Automations
senhasegura DSM allows creation of automation for secrets life-cycle active management in applications such as, Kubernetes and cloud services such as Google Cloud Manager, Azure Key Vault among others.
Automations are based on triggers, such as creating or updating a secret:
Secret creation;
Secret update;
Secret activation;
Secret inactivation;
Authorization creation;
Authorization update;
Authorization activation;
Authorization inactivation;
The automation module already has several predefined connectors to make easy a resource usage, but new ones can be easily created from templates.
Automations can be used to add, update and delete secrets. But they are not limited to these cases only. For example:
Templates for databases;
Templates to change application or server configuration files;
Templates to run on Kubernetes, OpenShift or other Kubernetes services;
Templates to run into cloud services like Google Secret Manager;
Automations can also run Ansible Playbooks inside Dockers containers to ensure more security and allow greater possibilities for integrations.
Creating an automation
To create an automation, click at the menu: DSM ➔ Automations ➔ Automations
Click the actions button and click at New;
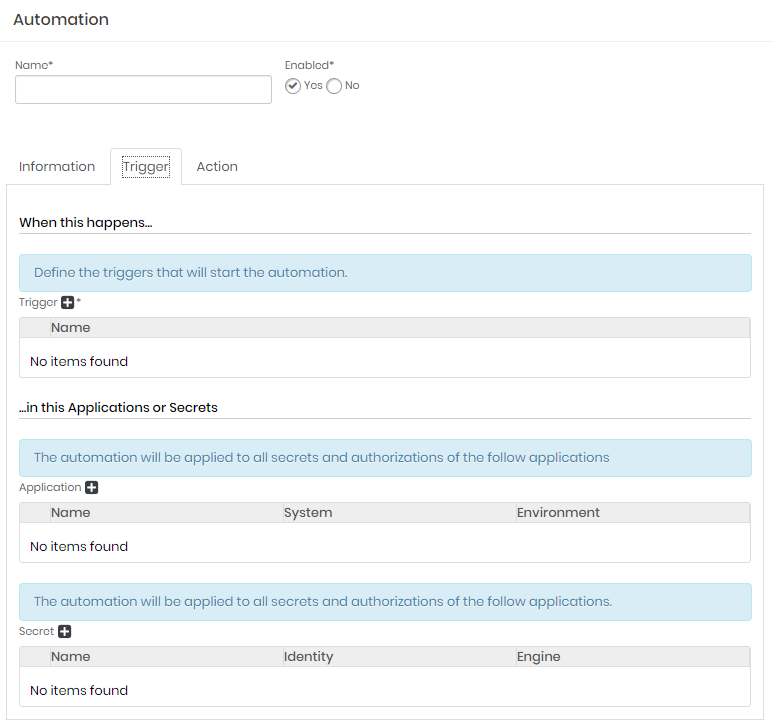
Fill the automation general fields:
Name: It will be the automation name. It will be used internally in the senhasegura for identification on other screens;
Enabled: Indicates whether automation is available for use;
At Information tab, fill the following fields:
Description: A detailed description of this automation;
Tags: Tags to be used as filter or data segregation inside senhasegura ;
At Trigger tab fill the following fields:
Trigger: It's the event triggers who start an automation process. Select one or more items;
Application: Select one or more applications to be triggered by the selected triggers;
Secret: Select one or more secrets to be triggered by the selected triggers;
At Action tab fill the following fields:
Plugin: which protocol or application will execute the select template;
Template: which template will be executed into the target application;
Device: which device will be connected by the plugin to execute the template;
Click at Save button to finish;
It's really easy and fast to create new templates to perform new integrations in others solutions.
Automations details
Click at DSM ➔ Automations ➔ Automations menu to list all automations.
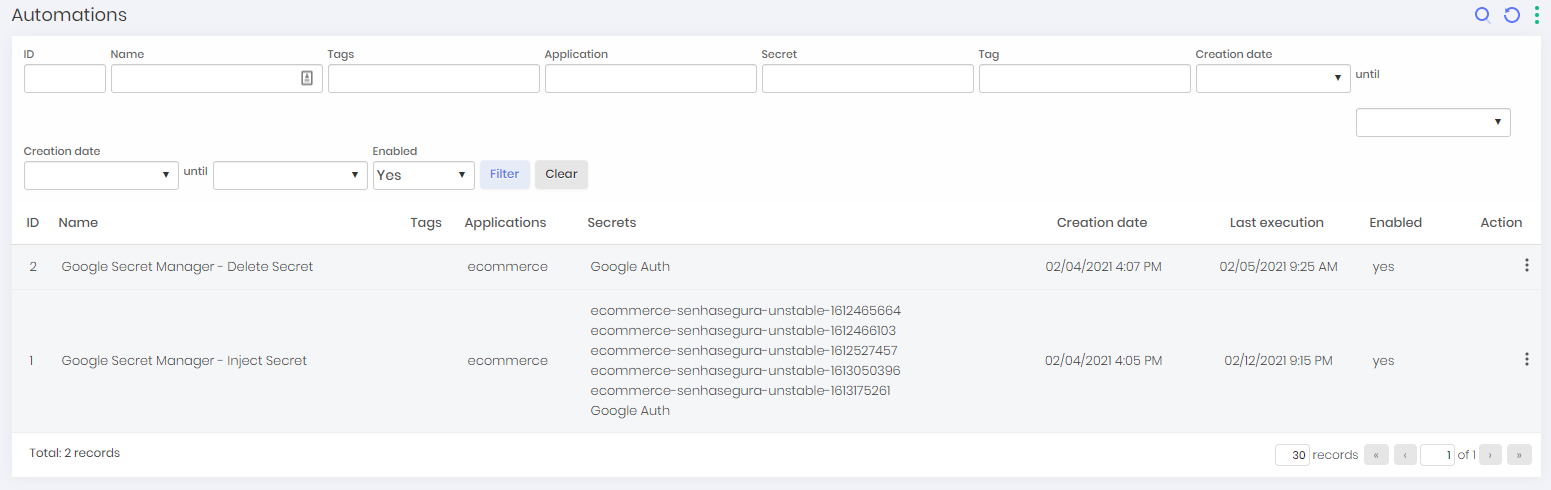
Into this report you can see all automations with its data like name, tags, automations applications, automation secrets, creation date, last execution date and status;
Automation execution details
Click at DSM ➔ Automations ➔ Executions menu to list all automations result. Search for a desired automation execution record and click at its Detail button.
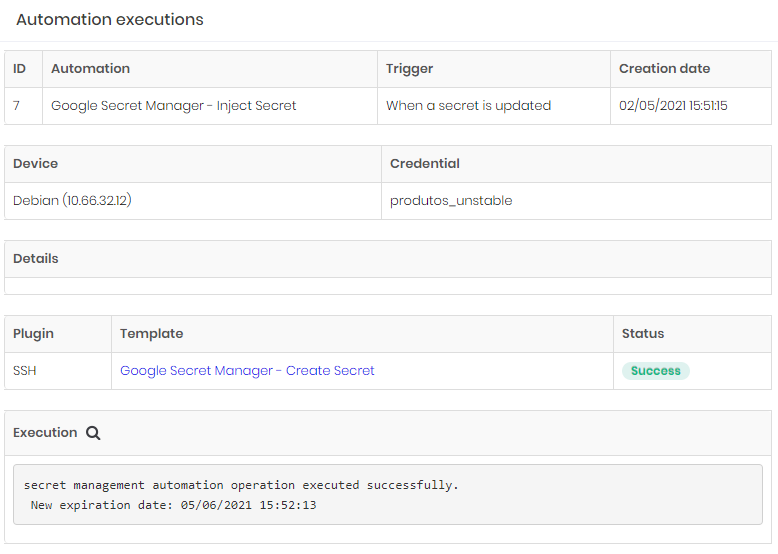
In the Execution section, click on the Execution details button to view the template's execution details.
For security reasons, in the details of the template execution, sensitive information such as passwords and access keys are replaced by a mask.
Inject and change secrets into Azure Key Vault, AWS Secret Manager, Google Secret Manager and Kubernetes
Create an automation as described at section dsm-create-automation of this manual, and in the Action tab, select a template to be executed:
Azure Key Vault
On the Action tab, select the Azure Key Vault - Inject Secret template to inject and rotate secrets.
After execution, access the Azure portal, search for the Key Vaults service, select the vault where the secret was injected. In Settings, click on Secrets and click on the one created by senhasegura to view its details, as in the example below:
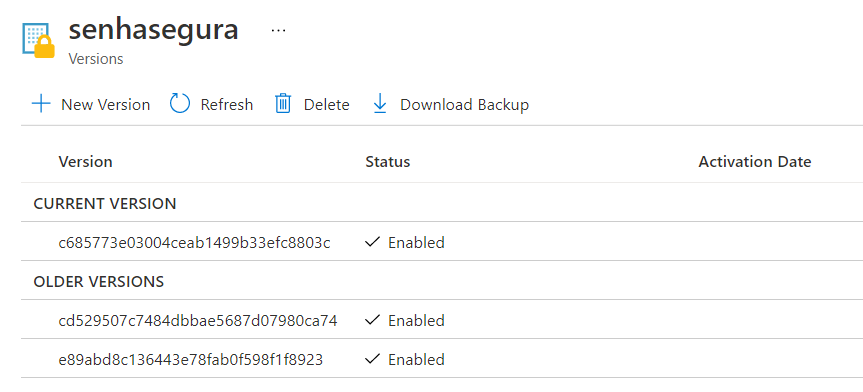
AWS Secret Manager
On the Action tab, select the AWS Secret Manager - Inject Secret template to inject and rotate secrets. After running, access the AWS management console, look for the Secret Manager service. In the list of secrets, click on the one created by senhasegura to view its details, as in the example below:
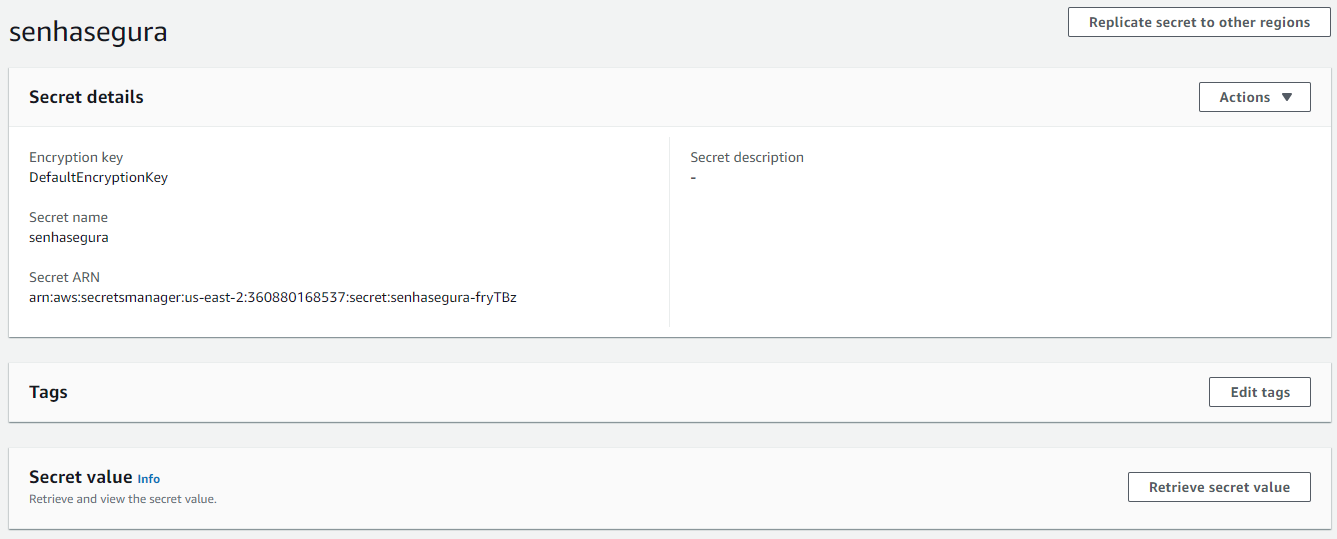
Google Secret Manager
On the Action tab, select the Google Secret Manager - Inject Secret template to inject and rotate secrets. After execution, access the Google Cloud console, select the project in the top selection bar, in the side menu access Security ➔ Secret Manager. In the list of secrets, click on the one created by senhasegura view its details, as in the example below:
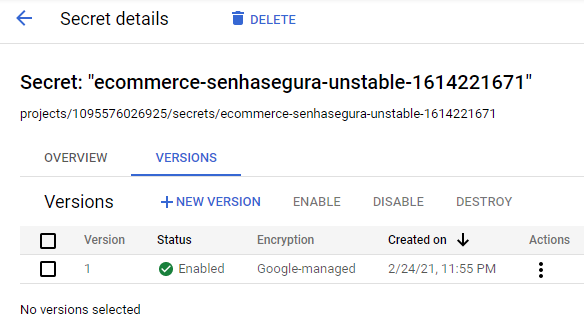
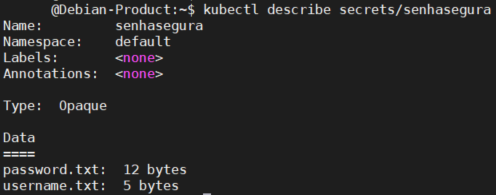
Kubernetes
On the Action tab, select the Kubernetes - Inject Secret template to inject and rotate secrets. After execution, access the Kubernetes cluster where the secret was created and view the secret with the command kubectl describe secrets/[secret_name], as in the example below: