Dynamic provisioning
To grant a high security level into elastic cloud Environment, the senhasegura DSM allows JIT automatic secrets provisioning and deprovisioning into cloud providers, environments and systems. This scenario is normally used at ephemeral and dynamics environments, where there is JIT secrets creation.
Configure dynamic access keys provisioning into Cloud Providers
Access keys are credentials used by applications and scripts to access services from cloud providers such as AWS, Azure, Google Cloud and others.
senhasegura DSM allows dynamic provisioning of access keys at major providers such as AWS, Azure and Google Cloud through provisioning profiles.
To create a dynamic provisioning profile, access the menu: Cloud ➔ Cloud IAM ➔ Dynamic provisioning ➔ Profile.
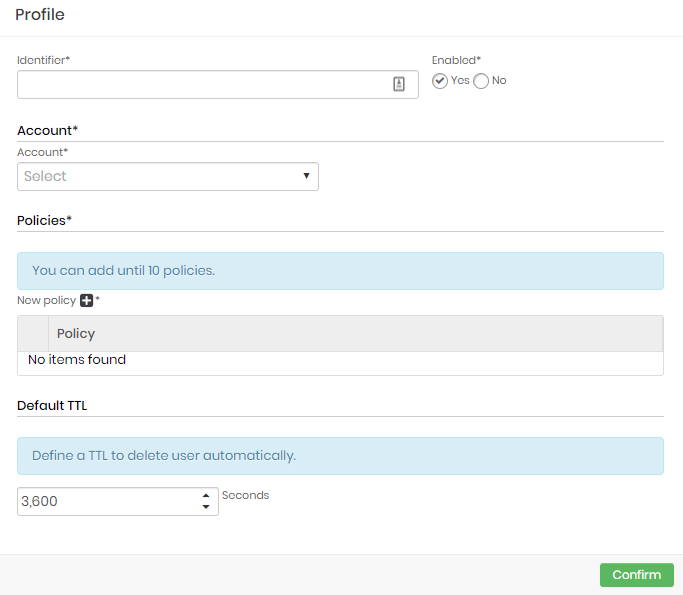
Click at Add profile button at report actions;
Fill the following fields;
Identifier: Enter an identifier to identify this profile into reports. User names will be composed using this identifier plus a time-based string;
Enabled: Flag if this profile is enabled for use or not;
Account: Set up a provider account where the users and access keys will be created;
Policies: Set up which policies this user will receive when created;
Default TTL: Configure the user life-time. After this time the user will be automatically removed from the cloud provider;
Click at Confirm button to finish;
After creating the dynamic provisioning profile for access keys, relate it to an application into DSM ➔ Applications ➔ Applications menu. Check out the dsm-create-automation section of this manual for more details.
Configure dynamic credential provisioning
senhasegura DSM allows dynamic credentials provisioning into many systems and devices such as databases vendors, such as MySQL, Oracle and SQL server, Linux and Windows servers and other technologies.
Access the Dynamic provisioning report at PAM ➔ Dynamic provisioning ➔ Profile menu.
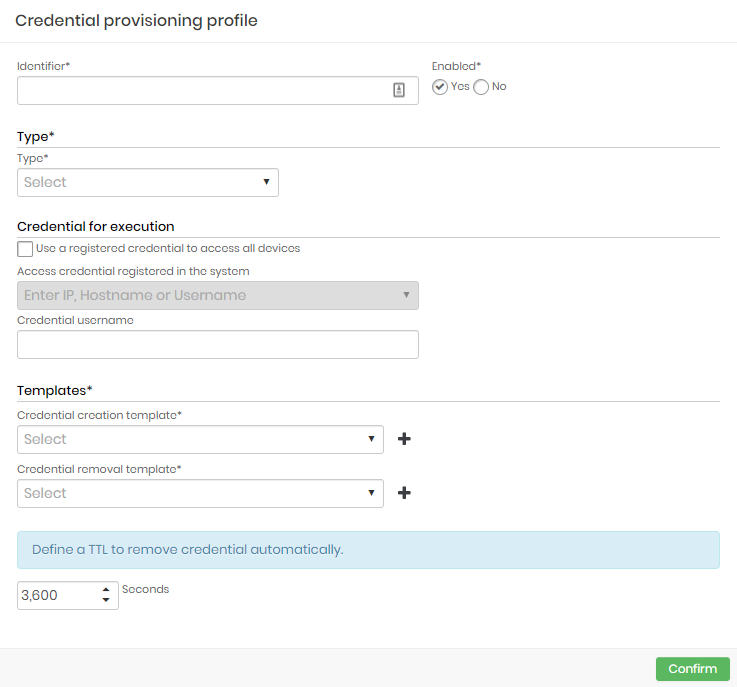
Click at the report action Add profile button;
Fill the following fields:
Identifier: Enter an identifier used to identify this profile into reports;
Enabled: Flag if this profile is enabled for use or not;
Type: Type of profile that represents the target device. There is only predefined options:
Linux;
MySQL;
Oracle;
SQL Server;
Windows;
Credential for execution: Define which credential should be used to connect to the devices where the profile will run;
Templates: These are the templates for the selected Type. It has the execution rules for some actions. Select from the options:
Credential creation;
Exclusion of the credential;
TTL: Define the credential lifetime. After the end of this period, it will be automatically deleted by senhasegura at the destination;
Click at Confirm button to finish;
After creating the dynamic credential provisioning profile, relate it to an application in DSM ➔ Applications ➔ Applications menu, editing an existing one or creating a new one. Visit the dsm-create-automation section of this manual to learn more details.
Dynamic secret provisioning
senhasegura DSM allows the dynamic secret provisioning in many devices, credential devices, and other services.
Access DSM ➔ Secret Management ➔ Secrets
When changing the credential password with a secret attached, the version of the secret will be updated. This change can happen manually or in an automatic way.