Additional Security Settings
Through the Settings ➔ System parameters ➔ Security menu you have access to additional security settings. In this screen you have access to settings that affect all system users.
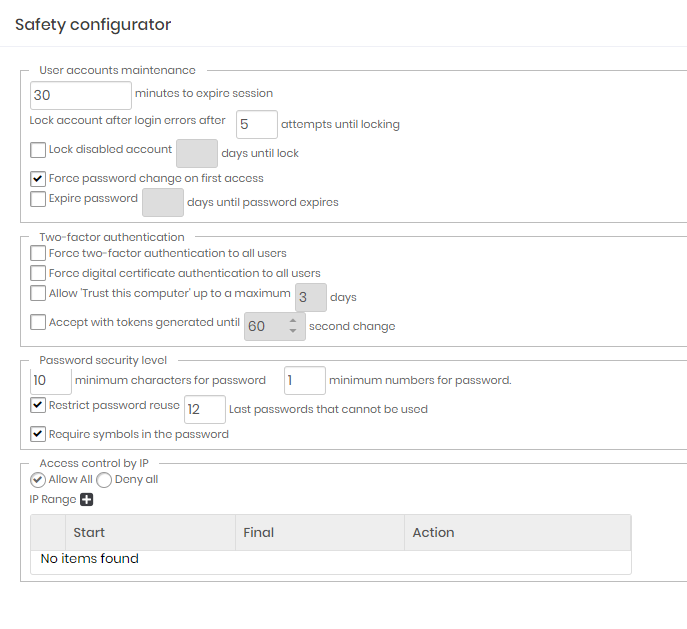
User accounts maintenance
Minutes to expire session: Inactivity time on the web interface so that the user session automatically expires.By default 30 minutes;
Lock disabled account: Flag to automatically block accounts that were not used after a range of days.Inactive by default;
Days until lock: Number of days to consider for an inactive account to be blocked;
Force password change on first access: Flag if the user must change his temporary password in the first access. Active by default;
Expire password: Forces the user's password expiration after a period of time. Inactive by default;
Days until password expires: Number of days for the password to expire automatically;
Warning. The Lock disabled account, Force password change on first access and Expire password configurations can only be used when the standard authentication provider of the senhasegura is in use.
If the user is using an external authentication provider that already has these controls, the authentication provider that must provide the rules.
Two-factor authentication
Force two-factor authentication to all users: By activating this configuration, all users, including the administrator, will have to immediately configure and use the MFA in senhasegura. Use carefully not to affect the current users sessions;
Force digital certificate authentication to all users: By activating this configuration, all users, including the administrator, will have to link a X.509 digital certificate in the login act;
Allow "Trust this computer" up to a maximum X hours: Once active and with hour range set, the MFA token won't be requested every login trial. This allows the tools that execute simultaneous logins in lots of terminals SSH;
Accept with tokens generated until X second change: Some devices are not configured on NTP servers, generating an interval of seconds that can affect authentication using TOTP. In these cases, set the accepted interval in this property;
Enable use of an external multi-factor authentication solution: Allows external providers SSO, hosted in cloud or on-premise, using protocols approved by senhasegura, are used as authenticators;
Password security level
Minimum characters for password: Minimum length for the user password;
Minimum numbers for password: Minimum number of numerical characters in the password composition;
Restrict password reuse: Does not allow password re-use by the user;
N last passwords that cannot be used: Number of passwords that will be considered by senhasegura to identify the re-use by the user;
Require symbols in the password: Indicates whether special characters must be used in the password composition;
Warning. The password security level settings are valid only when the default authentication provider is in use.
If the user is using an external authentication provider that already has these controls, the authentication provider that must provide the rules.
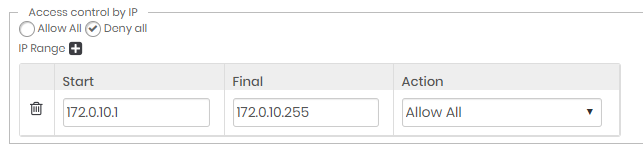
Access control by IP
Allows access or denial of access to IPS and network segments.
This list acts like an Allowlist or Denylist. Be very careful to not restrict administrator access that is creating the rules.
Creating Allowlist rules
In this scenario, senhasegura must be configured for Deny all access and accept only the access configured in the list.
Configure the general rule for Deny all, and in the IP list, configure the ranges with the Allow all rule.
With this setting, only the IPs on the list can authenticate in the senhasegura .
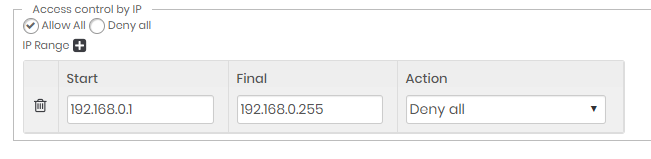
Creating Denylist rules
In this scenario, senhasegura must be configured for Allow all access and will block attempts from the IPs configured in the list.
Configure the general rule for Allow all, and in the IP list, configure the ranges with the Deny all rule.
chapterReview and Certification Review and Certification have the objective of guaranteeing that all access groups and users of senhasegura have the correct level of access, through periodic reviews. To bring more security to the platform, the review system is responsible for reminding the administrators of the access characteristics of each group, making sure that there is no extra access for any group, as well as checking that the users are correct. Not only the access groups but the users are also reviewed individually so that no old employee or one who has changed area continues with the permissions of the previous position.
Group Review
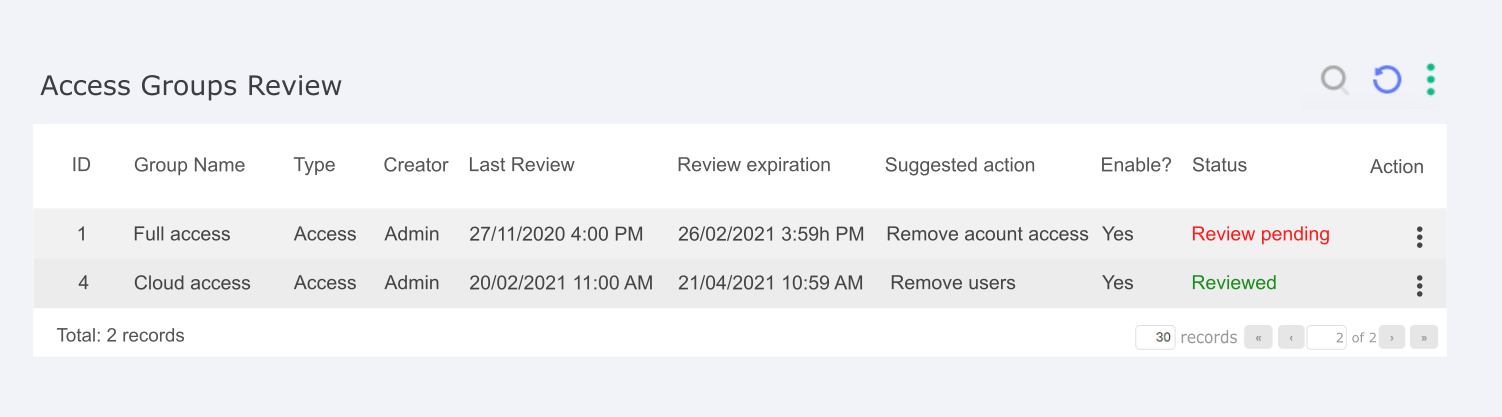
The group review is composed of a screen and alerts that allow administrators to always have control over all the group's characteristics. The screen is essentially made up of a report responsible for allowing the identification of the access group to which it refers and its review dates. The columns that constitute this report are:
ID: ID to identify the group;
Group Name: Group Name to identify the group;
Group Type: Group type are responsible for identifying the group;
Review Date: The Review date is responsible for identifying the date of that review;
Created by: Shows the creator username;
Creation Date: Creation date to identify the group;
Reviewer: The reviewer is responsible for indentifying the date of that review;
Last Revision: It is possible to see when was the last time the group was reviewed;
Expiration Date: This shows the next time the group must be reviewed;
Enable?: The Enable column lets you see whether the group remains active or not;
Status: The Status column is responsible for giving visibility to the status of that group's review, being "pending review" and "reviewed" the possible options, the first option takes the color red and the second green to help visualization;
Action Button: The action button appears whenever the review is pending, so the reviewer can click on it to review.
The Suggested Action column brings an action recommended by the system based on the information in that review, making it easier for the reviewer to judge. The options are based on quick tips such as:
Remove user: The suggestion is to check the users in the group, as there are users who have not logged on for a long time.
Remove account access: The suggestion is to check the accounts registered in the group, because some users have not used them for a long time.
Every group on its creation will have a pre-configured review time, the system default being 90 days, and this is the main trigger for the pop-up alert in the windows tray so that no review is forgotten and the security of the platform is threatened. Not only after the pre-set time, but alerts can also be set for other events such as the addition of new users to the group.
Users Review
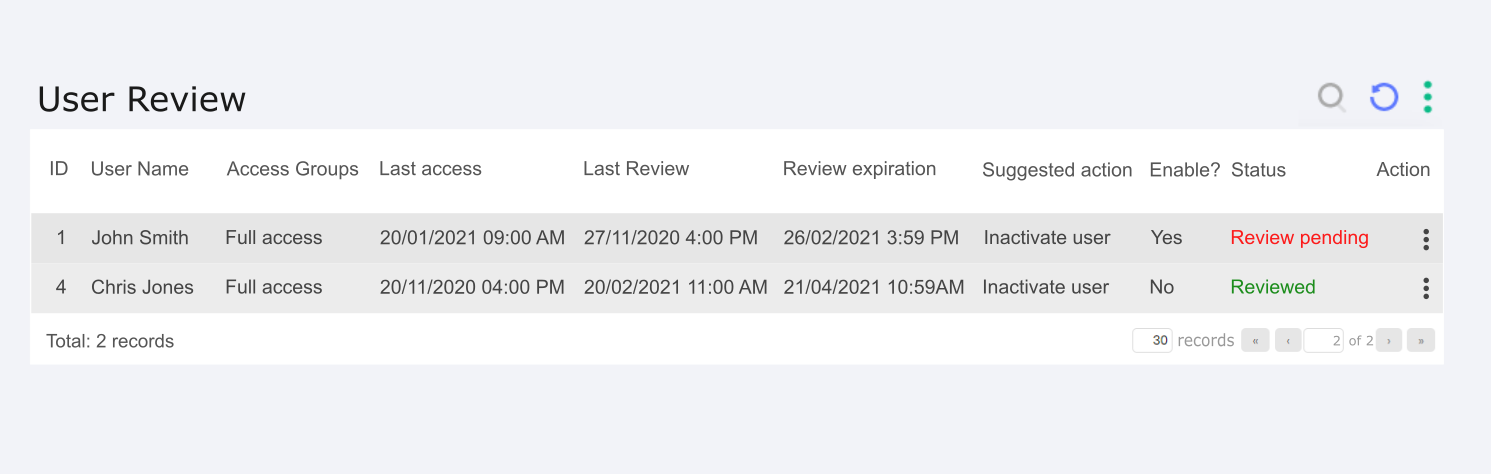
The user review is similar to the group review, with a screen and alerts. In the case of users, the report present on the screen has the following columns:
Date of last review: serve to alert you to the validity of that review and when you will need to review it again;
Review expiration date: serve to alert you to the validity of that review and when you will need to review it again;
ID: ID is the user identification;
User's name: User name is the user identification;
Access groups: Access groups is the group the user is a member of;
Last Access: Last access bring useful information for the administrator about the last access perfomed by the user;
Enable?: Enable bring useful information for the administrator, if the user is enabled in the system;
Status: The Status column is responsible for giving visibility to the status of that group's review, being "pending review" and "reviewed" the possible options, the first option takes the color red and the second green to help visualization;
Action Button: Action button are the quick actions Approve and Disapprove, as well as the possibility to see more details.
As with the group review, the Suggested Action column brings an action recommended by the system based on the information in that review, making it easier for the reviewer to judge. The options are hints to guide the reviewer such as:
Disable user: The user has not logged in for a long time and should be disabled
Remove from access groups: The user does not use the credentials of the access group they are in, so we suggest removing them.
Reviewing users will also generate alerts in pop-up form, keeping administrators up to date on which users need to be reviewed. The trigger for the review is mainly the review time that must be configured according to your needs, the system recommends 90 days. Other events can also be configured, such as a user inactivity limit.
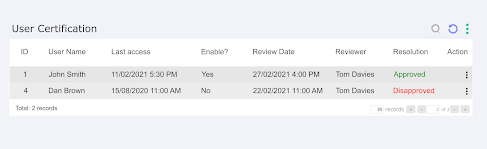
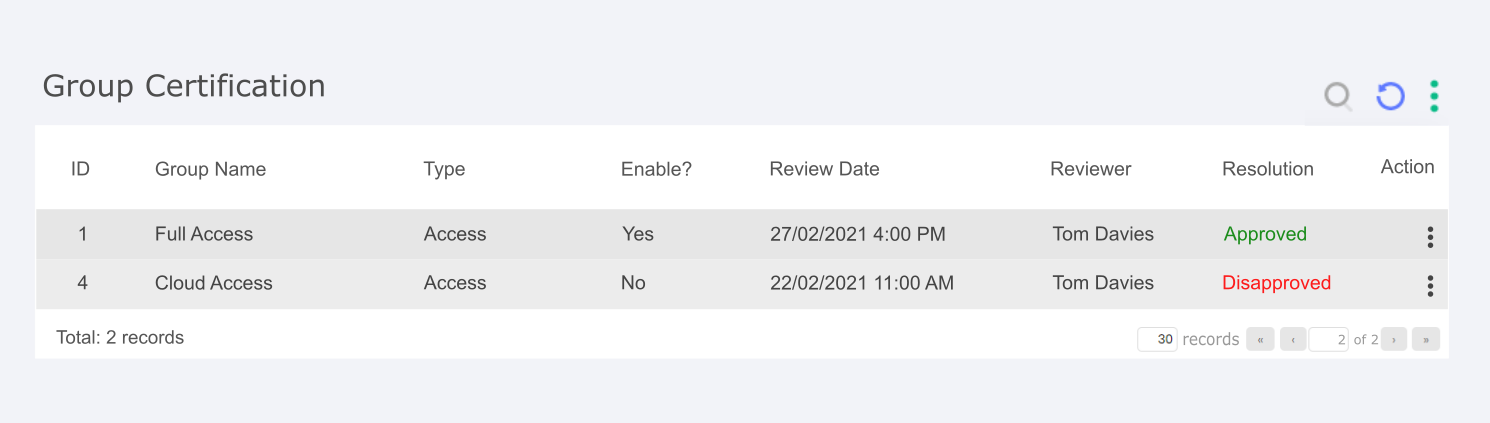
Certification
The goal of Certification is to ensure that the actions taken on reviews are correct, reversing them when necessary. It consists of two screens with reports that register all the actions taken on reviews by groups and users. This way the group in charge of certifying the actions can see information about each review and undo the actions taken, reactivating a user or deactivating an access group, for example.
The columns present in the group certification screens are:
Review Date: The Review date is responsible for identifying the date of that review;
ID : The ID is responsible for identifying the target of that review;
Group Name: The group name is responsible for identifying the target group of that review;
Group Type: The group type is responsible for identifying the group type of that review;
Enable?: Enable bring useful information for the administrator, if that review is enabled in the system;
Reviewer: The Reviewer is responsible for identifying the one who take de action;
Resolution: Resolution help to recognize the action taken by the reviewer;
Action button: In the Action button, we have the options of certifying the action taken or reversing it
For user certification, the columns are repeated except:
User Name: The user name is responsible for identifying the target user of that review;
Last Access: Last access help to recognize the last access perfomed by the user;
The certification actions are then saved in the screens' reports, reports that can still be printed and saved for future audit processes.