Password force
The strength of the password concerns the composition of the password that will be generated randomly and automatically by senhasegura in the process of password rotation.
It is possible to create several password strength settings based primarily on the password policies of the target devices.
It is important to know the different password rules of each manufacturer, creating a password force that does not match the password criteria of the application will give an unsuccessful password rotation attempts.
This isolation ensures that other devices that allow the use of larger, more complex passwords do not take the risks of legacy devices that accept, for example, only numeric passwords up to 5 digits.
Passwords can compose a maximum number of 256 characters. If the password strength setting is set to not allow duplicate characters, the maximum limit will be 70.
Creating new password strengths
Through the PAM ➔ Settings ➔ Credentials ➔ Password strength menu, you have access to the configured forces and the action to create new ones.
By default, the system already has 3 registered forces set up. You can register new forces through the form accessible by the New password strength report action.
The form allows you to configure the quantity composition of the following aspects.
- lowercase characters;
- uppercase characters;
- numbers;
- symbols. The only symbols allowed are in checkboxes for selection.
You can still determine whether character repetition is allowed. If your password uses more than 26 characters, more than ten numbers or more than 8 special characters, repetition is inevitable.
As additional security, senhasegura always validates that the username is not present in the generated password. Let's see some examples:
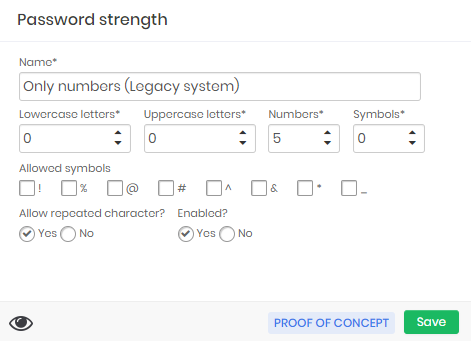
A weak password of a legacy system that uses only 5 numeric characters in its passwords
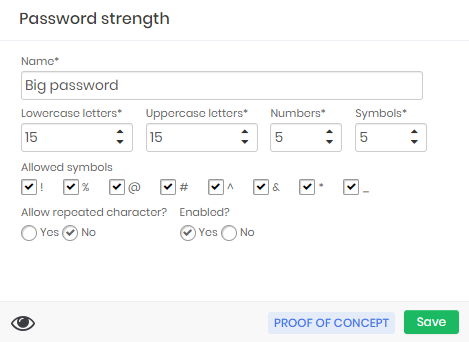
A password from a system that allows 40 characters in your password, varying between numbers, letters and symbols
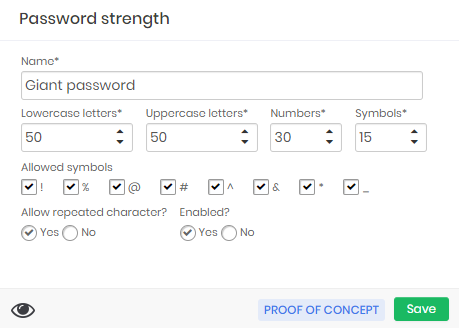
A password from a system that allows a password of 145 characters. In this case, repetition is inevitable
If you inactivate a password force that is already in use by some credential policy, that policy continues to use the same force even if it is inactive. This force setting will only not be available for new policies.
Always give a name that makes sense of password strength. Use names that lead to understanding the types of systems that should use this force. Legacy systems will generally be exceptions that force the administrator to create new password policies and forces.
Dynamic password creation
senhasegura provides the possibility of separate settings for managing Password Strength and Password Policy, and it is from Password Strength that the configuration settings for the generated passwords are defined.
The configuration of this strength can rely on combinations of lowercase and uppercase letters, numbers, and up to 8 different pre-determined special characters. Using these combinations, senhasegura can issue a password of up to 256 characters, ensuring that:
the username of the credential is not sequentially present in the composition of the password;
the generated password is not present in public password dictionaries;
the random password is unique for each credential.
Using randomization, the candidate character sets are then scrambled for each password character to be formed.
The Password Policy will ensure that password change triggers are adhered to. Being them:
Expiration time by period: Change over time even if users have not used the password;
Use in proxy sessions: Automatic password change for use in a proxy session, even without exposing its value to a user;
View by user: Automatic switch in cases where a user has viewed the password value.
In the automatic provisioning process or password change, the link of the credential with the issued password will only be perpetuated in senhasegura if the operation on the target device has been successfully completed.
A second password reconciliation process is used to ensure that the password managed by senhasegura remains identical to the credential password available on the target device.