Secrets
A secret is a set of sensitive information, such as credentials, cloud access keys or key/value pairs used in DevOps environment, which grants access to systems like databases, API servers, cloud services, and others. Developers and Security Teams often have dificulties managing those sensitive data on environemts like CI/CD pipelines, Infrastructure-as-a-Code (IaaC), automation tools such as Ansible and Puppet, or even hard-coded inside application dependencies. DevOps Secret Management module offers an easy-to-use way of managing secrets on those environments through an user-friendly interface, centralizing sensitive data in a secure and encrypted vault.
The DSM module current supports Credentials with username and password, as well as SSH Keys (through integration with PAM module), Cloud Credentials (through integration with Cloud IAM module), Ephemeral Credentials (through Dynamic Provision) and Key/Value pairs as secret data.
The secrets can be queried by applications or scripts through API calls using authorizations as access policies and can be injected on systems and environments through automations created directly in senhasegura, where the secrets will be created, updated and deleted without the need to change the application code.
Register a Secret
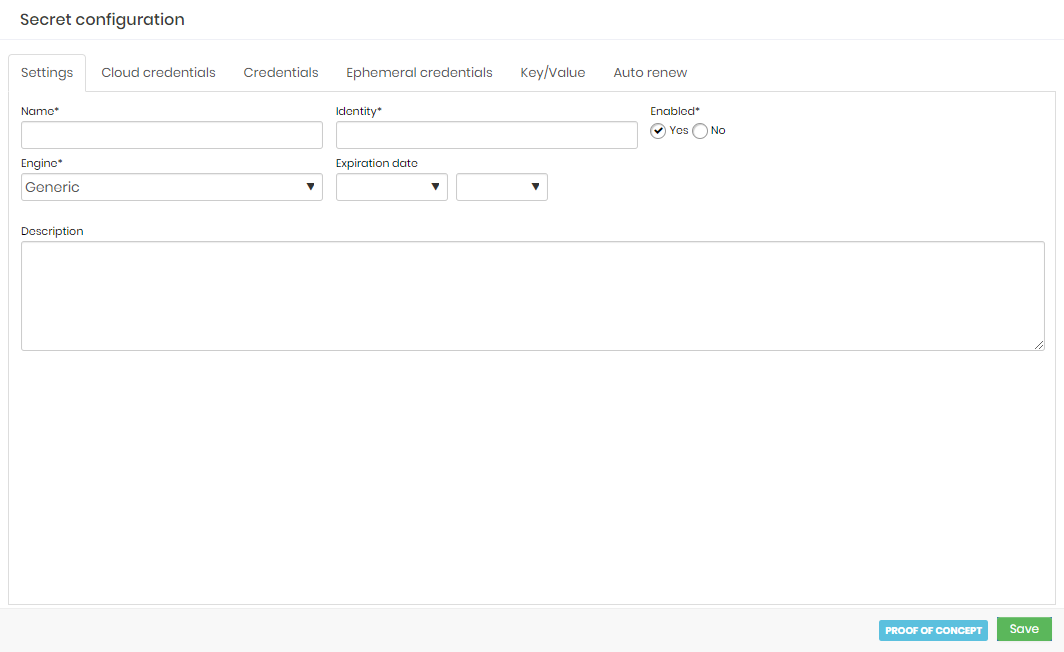
To register a secret follow the menu DSM ➔ Secret Management ➔ Secrets.
- In the report's action button, click on New secret;
- In the Settings tab, fill in the following fields:
- Name*: Name of the secret for management within senhasegura DSM;
- Identity*: Unique secret identifier used to query its data;
- Enabled*: Whether this secret is available to be used by applications;
- Engine*: Engine to be used. This information is used only for audit purposes;
- Expiration date: Date/time on which the secret will be automatically inactivated;
- Description: Secret usage description. Will not be used by applications;
- In the Cloud Credentials tab, select the cloud credentials that will be part of the secret;
- In the Credentials tab, select the credentials that will be part of the secret;
- In the Ephemeral Credentials tab, select the dynamic credentials that will be part of the secret;
- In the Key/Value tab, provide a key name and sensitive value pair.
- In the Auto-renew tab, select whether to:
- Enable/disable secret data renewal for Cloud Credentials, Credentials and Ephemeral Credentials;
- Determine an interval in minutes to renew data for Cloud Credentials, Credentials and Ephemeral Credentials;
- To finish, click on Save;
Fields marked with asterisks (*) are required and it is not possible to proceed if they are not provided.
Once the credential is rotated, senhasegura DSM will not delete the old information for Cloud Credentials and Ephemeral Credentials. For more information, please check the Dynamic Provisioning guide.
Cloud Credentials are managed by senhasegura Cloud IAM module. For more information on how to import Cloud Access Keys, please check the Cloud IAM guide.
Credentials are managed by senhasegura PAM module. For more information on how to create and manage credentials, please check the PAM guide.
Ephemeral Credentials are provisioned by senhasegura directly on the target through Dynamic Provisioning. For more information on how to configure it, please check the Dynamic Provisioning guide.
View a Secret
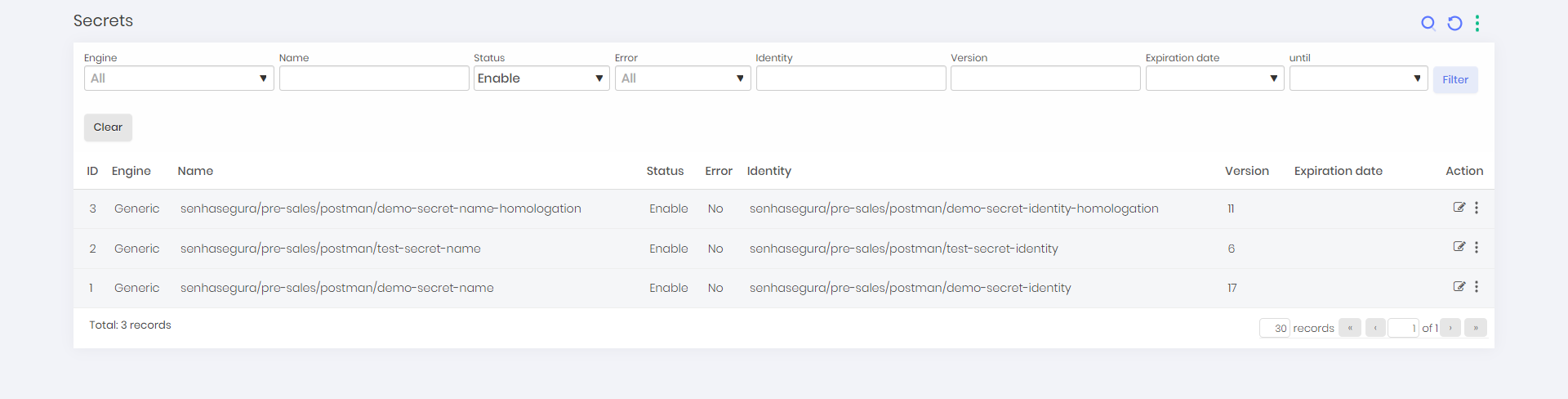
To view the a list of all secrets and its data follow the menu DSM ➔Secret Management ➔Secrets.
On this screen, you can view the existing secrets along with information such as engine, identifier, status, version and expiration date.
Viewing a Secret Version
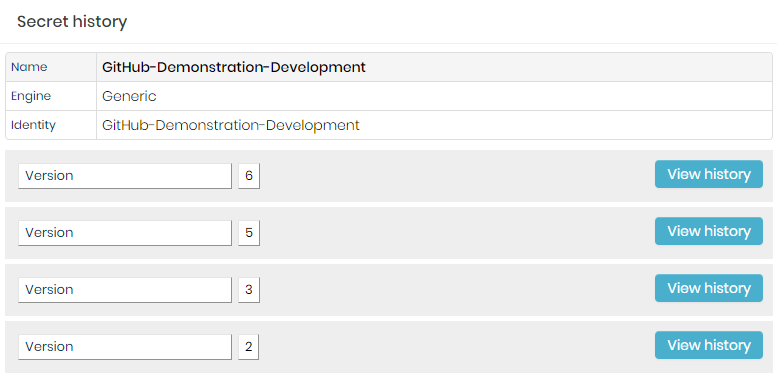
To view the secrets history follow the menu DSM ➔ Secret Management ➔ Secrets.
- In the actions of a secret, click on More options, then Show versions;
- In the presented screen, click on View history for the desired version;
- Use the eye icon button to view specific data of that secret version;