Additional Security Settings
Through the Settings ➔ System parameters ➔ Security menu you have access to additional security settings. In this screen you have access to settings that affect all system users.
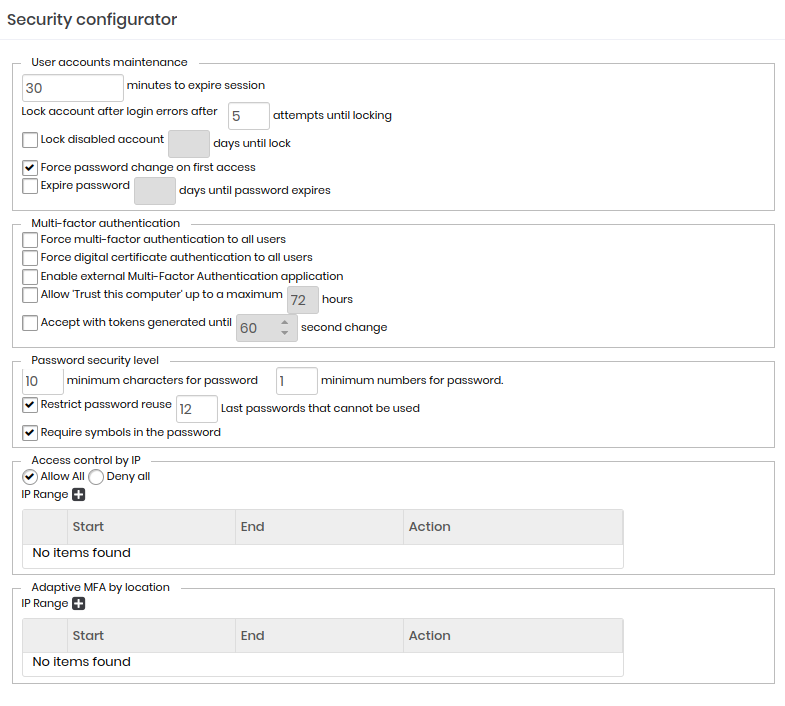
User accounts maintenance
Minutes to expire session: Inactivity time on the web interface so that the user session automatically expires.By default 30 minutes;
Lock disabled account: Flag to automatically block accounts that were not used after a range of days.Inactive by default;
Days until lock: Number of days to consider for an inactive account to be blocked;
Force password change on first access: Flag if the user must change his temporary password in the first access. Active by default;
Expire password: Forces the user's password expiration after a period of time. Inactive by default;
Days until password expires: Number of days for the password to expire automatically;
Warning. The Lock disabled account, Force password change on first access and Expire password configurations can only be used when the standard authentication provider of the senhasegura is in use.
If the user is using an external authentication provider that already has these controls, the authentication provider that must provide the rules.
MFA (Multi-factor authentication) authentication
Force Multi-Factor authentication to all users: By activating this configuration, all users, including the administrator, will have to immediately configure and use the MFA in senhasegura. Use carefully not to affect the current users sessions;
Force digital certificate authentication to all users: By activating this configuration, all users, including the administrator, will have to link a X.509 digital certificate in the login act;
Allow "Trust this computer" up to a maximum X hours: Once active and with hour range set, the MFA token won't be requested every login trial. This allows the tools that execute simultaneous logins in lots of terminals SSH;
Accept with tokens generated until X second change: Some devices are not configured on NTP servers, generating an interval of seconds that can affect authentication using TOTP. In these cases, set the accepted interval in this property;
Enable use of an external multi-factor authentication solution: Allows external providers SSO, hosted in cloud or on-premise, using protocols approved by senhasegura, are used as authenticators;
Password security level
Minimum characters for password: Minimum length for the user password;
Minimum numbers for password: Minimum number of numerical characters in the password composition;
Restrict password reuse: Does not allow password re-use by the user;
N last passwords that cannot be used: Number of passwords that will be considered by senhasegura to identify the re-use by the user;
Require symbols in the password: Indicates whether special characters must be used in the password composition;
Warning. The password security level settings are valid only when the default authentication provider is in use.
If the user is using an external authentication provider that already has these controls, the authentication provider that must provide the rules.
Access control by IP
Allows access or denial of access to IPS and network segments.
This list acts like an Allowlist or Denylist. Be very careful to not restrict administrator access that is creating the rules.
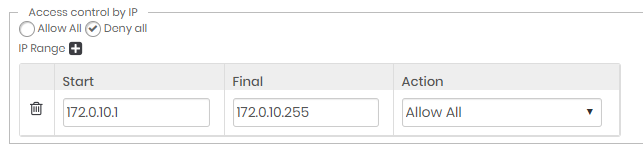
Creating Allowlist rules
In this scenario, senhasegura must be configured for Deny all access and accept only the access configured in the list.
Configure the general rule for Deny all, and in the IP list, configure the ranges with the Allow all rule.
With this setting, only the IPs on the list can authenticate in the senhasegura .
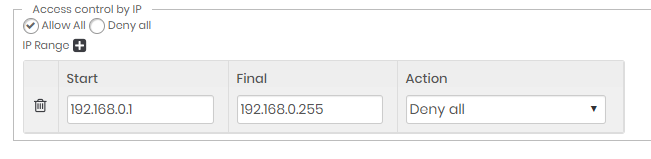
Creating Denylist rules
In this scenario, senhasegura must be configured for Allow all access and will block attempts from the IPs configured in the list.
Configure the general rule for Allow all, and in the IP list, configure the ranges with the Deny all rule.
Adaptive MFA by location
This parameter allows you to add for which IP range the MFA will be required or not, being able to Oblige MFA or Ignore MFA, based on the user's source IP. This rule applies to the following actions:
Login;
Session;
Withdraw.
If there are conflicting IP ranges, the first range in which the user belongs is considered.
This configuration overrides Force multifactor authentication for all users if the user's access IP is in any of the registered IPS ranges. The rule that will apply will be the one in Adaptive MFA by location.