Authorizations
DevOps Secret Management Authorizations allows administrators to define the access policies to application and secrets data. Those access policies provide configurations such as:
- Which resources can be accessed;
- Authorization expiration date;
- List of allowed devices IPs to perform requests;
- List of allowed request origin URLs through HTTP Referers to perform requests;
- Environment where the authorization will be used;
- System where the authorization will be used;
- Secrets that can be accessed;
Authorizations inside senhasegura DSM are configured by application, where an application can have multiple authorizations allowing access to different groups of secrets. This way is easy to create segregation between environments, for example, where a development or homologation environment might be using different secrets then those used in production.
Also, it is possible to define sensitive information encryption, where data such as Credentials Password and Secret Access Keys are obfuscated even if a developer can access secret information once outside the vault, for example.
Register an Authorization
To register an authorization follow the menu DevOps Secret Manager ➔ Applications ➔ Applications.
- On a selected application, click on the Authorizations button;
- In the presented screen, use the plus icon to create an authorization;
- In the Settings tab, fill the following fields:
- Expiration date/time: Date/time on which the authorization will be automatically revoked;
- Enable*: Whether the authorization is enabled for use or not;
- Enable encryption of sensitive information*: Whether confidential data should be sent as encrypted;
- Environment*: Environment which this authorization belongs.
- System*: System which this authorization belongs.
- Allowed IPs: A list of IPs that are allowed to use this authorization.
- Allowed HTTP referers: A list of applications URLs allowed to use this authorization;
- Certificate fingerprint: A certificate fingerprint that will be used to verify the request origin;
- In the Secrets tab, select which secrets can be accessed through this authorization;
- To finish, click on Save;
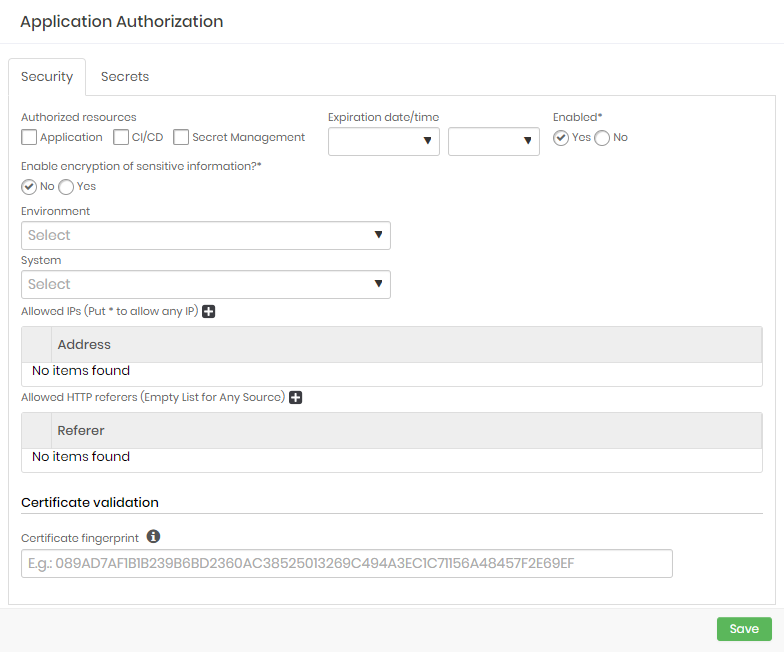
Fields marked with asterisks (*) are required and it is not possible to proceed if they are not provided.
By default, senhasegura DSM will reject every request attempt if no IP address is provided.
If not provided, senhasegura DSM will allow requests coming from any URL set in a request header.
To register systems and environments to use on authorizations follow the menu Settings ➔ System Parameters ➔ Systems and Settings ➔ System Parameters ➔ Environments respectively
View an Authorization
To view applications authorizations follow the menu DevOps Secret Manager ➔ Applications ➔ Applications.
- In the actions of an application, click on Authorizations.
On this screen, you can view the application authorization along with informations such as application name, environment, system, creation date and status of that authorization;
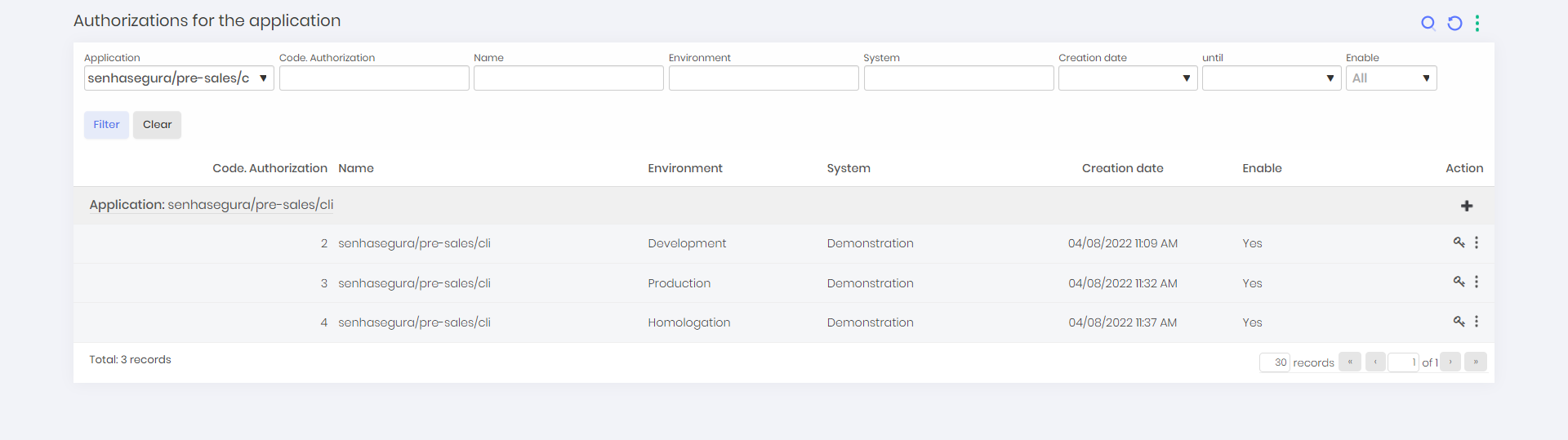
Optionally, you can go to DevOps Secret Manager ➔ Applications ➔ Authorizations by application to see a full list of all authorizations for all applications.
View an Authorization Tokens
To retreive the tokens from DSM to use in the resource follow the menu DevOps Secret Manager ➔ Applications ➔ Applications.
- Click on Authorizations to list all authorizations of an application;
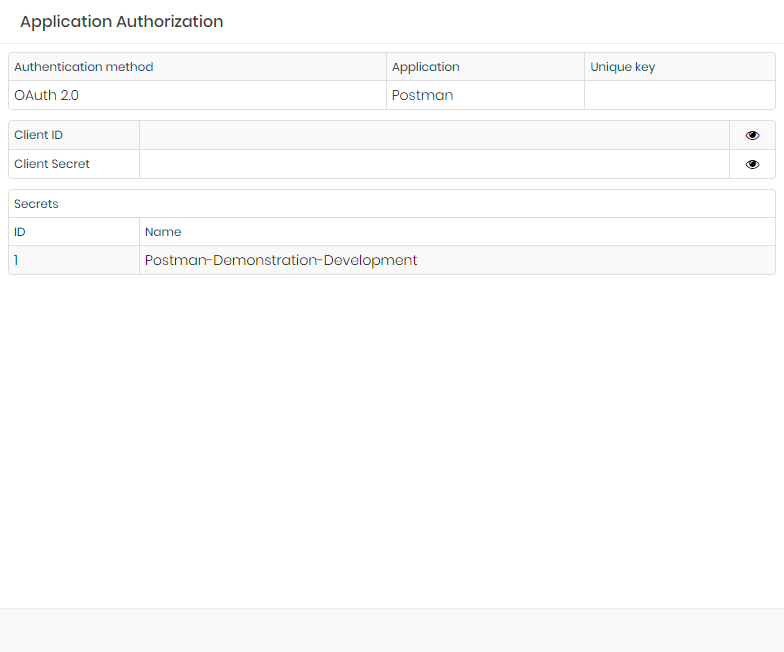
- In the authorization list, click on View authorization for the selected authorization;
- Use the eye icon to reveal the values depending on the selected authentication method on the application.
Optionally, you can go to DevOps Secret Manager ➔ Applications ➔ Authorizations by application to see a full list of all authorizations for all applications, where from there you can click on View authorizations of a selected authorization to retreive this same information.
Sensitive Information Encryption
Enabling sensitive information encryption allows senhasegura DSM to protect privileged data such as password and secret access keys even once the application retrieves it from the secure vault. Once enabled, DSM will generate a public key that can be used to verify and open the data.
To download the key, follow the menu DevOps Secret Manager ➔ Applications ➔ Applications.
- Click on Authorizations to list all authorizations of an application;
- In the authorizarion list, click on More options of a selected authorization, then Download public key.
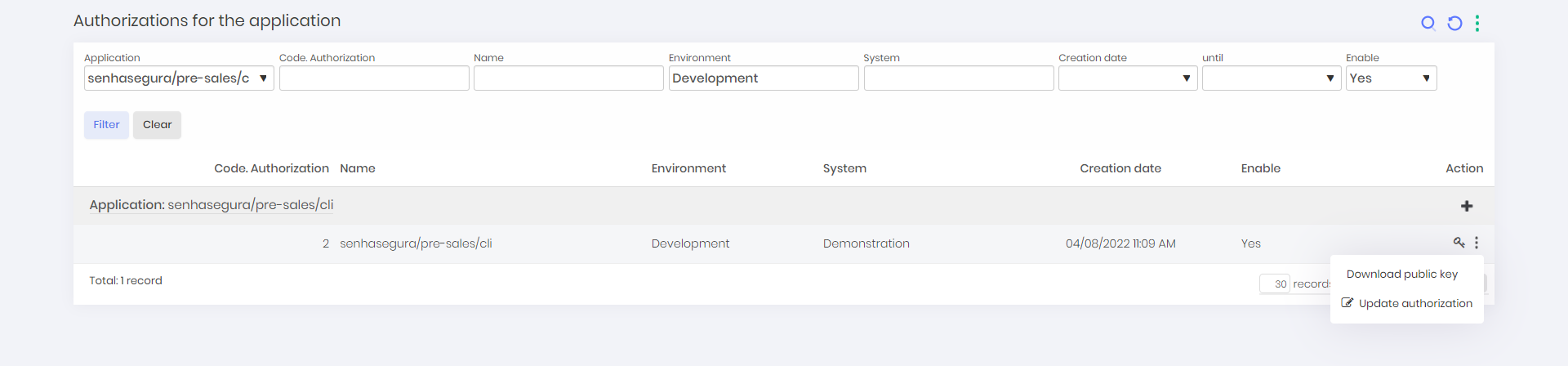
Optionally, you can go to DevOps Secret Manager ➔ Applications ➔ Authorizations by application to see a full list of all authorizations for all applications, where from there you can click on More options of a selected authorization, then Download public key.