First Configurations
The Domum workflow is quite simple and boils down to the administrator user defining and creating privileged remote access policies according to your company's needs. Domum will generate these accesses and they can be monitored and controlled by the Administrator. See below an example of the workflow and its respective steps:
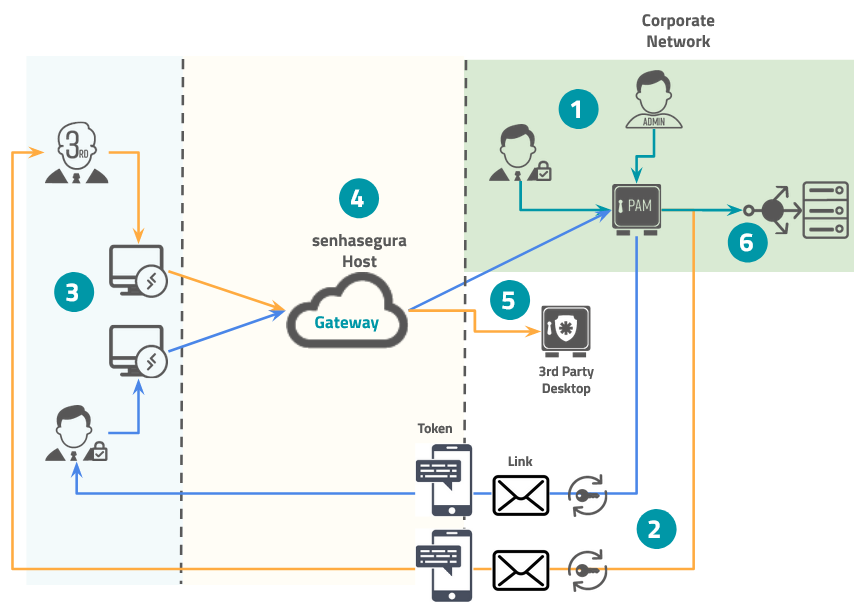
Administrator user defines and configures external accesses
The Domum will generate a personal link and a token via SMS or e-mail
The user accesses the link
The Domum Gateway communicates with the corporate environment
The user inserts the token received via SMS or e-mail to login
The user has authenticated access to the senhasegura where he can perform his operations
Administrator user
Before access can be granted to the external user, some settings need to be made within senhasegura by the System Administrator, which are:
Adjust the parameters
Create an access group for employees and third-party users
Register the vendor and third-party users
Register a reason why accesses should be granted
The following sections give a step-by-step example of how to implement these settings.
Domum Parameters
The basic functionalities of Domum can be seen at Domum Remote Access ➔ Settings ➔ Parameters.
This screen will display the configuration parameters, use them as needed for your operations:
Employees domain: Domain that will be used for the employee access link
Third-parties domain: Domain that will be used for the thrid-party access link
Sending account: Indicates the e-mail account responsible for sending the external access link
Initial authentication token: By default email, indicates the way by which the first access token will be sent
To fill in the fields of the Gateway Configuration section, it will be necessary to previously perform the communication configuration between the instance and the Domum Gateway. Please check the Orbit Command Line manual to perform the steps of this configuration.
If you have changed any parameter, click on Save to make sure that the senhasegura admits the changes.
Upon successful completion of the configuration, the data will be automatically filled by an automation.
Registering a reason for access
The Administrator must keep track of the reason and rationale for granting the third-party user or employee access.
Go to the menu Domum Remote Access ➔ Settings ➔ Access reason
In this report you can view all the reasons already registered, to register a new reason click on the button New.
Enter in the field, Name how the reason will be identified, for example: "Maintenance".
Click on Save.
The registered reason can be used for any third-party user or employee request, this record will be made available for all access request forms.
Creating an Access Group for Vendors
One of the first configurations that must be performed is the creation of an access group for the third-party users who performed the external accesses:
Go to the menu Domum Remote Access ➔ Access Control ➔ Access Groups. On this screen, you will see the report of all the groups already created on the senhasegura and which types of permissions they are associated with. Click the New option.
cautionIt is important to remember that this group is not related to the access group of the PAM Core module, the settings determined in this form are independent.
In the field, Access group name enter a name for the group that is easy to identify, and if you wish write a short description of the group in the field, Description.
In the Settings tab, determine how this group should behave about to the password view permission:
Users can view a password: Determines that the credential password can be seen by the user;
Require approval to view a password: Check whether another user will need to act as an approver to see the password. Once active, you also need to define for how long this approval will be valid;
Approvals required for viewing: The number of approvals required to approve the operation;
Disapprovals required to cancel: The number of refusals to stop the operation;
Approval in levels: Check whether approvers will be triggered in tiers. This way you can define a hierarchy of approvers;
Also on the same tab, determine how this group should behave about the remote sessions permission:
Users can start session: Flag if member users are allowed to start a proxy session using the credentials that this group is allowed to access;
Require approval to start session: Flag whether another user will need to act as an approver to start the proxy session. Once active, you will also need to define how long this approval is valid for;
Approvals required: Number of approvals required to approve the operation;
Disapprovals required to cancel: Number of refusals to stop the operation;
Approval in levels: Flag whether the approvers will be triggered in tiers. This way you can define a hierarchy of approvers;
Then determine the Settings of the access request:
Governance ID required when justifying?: Flag if the applicant must enter an ITMS code at the time of justification;
Always add user manager to approvers?: Flag if the user responsible for the user's department should be automatically alerted as an additional approver to this group. Therefore, this user will be alerted together with the other approvers in the tab Approvers;
If you have determined that this group requires approvers, go to the Approvers tab. Note that approving users have a Level setting in their registry. This setting determines the calling sequence for approving the operation, allowing a hierarchy to be applied.
infoIf you are an approving user the requests from other users will be on the menu: Domum Remote Access ➔ Access Control ➔ My Approvals. And if you are a user that needs approval you can view your requests in the menu: Domain ➔ Access Control ➔ My Requests.
To finish click on Save.
Registering Vendors and Third-Party Users
After you have created an access group for the third-party users and have registered an access reason, go to the menu Domum Remote Access ➔ Settings ➔ Vendors and follow the instructions:
On this screen, you will see the report of all the vendors already registered at senhasegura , as well as the Contract Number, contract and other details. Click on the option New
In the field, Vendor enter the name of the vendor to be registered.
Then select the access group created earlier in the field, Access group.
If desired, enter in the fields Contract Number and Document ID, the contract data and document ID respectively.
Select in the field Start date the date on which the contract for granting access started.
In the Photo field, you can select an image to represent the vendor being registered. This image must be in format
.pngor.jpgand be up to 5MB in size. It will be presented in the Vendor Dashboard. (In the vendor report, click on the vendor registration action button and choose the Dashboard option to view).Go to the Location tab. On this tab determine if access from this provider's users will be considered legitimate if they originate from a particular location, this setting is not mandatory, but if it is your wish check the Restrict access to only those locations option.
- Select the Country and Region from which the accesses must originate to be considered secure, then click the Add button. You can define more than one location if you wish.
To finish click on Save.
With the vendor registration completed, you can register the user that is the service provider of this vendor, to do this go to the menu Domum Remote Access ➔ Settings ➔ Third Party Users and follow the instructions:
On this screen, you will see the report of all third party users already registered at senhasegura , as well as which vendors they belong to and their contact data. Click on the option New
In the field, Vendor select the vendor you created earlier
Then, fill in the fields that refer to the user's personal data: Name, which will identify the user in the dashboards and reports, e-mail and Mobile phone, which will be how the senhasegura will send the access link to Domum, and the access token, in case the token is sent by SMS in the parameters.
cautionThis user must have a valid email account to receive the URL to access Domum. And a valid mobile phone number to receive the token, if the parameter for sending the token by SMS has been defined.
infoIt is recommended to use the SMS token sending parameter so that the access information is not concentrated in one place, making the process more secure.
In the Photo field, you can select an image to represent the user being registered, this image will be presented in his Dashboard. (In the third party users report, click on the action button of the user registration and choose the Dashboard option to view).
infoOn the Access tab you will get a report of all access requests for this user.
Click on Save to finish
Creating an Access Group for Employees
As previously stated, it is possible to grant access to Domum to employees in your company who already have access to senhasegura , but because of a scenario, for example, remote work or a business trip, they may need to perform their activities from an external network.
As Domum grants access to the senhasegura remotely and safely, it is possible to deliver to the employees an access link to Domum without the need to create a new user for them or to configure an external access group, since the secure login delivers to the employee the common access to the secure login that he usually has in the organizational environment, respecting the permission and the access group with which he is already registered.
Remember that accessing the senhasegura within the organizational environment using the company network will not have any change, the user will access the senhasegura as usual. However, when using external networks and being physically in a place away from your organization, you must use the Domum access link if you wish to use the senhasegura .
To grant the employee access, you must first create an employee group, this group will not configure permissions for viewing passwords or remote sessions, only allow authorized locations to be indicated for the origin of access for users who are members of this group. The access settings are the same as the access group configured in the PAM module, and other modules that the user uses, to which he belongs. To create an employee group go to the menu: Domum Remote Access ➔ Settings ➔ Employee group and follow the instructions:
When you access this menu you will be presented with a report with the list of employee groups already created. Click on the button New to register a group of employees.
Enter the Group Name, this name will be used to identify the group for granting employee access and in access reports, session and dashboards.
Then click on the addition icon and select the users that will be part of this group. This action does not mean that the user can already receive the Domum access link, adding a user to the group only indicates that he must respect the group rules. It is through the employee group field, on the employee access consent form that users will be displayed for granting access, so include in the group everyone who may now or in the future receive access to Domum.
cautionThe users added to the group must have an e-mail address registered at the senhasegura for the Domum access link to be sent.
Go to the Location tab. In this tab determine if access from this provider's users will be considered legitimate if they originate from a certain location, this setting is not mandatory, but if it is your wish check the Restrict access to only those locations option.
- Select the country and region from which the accesses must originate to be considered secure, then click the Add button. You can define more than one location if you wish.
To finish click on Save.