Automations
DevOps Secret Management module allows administrators to setup automations for active life-cycle management of secrets in applications like cloud secret management services such as Google Cloud Secret Manager, Azure Key Vault, AWS Secrets Manager, and others, as well as Kubernetes environments, configuration files inside servers, etc...
Through the usage of these automations it is possible to connect on most environments and systems using a protocol driven approach, where senhasegura DSM will reach those systems and environments through SSH, Windows RM & RPC, SQL, HTTP/S and others so it can run a series of pre-defined commands to manipulate secrets without the needing of manual configuration.
Automations are based on triggers, those that can be executed depending on the application and the secret being monitored. DSM allows automations to run based during the following moments:
- Secret creation on a specific secret or application;
- Secret update on a specific secret or application;
- Secret activation on a specific secret or application;
- Secret inactivation on a specific secret or application;
- Authorization creation on a specific application;
- Authorization update on a specific application;
- Authorization activation on a specific application;
- Authorization inactivation on a specific application;
Automations can also run Ansible Playbooks inside Dockers containers to ensure more security and allow greater possibilities for integrations.
Register an Automation
To create an automation follow the menu DevOps Secret Manager ➔ Automations ➔ Automations.
- In the report's action button, click on New;
- Fill the automation general fields:
- Name*: Automation name used internally for identification and reports;
- Enabled*: Whether the automation is available for use or not;
- In the Information tab, fill the following fields:
- Description: A detailed description of the automation;
- Tags: List of tags to further identify the automation;
- In the Trigger tab, fill the following fields:
- Trigger*: The event triggers who start the automation process. One or more can be selected;
- Application: One or more applications to be observed by the selected triggers;
- Secret: One or more secrets to be observed by the selected triggers;
- In the Action tab, fill the following fields:
- Plugin: Protocol or application which will execute the select template;
- Template: Template containing instructions which will be executed on the target application;
- Device: Target device which senhasegura DSM will connect to through the selected plugin to execute the template;
- To finish, click on Save.
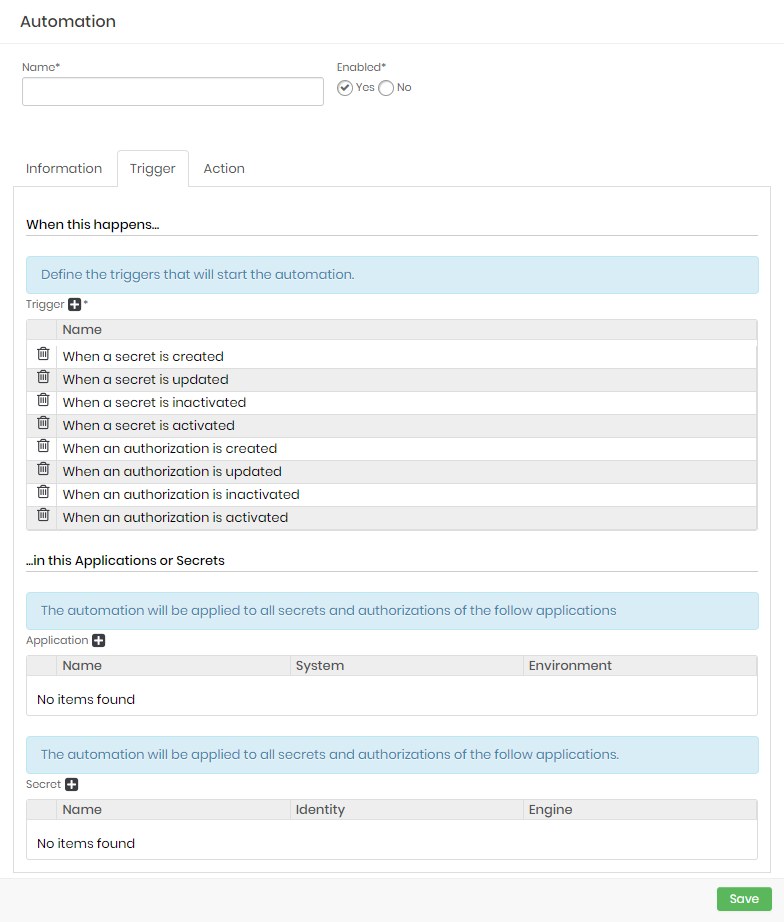
Fields marked with asterisks (*) are required and it is not possible to proceed if they are not provided.
DevOps Secret Management uses templates registered as Secret Management Automation type on the Executions module. For more information on how to create templates, please check the Automated Executions.
View an Automation
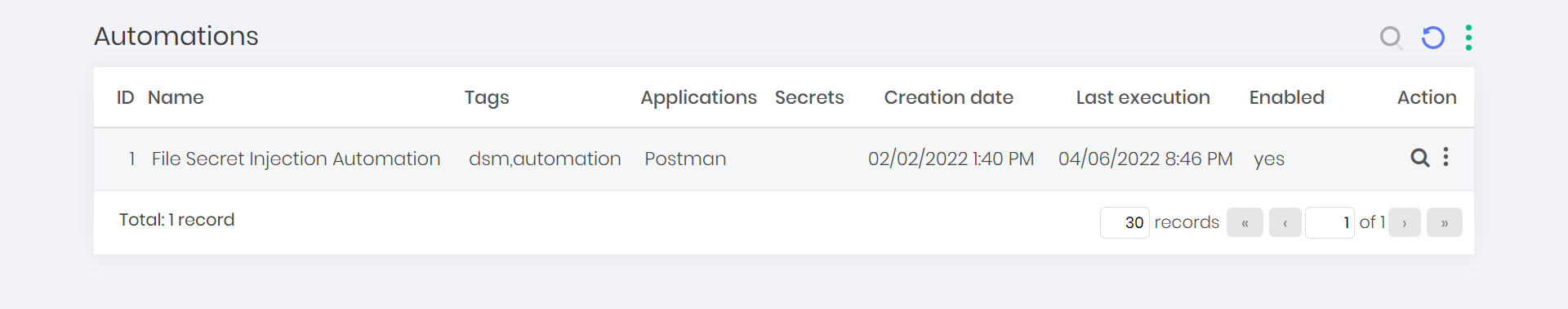
To see a list of all configured automations inside DSM follow the menu DevOps Secret Manager ➔ Automations ➔ Automations.
On this screen, you can view registered automations with extra informations such name, tags, automations applications, automation secrets, creation date, last execution date and if the automation is enabled or not.
View an Automation Execution Status
To see all the automations executions status follow the menu DevOps Secret Manager ➔ Automations ➔ Executions.
On this screen, you can view automations execution status with extra informations such as automation name, trigger, target device, status and creation date.
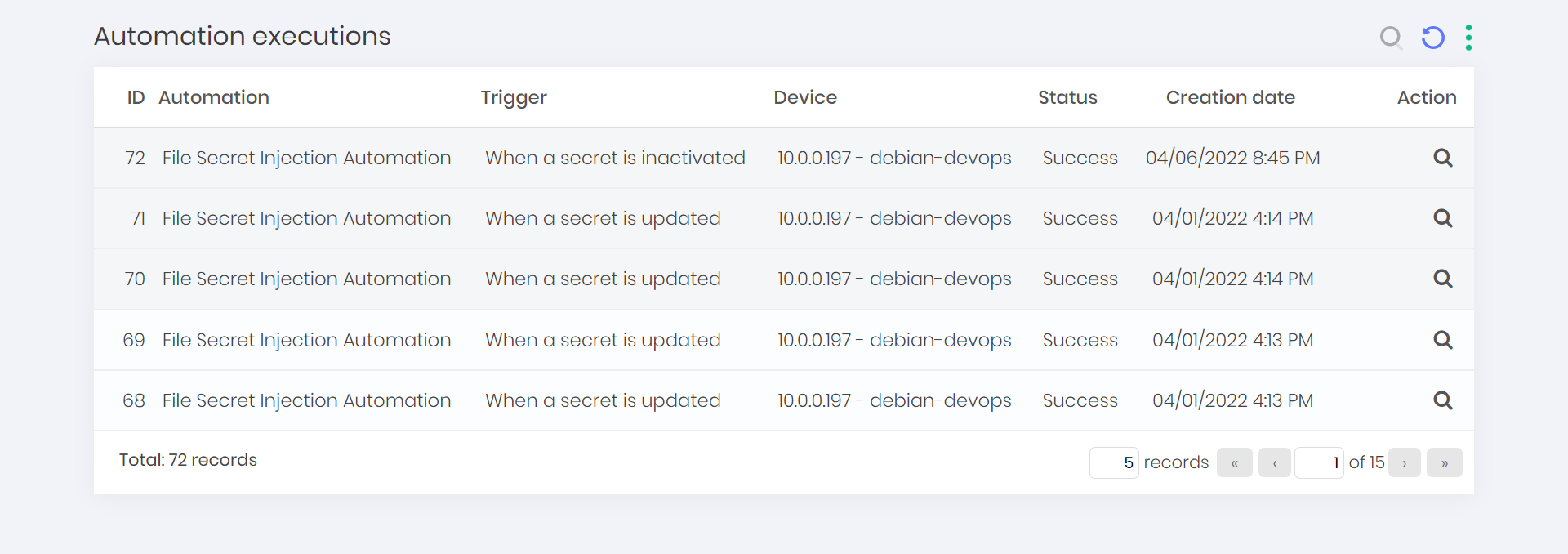
To see more details about the execution, click on the Details action for the selected execution.
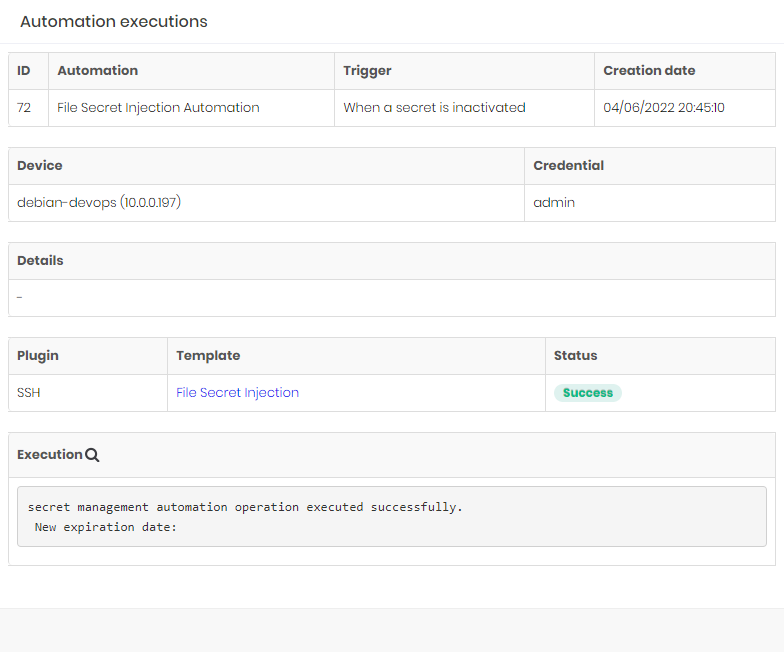
For security reasons, sensitive information such as passwords and access keys are replaced by a mask in the details of the template execution.
Automatically provision API from Applications POST method
In Applications POST API /iso/dapp/application)
Add cloud_profiles parameter:
Name: cloud_profiles
Type: string[] (Array of strings)
Required: no
Application-related dynamic cloud provisioning profiles are defined. The value filled in will overwrite the current value of the application. When the value is omitted, no changes are made. If an empty array is filled, all application profiles will be removed.
Example: cloud_profiles: ["aws_profile", "gcp_profile"]
Add credential_profiles parameter:
Name: credential_profiles
Type: {device: string, profile: string}[] (Array of objects with a device and profile keys)
Required: no
Application-related dynamic cloud provisioning profiles are defined. The value filled in will overwrite the current value of the application. When the value is omitted, no changes are made. If an empty array is filled, all application profiles will be removed.
Example: credential_profiles: [
{device: "192.168.0.1", profile: "cassandra_profile"},
{device: "192.168.0.2", profile: "redis_profile"},
] :::