Overview
This section will explain how to use, the senhasegura proxies.
Proxy architecture
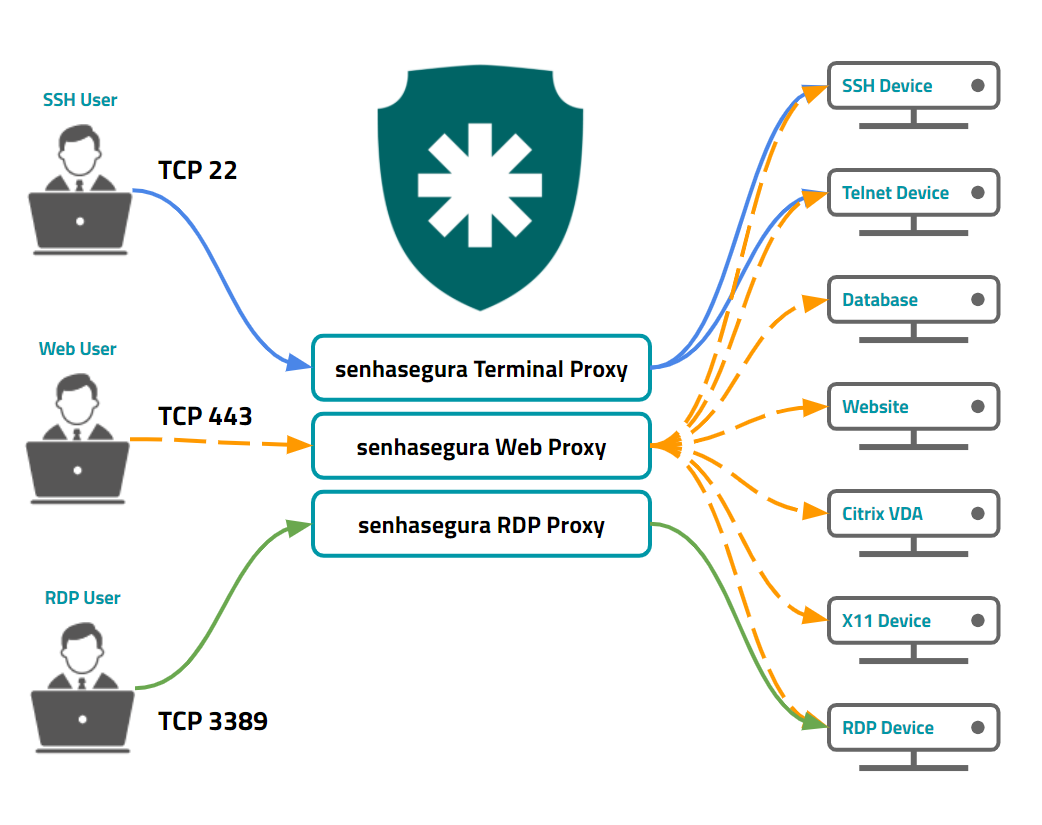
senhasegura gives proxy technologies to many target protocols and applications. And also gives to the user three ways to connect. Every gateway has its particular features, cryptography capabilities, segregations and session recorders.
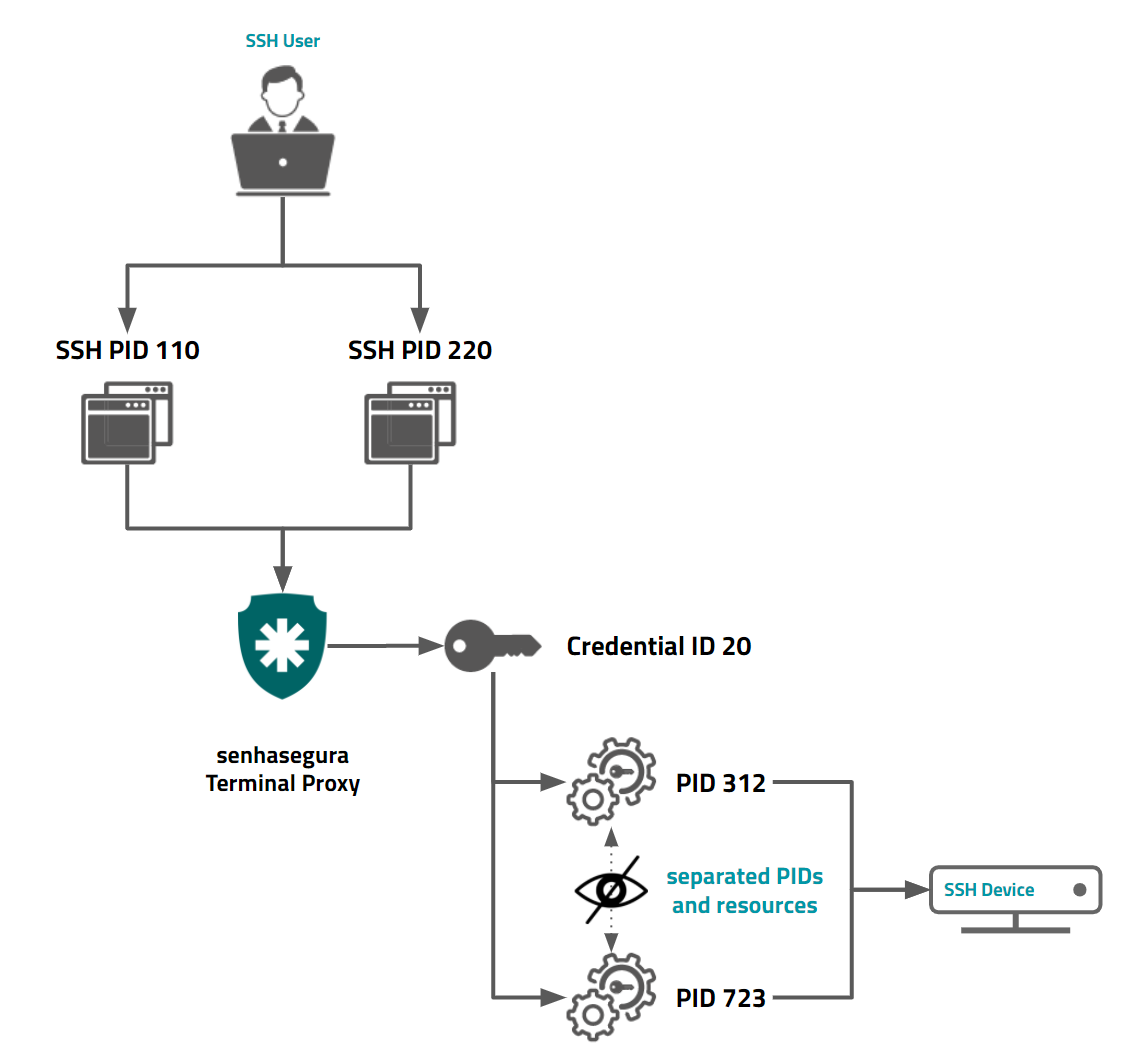
Each user session receive a separated internal PID running over security hardenize layers and abstractions using best CIS and NIST pratices. There is no possibility to share data between running sessions even when it comes from the same senhasegura user.
Proxy User Types
Proxy sessions have several functionalities that occur at different times, and that are performed by different types of users.
The types of users in a session:
Operator: It is the user who requests access and performs tasks on the target device;
Approver: The user who participates in the workflow process. It has the decision-making power whether or not the session can be executed;
Auditor: It is the user who observes the sessions that have already occurred looking for behaviors, commands or videos;
Administrator: It is the user who configures all options and functionality of a session and decides intervention actions into ongoing sessions;