Introduction
The Domum module is a "Remote Privileged Access" solution that offers the possibility for external hosts to gain access to an organization's internal resources, as well as providing a more secure home office environment for all of the organization's devices, controlling access by third parties and customers.
Without this kind of control and monitoring, one of the potential risks that organizations are vulnerable to is unauthorized access to enterprise resources, as a compromised server, for example, could be used to intercept communications and be a point of attack for other hosts within the organization.
Domum not only provides a secure external access for the organization but also an easy and fast procedure to grant external access to third-party users and employees because it is a VPN-Less solution, that is, the organization will not need to worry about setting up networks and VPNs for each user that needs to access the secure network from an external network, just configure their permissions in an access policy and give them a dedicated link for access.
That said, Domum can assist an organization in the following scenarios:
User origin management
Definition of remote access policies separate from other PAM users
Secure authentication with a dedicated link and token requirement
Visibility of remote activities
IT (Just In Time) accesses for third parties
Flexibility and possibility to expand operations around the world with governance through geolocation
Check out Domum's architecture below and, consequently, who the external hosts are and how access is made:
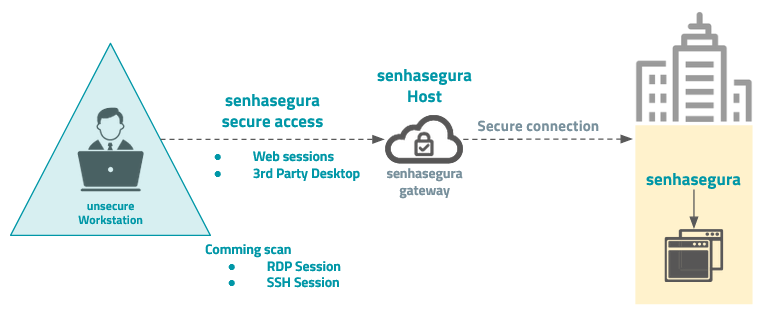
As presented above, Domum, through senhasegura , will provide secure access to Web sessions coming from third-party desktops, which in turn will connect to the senhasegura gateway1 through the HTTPS protocol without the need for VPN, which will then secure and provide access to the organization's internal resources.
In the Domum module, organizations can create their own Privileged Remote Access rules and execute and monitor them according to the needs of their respective operations.
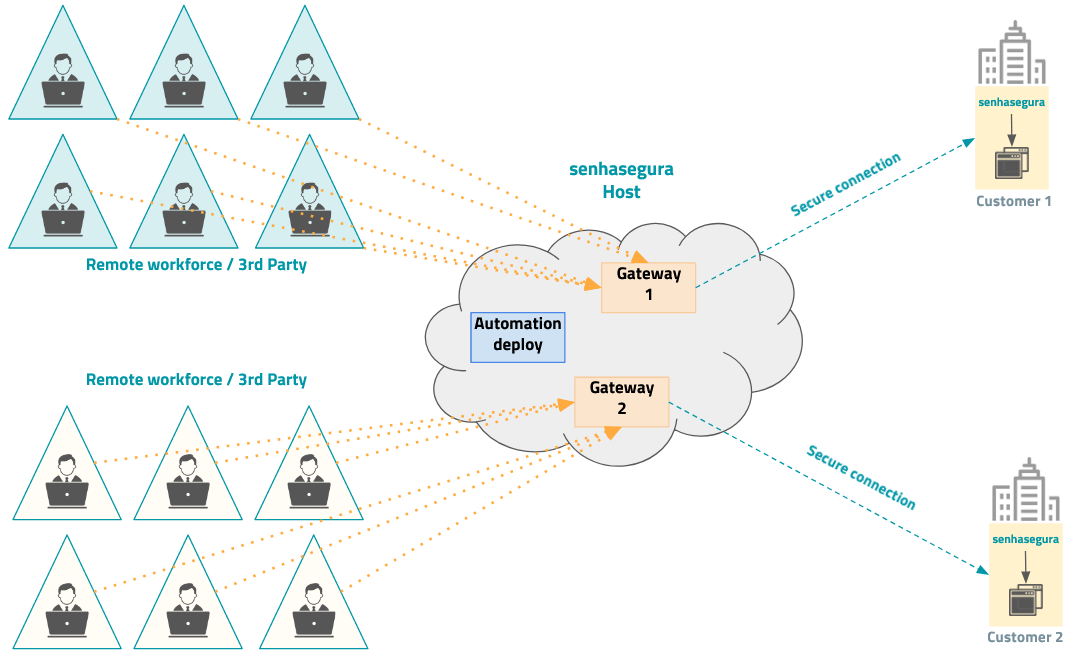
The figure below demonstrates how different organizations can use the Host senhasegura to reach their institutional senhasegura instances, without any conflict between the gateways.
Use cases
This section brings together the concepts presented in the previous sections and exemplifies how they can be adopted by the organization as needed for its policy and operations. The section refers to operating models to help the organization determine what types of external access approaches can be implemented. The approaches are as follows:
Third-party users: With the organizational network being such a critical asset, it is not ideal to grant external users access to it when their activities are restricted to only using the senhasegura . Even using methods such as VPN is still difficult to control and restrict access to just a few applications.
VPN-Less and Principle of Least Privilege: this type of user can have his access restricted to the Domum platform only, without ever having to be registered with senhasegura , receiving a link dedicated to his user for access to the platform. He will be able to visualize passwords and carry out remote access to the credentials assigned to him while working from home, from his own company's space or even from the organization where he provides his service, in an isolated manner from the network where the senhasegura is operating, using an access profile of an external user and minimal privileges.
External Access Policy: the organization must configure which assets the user must access and how this access can be carried out respecting the days and times determined in the policy.
Geo-location Blocking: Using the policy the organization can determine from which locations the request for access to Domum will be considered a secure request. For example, the access permission can be restricted only to the regions of the partner company where the third party user works and the organization where the user is providing the service. If the access to Domum comes from a region that is not authorized by the external access policy settings, the access will be blocked, regardless of whether the user has access permission or not.
Employees: this type of user may need access to the senhasegura to perform his activities when he is in working model that allows him to be outside his organization's premises, such as in his home environment or on a business trip. Users whose access to senhasegura is sufficient to perform their activities can be instructed to access the system through Domum, when they are not in the organizational environment, to save VPN resources, as well as restrict access only to the solution they need to use, senhasegura . In this way, the organization guarantees total access to your system through a safe and secure path, with a dedicated link that only that user can authenticate.
External Access Policy: employees of the organization that are performing their activities in an external network, the access group policies already applied in the PAM module are used during the access to the platform, ensuring that the policy already defined continues to be respected even in external access, i.e., when the user accesses the senhasegura through Domum the permissions and access group rules applied to his user remain the same.
Geo-location Blocking: Using the policy the organization can determine from which locations the request to use the Domum link will be considered a secure request. For example, the organization can determine that only the region where the employee lives or will travel for business are allowed regions. If the use comes from a region that is not authorized by the external access policy settings, the use of Domum will be blocked, regardless of whether this user has a registered user in the application and authentic permission.