are occurring at the time this dashboard is being viewed
Vendors: Quantity of vendors registered in the senhasegura
Third parties: Number of third-party users registered in senhasegura
Accesses released: Displays the total of released accesses, third-party users and employees
Employees groups: Domum access groups of the employees who already have access to the senhasegura .
Employees: Number of employees who have liberated access to Domum.
Risk radar: Displays which regions in the world suspicious accesses are originating from. You can use the search bar to type the name of the location you want to query.
Authorized access: Displays the relation of the quantity of accesses and allowed times for each vendor
Active sessions: A list of remote sessions in progress at the time of the dashboard view, and the proxies being used for these sessions.
Gateway Status Notification: The broadcast icon will show the communication between the vault and the gateway service, and this status contains (Datetime, Errors, Details). When the light is green, it means that communication is established. It has been working without any failures in the past 12 hours; gray indicates that the service is not configurated; yellow represents the communication is established, but some failures could have happened in the past 12 hours; and red means that the communications are not working.
It is possible to send this communication notification to your SIEM, and the communication status is periodically refreshed.
Vendors
To get an overview of how a specific vendor is performing in the Domum environment you can access the exclusive dashboard for this vendor, go to the menu: Dashboards ➔ Vendors then use the filter in the top right corner and select the vendor you want to query and then click the filter button.
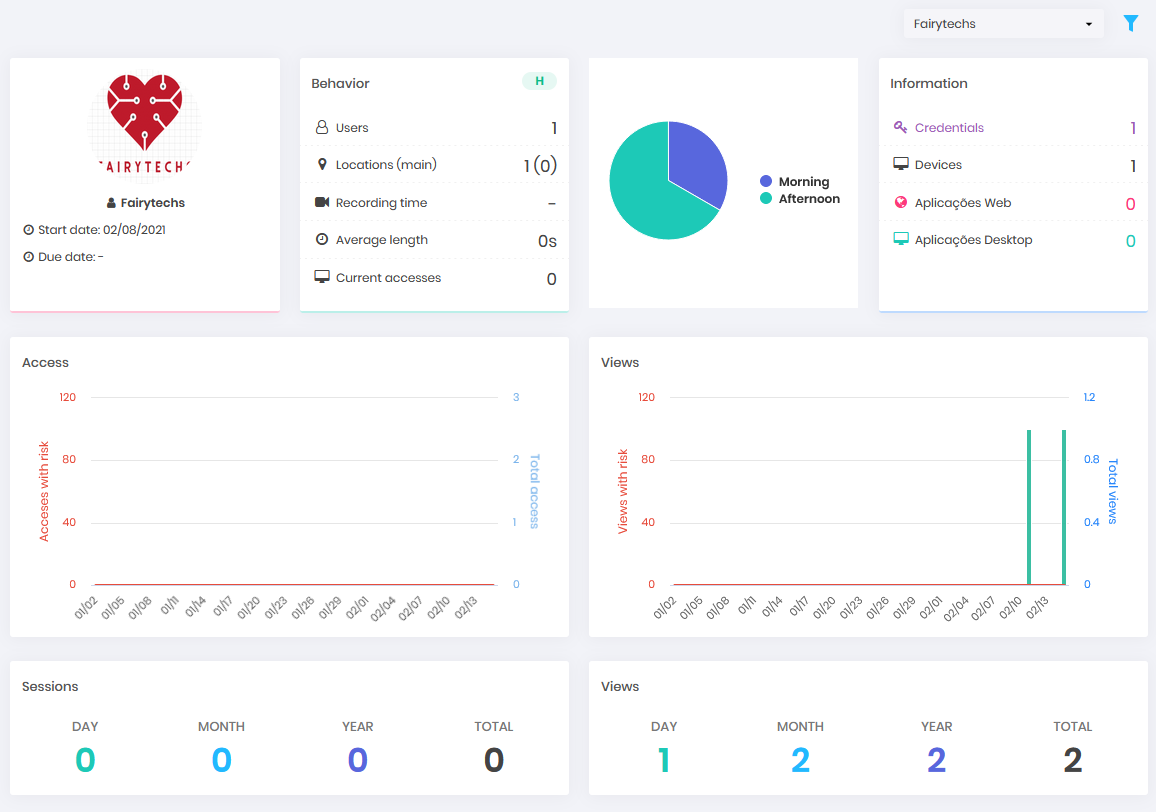
This dashboard will display blocks of information such as:
Behaviour: In this block it is possible to check how many users (enabled users) this vendor has registered in the senhasegura , if there is a location control, in other words, the places from where the access can be originated. Besides the recording time, quantity and average time of remote sessions. Each item in the block has a link to more detailed information about the data shown, click to be redirected to the corresponding report.
Chart: The pie chart shows a view of the period when accesses were made by users belonging to this provider. Hovering the cursor over the portion of the period will display the number of remote sessions or password views that occurred at that time.
Information: In the information block you can get a view of how much privileged information the users of this vendor have according to type. Each item in the block has a link to a more detailed report about the information, for example the complete list of credentials, and which devices the users of that vendor have access to.
Access: The bar chart shows how many remote accesses were made in the 45-days and how many of these were at risk.
Views: The bar chart displays how many password views were performed in the 45-day period and how many of these were at risk.
Sessions: This block will display the number of remote sessions held on this day of the dashboard view, in the current month and year, and finally, the total number of sessions held so far.
Views: This block will display the number of password views performed on this day of the dashboard view, in the current month and year, and finally, the total number of sessions performed so far.
Third-party users
To get an overview of how a specific vendor's employee is behaving in the Domum environment you can access the dashboard for this user only, go to the menu: Dashboards ➔ Third-Party Users then use the filter in the top right corner and select the vendor and user you want to query, then click the filter button.
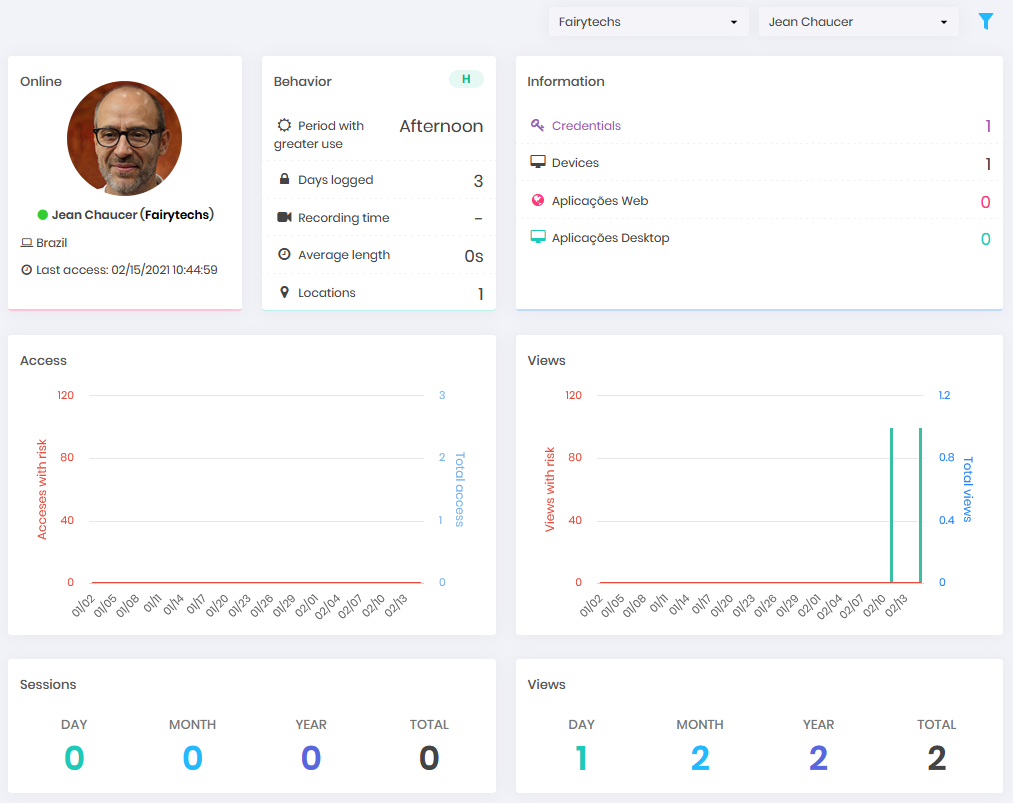
This dashboard will display blocks of information such as
Status: Displays whether the user is online using Domum, from which region he is accessing from, and the date and time of his access.
Behavior: In this block you can check how many days he has already accessed Domum, the time he usually accesses, the locations from where this user's access is allowed to originate. In addition to the recording time, quantity and average time of the remote sessions performed.
Information: In the information block you can see how much privileged information this user has access to according to type. Each item in the block has a link to a more detailed report about the information, for example the complete list of credentials, and which devices this user has access to.
Access: The bar chart shows how many remote accesses this user has made in the 45-day period and how many of these were at risk.
Views: The bar chart displays the number of password views performed by this user over the 45-day period and how many of these were at risk.
Sessions: This block will display the number of remote sessions performed by this user on this day of the dashboard view, in the current month and year, and finally the total number of sessions performed so far.
Views: This block will display the number of password views this user has had on this day of the dashboard view, in the current month and year, and finally the total number of sessions so far.
Employees
This dashboard will display Domum access information of an employee, that is, a user that already has access to the secure login. Go to the menu: Dashboards ➔ Employees then use the filter in the top right corner and select the employee you want to query.
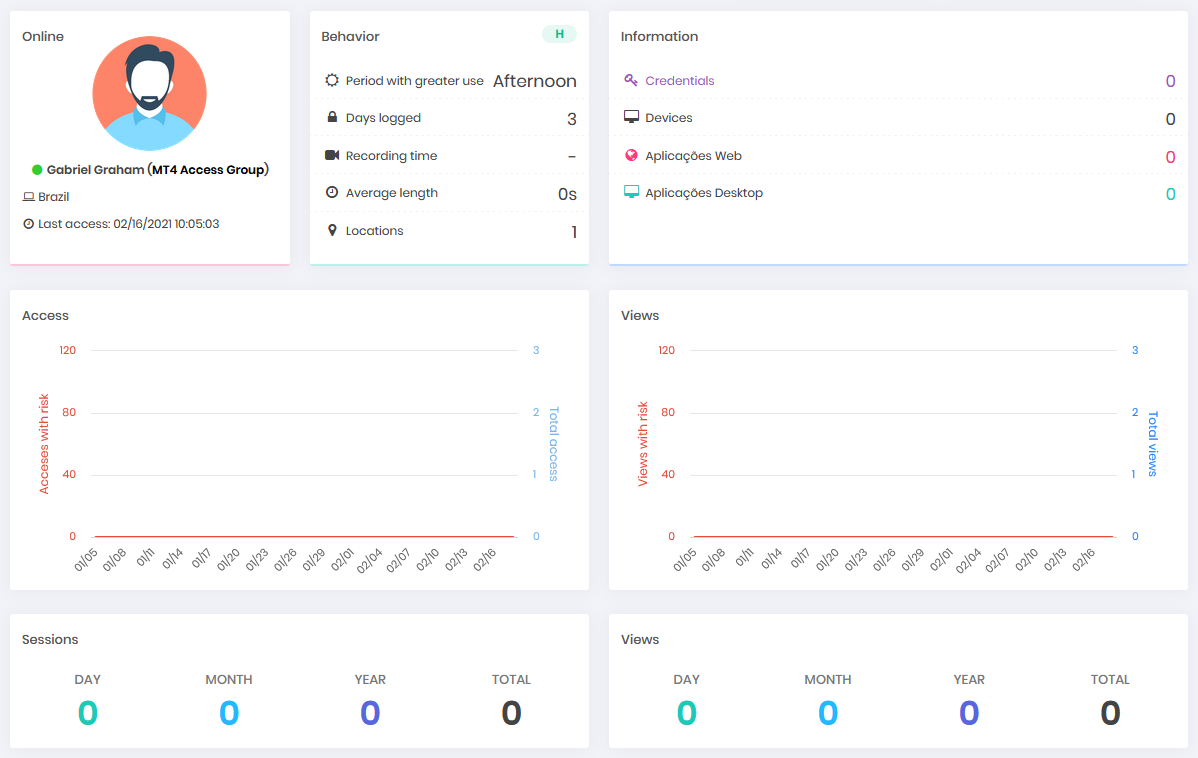
Status: Displays whether the user is online using the senhasegura through Domum or not and from which region he is accessing and the date and time of his last access.
Behavior: In this block it is possible to see how many days the user has already accessed via Domum, the time he usually accesses, the places from where this user's access is allowed to originate. In addition to the recording time, quantity and average time of the remote sessions carried out.
Information: In the information block you can see how much privileged information this user has access to according to type. Each item in the block has a link to a more detailed report about the information, for example the complete list of credentials, and which devices this user has access to.
Access: The bar chart shows how many remote accesses this user has made in the 45-day period and how many of these were at risk.
Views: The bar chart displays the number of password views performed by this user over the 45-day period and how many of these were at risk.
Sessions:This block will display the number of remote sessions performed by this user on this day of the dashboard view, in the current month and year, and finally the total number of sessions performed so far.
Views: This block will display the number of password views this user has had on this day of the dashboard view, in the current month and year, and finally the total number of sessions so far.
Session and access reports
senhasegura has reports to query details about Sessions and Accesses. These reports show a detailed view of how the remote session or password viewing took place, for example indicating which user performed the action and from which IP, credential and device was used or queried in the action.
To view the session report go to Domum ➔ Reports ➔ Sessions. In this report, it is possible to check which credentials and devices are being used to perform the remote sessions and by which vendors and third-party users, time and duration of the session, as well as the protocol, used. This way the auditor can understand if there is any divergence between what was determined in the policy and in granting access, and what is happening.
To access the video and other details of the remote session, note the code of the remote session you wish to check the video or logs for and go to the menu: PAM ➔ Access control ➔ Remote sessions. Search for the session code in this report and click the log action button:
Video of session: To watch the video or download the video file of the session.
Session logs: To view the events that occurred during the session or export the log data.
More: Record session macro, prevent purge or set the auditors users for this session.
Access the access reports through the menu: Domum ➔ Reports ➔ Access. In this report, it is possible to see which users used or accessed the senhasegura through the Domum platform, this way the auditor can check if the correct users are having access to the platform, if the location of their access matches the permission given to them or if there is any inconsistency.
Access Details
You can also check the access details of the user types:
Third-party users
Go to the menu: Domum ➔ Remote Access ➔ Third-Party Users
Employees
Go to the menu: Domum ➔ Remote Access ➔ Employees
Search the report for the user you want to check the access details of and click on the action button for the record Details.
If the user's access has not yet expired or been canceled the registration action button will have other options, choose the details option to check the access data.
In the displayed report you will have details such as
user's username;
the company that is employed by, in the case of third-party users;
which access group it belongs to
start and end date of access to Domum;
whether it is allowed to perform sessions or view passwords according to each credential and device it has access to;
days and times you can access the platform and maximum number of accesses
justification for granting access
Conclusion
By the end of this book you will have acquired the knowledge to perform the activities related to Domum.
If you wish to continue learning how to use the senhasegura in the best possible way, please ask our support team for our available documentation according to your profile and needs.
- See the Orbit Command Line manual to understand how to configure the Domum Gateway↩