Applications
Applications inside senhasegura DSM allows administrators to create access segregation policies, where each application can have one or more Authorizations, allowing access to specific Secrets. Also, senhasegura DSM will automatically create reports based on those aplications, making easy for auditors to search specific data.
Another possible configuration is to have multiple Dynamic Provisioning profiles attached to an application, this way, everytime a request to create a new authorization for that application is made, senhasegura DSM will use this profile to create Ephemeral Credentials on target devices or a temporary Cloud Access Keys on AWS, Azure or GCP, automaticaly registering them as a secrets.
Every application can have its own authentication method, so other resources can use a secure way to fetch secrets of a specific authorization.
This guide will demonstrate how to create and manage applications through the senhasegura DSM web interface. For more information on how to create applications through APIs, please check de API guide.
Register an Application
To register a new application follow the menu DSM ➔ Applications ➔ Applications.
- In the report's action button, click on New;
- In the Settings tab, fill in the following fields:
- Application name*: Name of an application for management inside senhasegura DSM;
- Authentication method*: Method used to authenticate and retrieve data from senhasegura DSM.
- Enabled*: Whether the application will be active or not;
- Line of Business: Business type that the application serves;
- Application type: Application type;
- Tags: List of tags to further identify the application;
- Description: A detailed description for the application;
- Amazon AWS ARNs: A list of AWS credential ARNs;
- In the Automatic provisioning tab, fill the following fields:
- Cloud dynamic provisioning profile: Select the provisioning profile used to create credentials on Cloud Providers;
- Credential dynamic provisioning profile: Select the provisioning profile used to create credentials on Devices such as databases;
- To finish, click on Save;
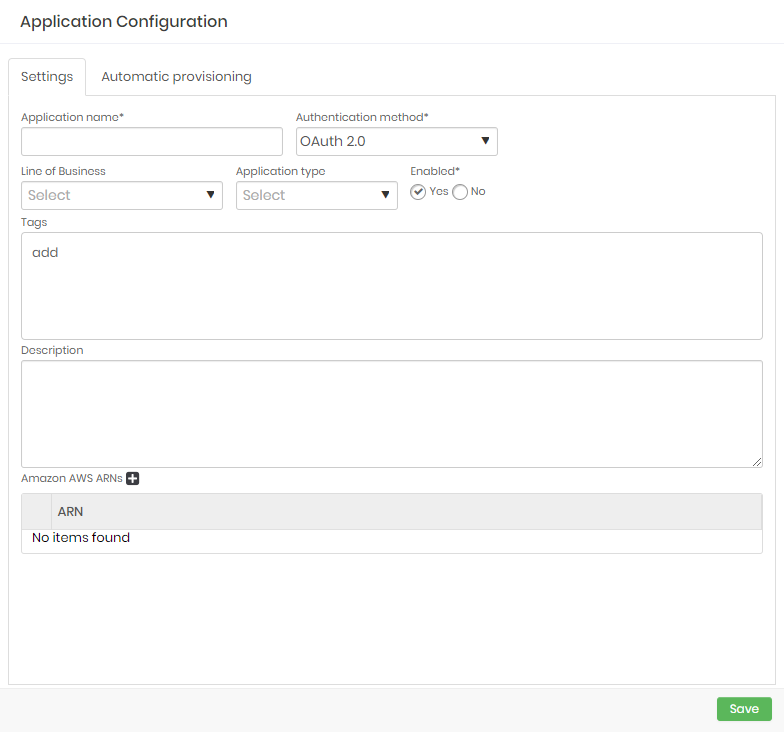
Fields marked with asterisks (*) are required and it is not possible to proceed if they are not provided.
The DSM module provide multiple ways for applications to obtain secret data. For more information on methods available check the Authenticators guide.
Automatic provisioning allows credentials and access keys to be generated and deleted automatically during the creation and inactivation of an authorization. For more information on how to enable and configure it, please check the Dynamic Provisioning guide.
View an Application
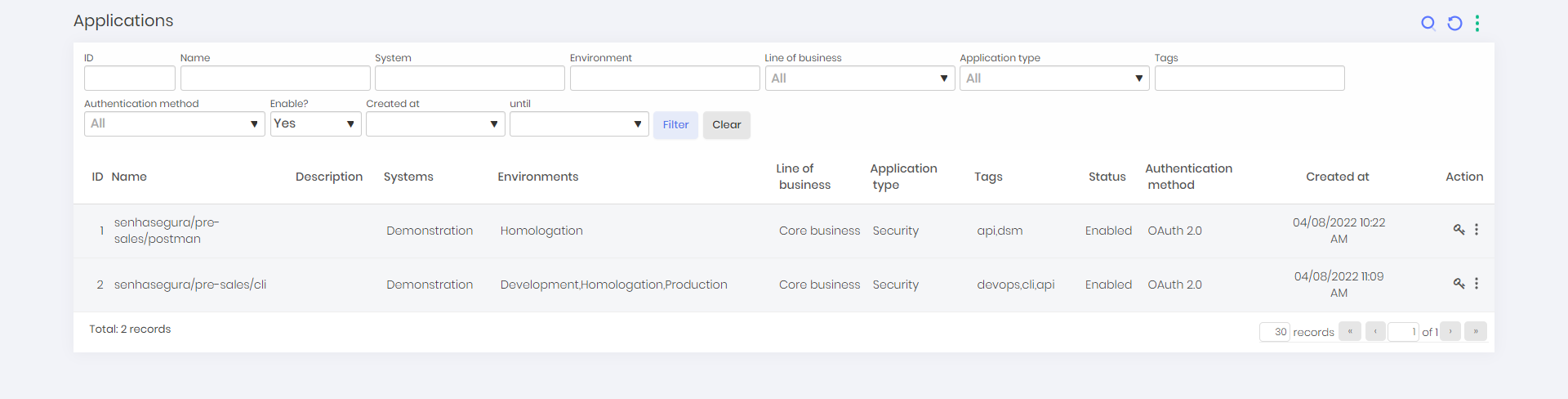
To view the list of applications follow the menu DSM ➔ Applications ➔ Applications.
On this screen, you can view registered applications with extra informations such name, description, systems, environments, business type, application type, tags, status, authentication method and creation date.
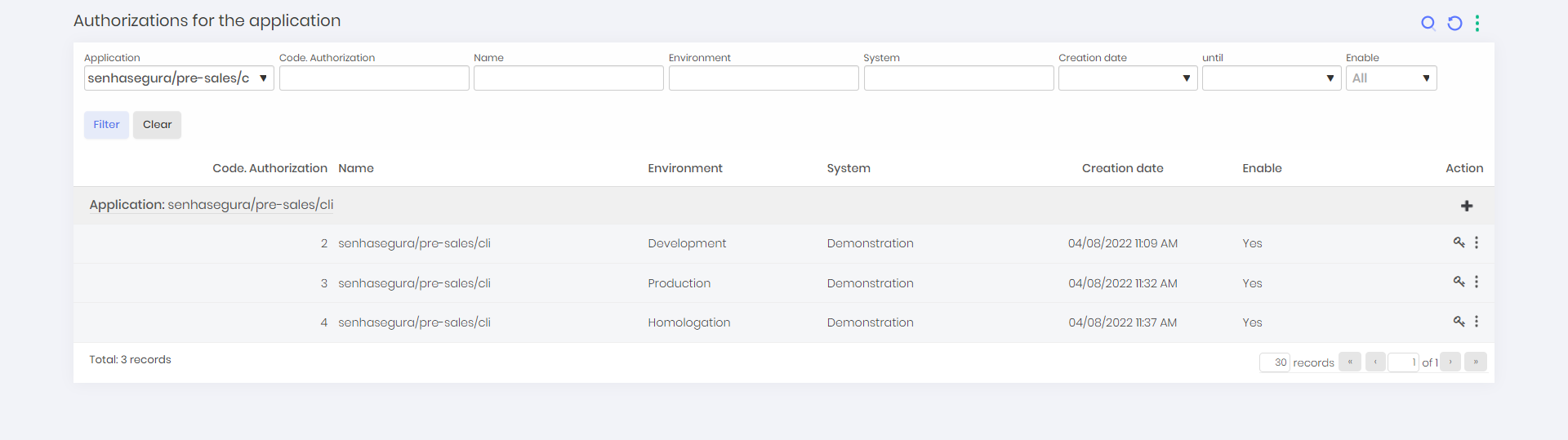
View an Application Authorizations
To view applications authorizations follow the menu DSM ➔ Applications ➔ Applications.
- In the actions of an application, click on Authorizations.
On this screen, you can view the application authorization along with informations such as application name, environment, system, creation date and status of that authorization;