Shared Information
In the Settings ➔ Access groups menu you have access to the access groups configured report for personal information. You can even create new access groups.
On the Access limitation tab is possible to restrict the information access by dates, days of the week and hours. In case an user that belongs to one of the access groups tries to access the information in date, day or time out of the restrictions configured, it will get an error message indicating restriction issue.
Unlike credential access groups, personal information access groups do not have a criteria tab. This means that only security policies and member users are configured.
The maintainer of the registered information has the power to decide on who that information will be shared for, not the access group administrator.
Note that by not having the criterion as an attribute of an access group, the name of the access group should reflect the security policies.
Registering a new Access Group
When clicking on the option to create a new access group, the Access group registration screen will open and there firstly, it's necessary to fill up the following fields and options:
Access group name: Name of the access group that matches the rules that this group applies. This makes easier understanding and auditing;
Description: a brief description of the access group;
Enabled: Whether the group is active or not. Disabling a group can reduce the amount of information the user has access to, or reduce the level of security required to access the information;
After filling up the initial fields and options, all other configuration options are separated by tabs:
Settings: Protected information settings
User can view the protected information: Flag if the protected information can be seen by the user;
It requires justification to view the protected information: Flag whether it is necessary to register a justification to see the protected information;
It requires an approval to view the protected information: Flag whether another user will need to act as an approver in order to see the protected information. Once active, you also need to set for how long this approval will be valid;
Approvals required for viewing: Number of approvals required to approve the operation;
Disapprovals required to cancel: Number of refusals to prevent operation;
Approval in levels: Flag if approvers will be triggered in levels. So you can set a hierarchy of approvers;
Users: Associate users to the access group that will have the role of operators.
ID: ID of the user to be added or removed;
Name: Name of the user to be added or removed;
Username: The username of the user to be added or removed;
E-mail: The e-mail of the user to be added or removed;
Approvers: Associate users that will have the role of approvers of the operations regarding the use of the information.
ID: ID of approver to be added or removed;
Name: Name of the approver to be added or removed;
Username: The username of the approver to be added or removed;
E-mail: The e-mail of the approver to be added or removed;
Access limitation: You can restrict the access group's acesss to the protected information by days of the week, time of the day and period (start and end date).
Registering Shared Information
Like personal information, shared information has the same protected attributes, and expiration information.
Its difference lies in the fact that the information holder configures which access groups will have access to information, without knowing who are the participants of these groups. In shared information, you cannot determine other users with edit power. All users with access will only be allowed to view the secret.
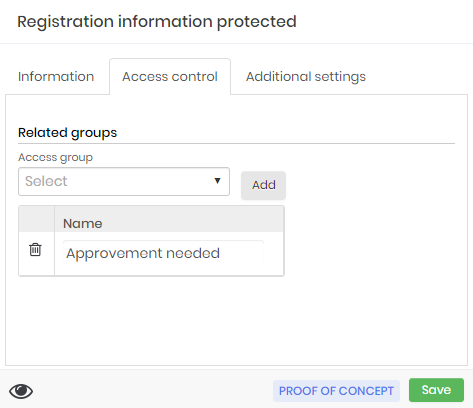
Once the information is registered, the secret holder can view the information and observe which users have access to the secret.