Administration
Operational screens
Operational screens are screens where the administrator can influence the behavior of the senhasegura.go installation.
As we have seen in the installation process, it is possible to deal with operations of the workstation where it is installed and separately with the user who is using it. Sometimes more than one user can use the same workstation. And the settings and operations of one user cannot affect the other.
Workstations Report
Through the menu go ➔ Workstations you can have access to the workstations that have an installation of senhasegura.go .
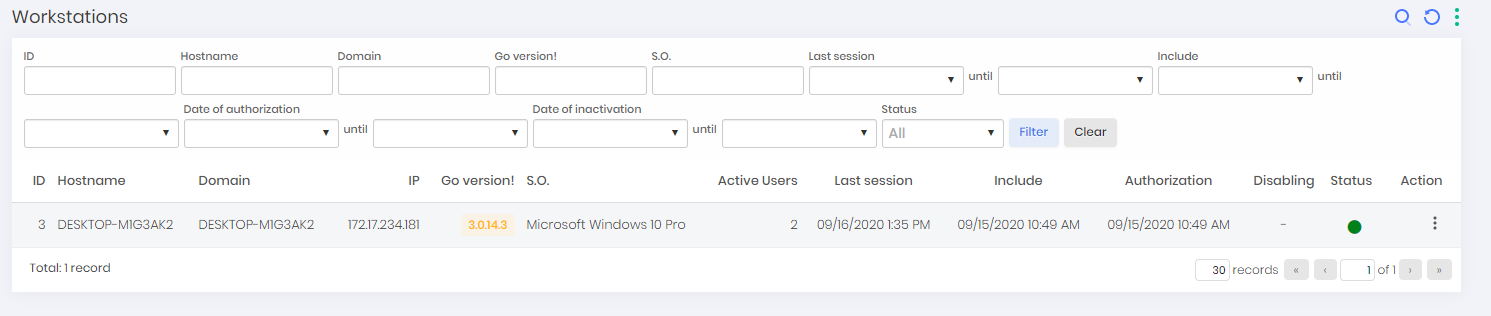
The registers are distinguished by their features, and have a color status indicator on the column Status. The values can vary from:
Pending (Orange): New installations that have not yet been approved or refused by the administrator. Not allowed to operate while there is no approval
Authorized (Green): Installations that have already been approved by the administrator and can use the features on the workstation;
Disabled (Red): Installations that have been revoked by the administrator. That is, they cannot operate the senhasegura.go ;
The Orange (Pending) status will only be displayed if automatic approval of workstations and users is not active. senhasegura by default comes with these options inactive, forcing the administrator to manually approve workstations and users.
This report does not have actions to add a workstation. One workstation is just added in case there is an installation with senhasegura.go activation enabled on the workstation itself.
Some registration actions will also vary depending on the status:
Detail: Presents the status dates of the workstation and its unique identifier. This unique identifier is used for in-depth diagnostics by our support team;
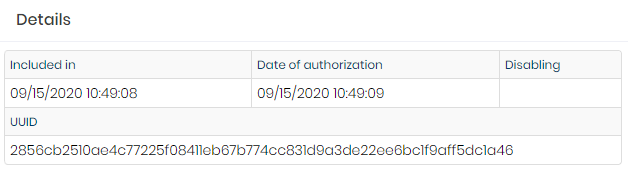
Detaisl report Users: Presents the list of users who ran senhasegura.go on this workstation. This report will be explored further;
Events: They are all events captured by senhasegura.go services or executed by users through senhasegura.go in this workstation. This report will be explored later;
Disable: Present only in the Authorized state, this action inactivates the use of senhasegura.go in the workstation;
Authorize: Authorizes the use of senhasegura.go on this workstation. This the present status;
Users Report
Through the menu go ➔ Users, you can have access to the users that have used senhasegura.go . This report allows the administrator to filter by fields that allow crossing different origins and identify the different connections between the senhasegura users and the workstations where they made use of senhasegura.go .
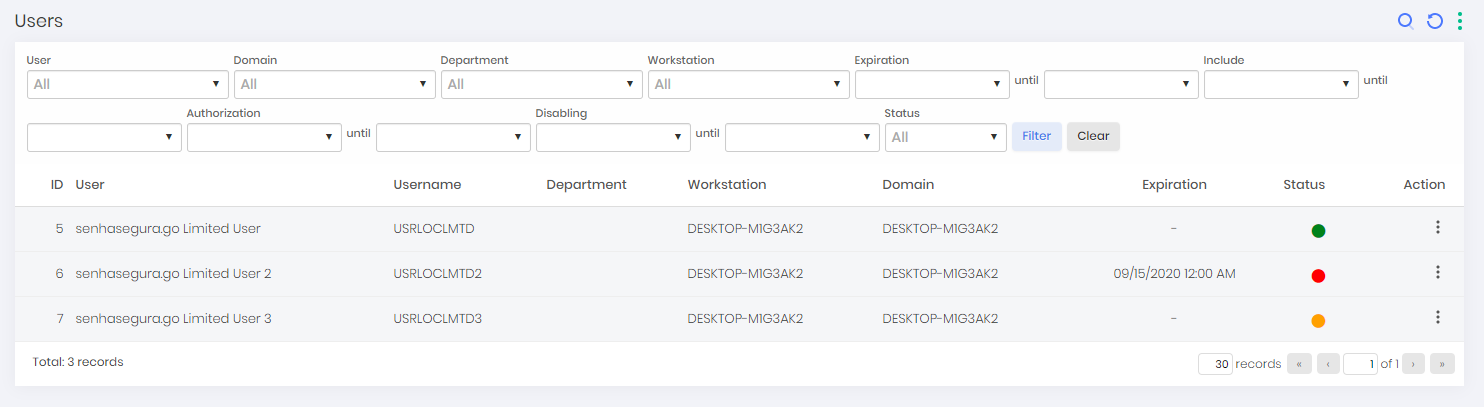
The Status field, just like in the workstation report, shows the status of this user on that particular workstation. Therefore, a username may be enabled to use the senhasegura.go on one workstation and be prohibited to use on another workstation.
Pending (Orange): Users who have not been evaluated by the administrator to use senhasegura.go . Not allowed to operate while there is no approval;
Authorized (Green): Users who have been approved by the administrator and can use the features on the workstation;
Disabled (Red): Users who have been revoked by the administrator. That is, they cannot operate the senhasegura.go ;
It is not possible to add new registers through this report. The user registration just occurs in case a user makes use of senhasegura.go on a workstation where senhasegura.go is installed and activated.
Actions per record may vary between:
Authorize: Present in Pending and Disabled status, it allows the user to use the senhasegura.go . You can indicate an expiration date of this approval, which after expiration, automatically will be the approval will be revoked
Revoke: Present in Pending and Authorized status, refuses the use of this user's senhasegura.go on the workstation. This does not prevent the user from making a new request on another workstation. The refusal will also not be expanded to other valid approvals this user has on other workstations and will also not disable the use of the workstation for other users;
Detail: Presents this user's details regarding approval, inactivation and inclusion dates;
Applications and Uninstallers Report
In the menu go ➔ Applications you can view all applications that have already been automatically mapped by the services of senhasegura.go , or executed by users through senhasegura.go .
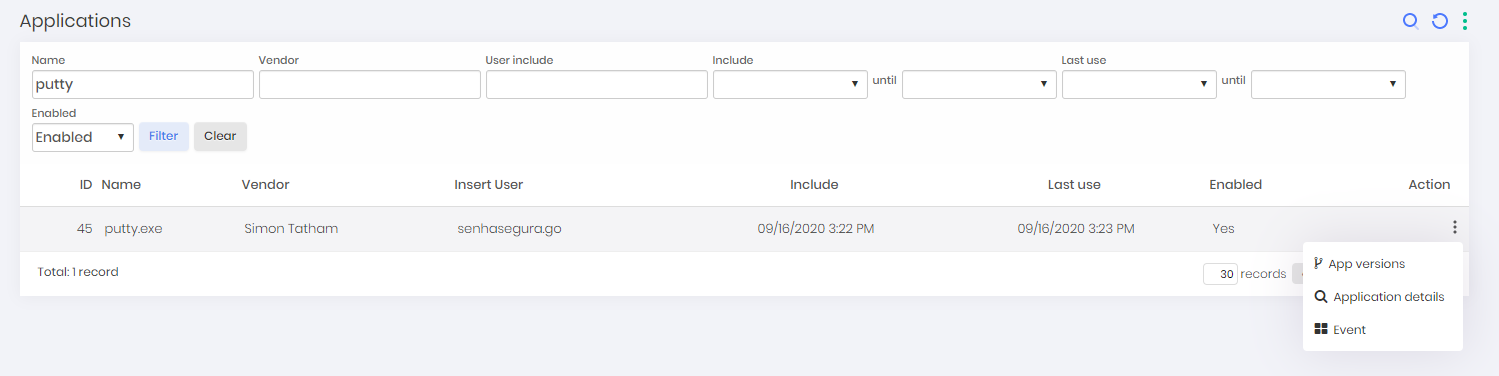
An application is unique to the senhasegura , regardless of its installation folder and the name of its binary. This way, senhasegura.go is able to identify its different versions and centralize the registration to create the segregation.
This also allows the administrator to identify the different versions installed in your machine park. Its registration actions also allow visualization of execution events.
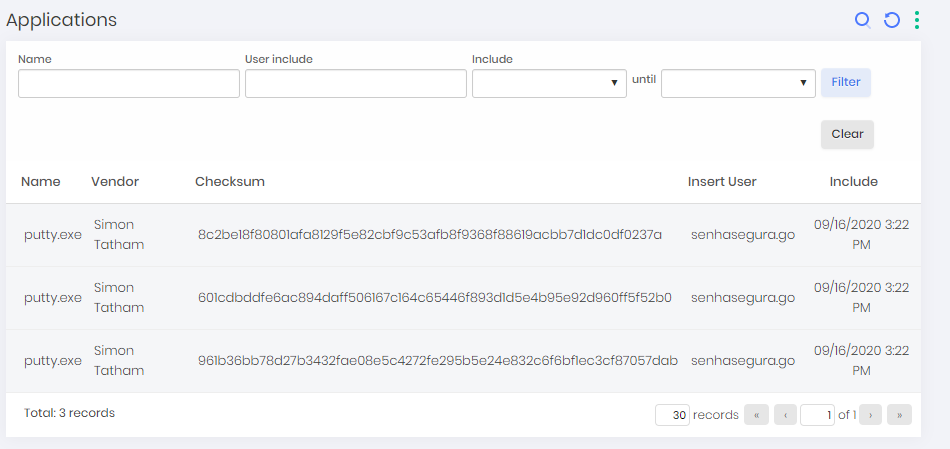
In the menu go ➔ Uninstallers there is a list of all uninstallers of applications identified in workstations.
Because they are also applications, their registration actions are identical to the actions of the application report.
Control Panel applet report
The Control Panel applets are pre-configured. This is necessary because Microsoft has different ways to access the controls for each Windows version.
You can access the controls through the menu go ➔ Control panel.
In this report you can observe each command used to achieve control, and which Windows versions are compatible.
The registration action presents a report with all events from when a workstation executed the high access control.
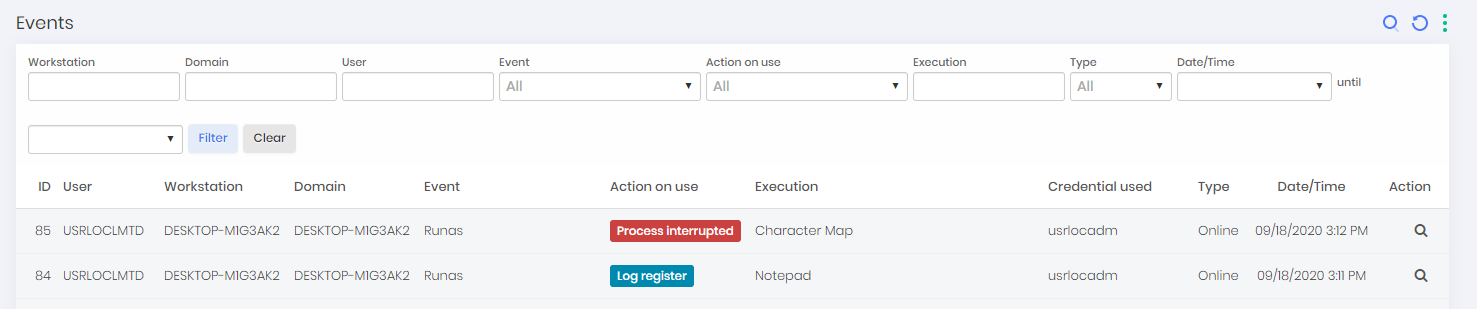
Event Report
This report is present as a detail in all records of the Workstations, Applications, Uninstallers, Control Panel reports and DLLs.
In this report, each automatic or intentional action of the user is centralized from senhasegura.go . When accessed as detailing, you have the filtered and reduced view of the source entity. But accessing through the menu, you have access to all filters and the possibility of combinations to identify the events that are occurring in workstations.
In the action field is possible to change permissions of a previously executed application by the user, restricting or allowing the application so that the user will or won't be able to use this tool again in a future moment.
DLLs included only after starting the process will be analyzed. If a user tries to open a file that has any DLL that is considered untrusted, the system will generate an event called Untrusted DLL execution attempt and will turn off the application. The event will be notified via SYSLOG and available to an e-mail configuration.
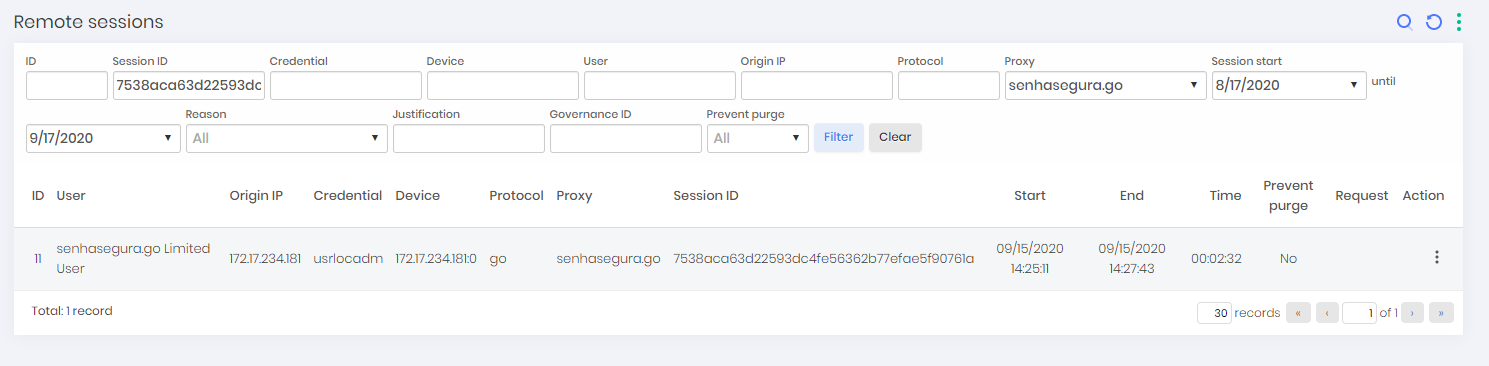
Report on elevations and videos
When a user performs an elevation of an application, senhasegura will record a video while the thread of that application is active. As soon as the thread is finished, the video is sent to the senhasegura server and becomes available for evaluation.
Like all recorded sessions, it can be accessed in the menu PAM ➔ Access control ➔ Remote sessions. You can filter through the Proxy filter with the value senhasegura.go to list only the sessions coming from senhasegura.go .
Through the register action Video of session you can watch the video.
This feature will only be available if the Enable recording session parameter is active.
Workstation Access History
Through workstation access history located in Go ➔ Reports ➔ Workstation Access History, it will be possible to verify how many access, the last and the first access of a determined user on a determined workstation. It is possible to filter by user, access, date, time, and ID.
Configurations and segregation
By default, some features of senhasegura.go are inactive. You must activate them manually to use them.
Global settings
The parameters can be accessed through the menu go ➔ Settings ➔ Parameters or Setting ➔ System parameters, and finally by accessing the go tab.
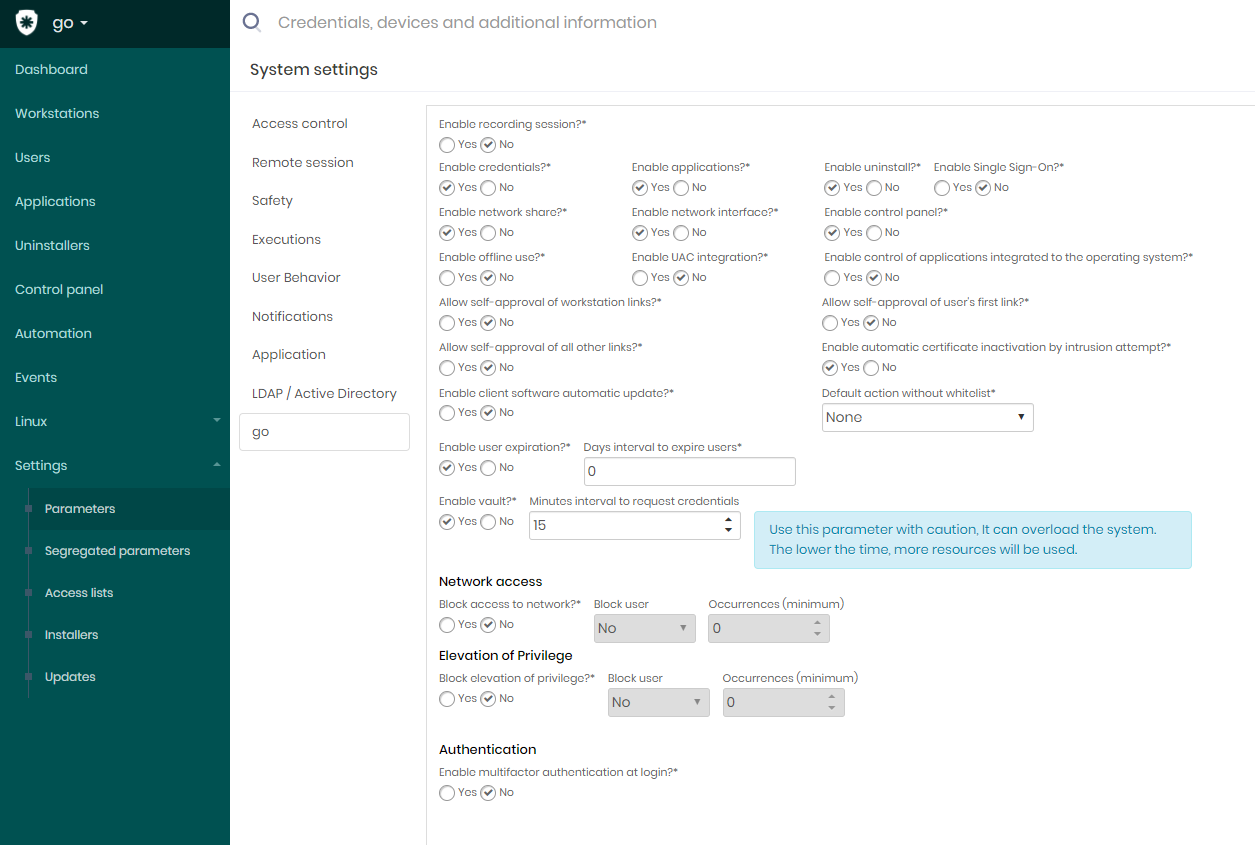
All parameters on this screen are of global level, that is, valid for all users. We will talk later about segregation that allows us to create different combinations of settings for each workstation or users.
The parameters are separated into sections:
Modules
The module settings control the display of the senhasegura.go respective sub-modules. They are:
Enable credentials;
Enable applications;
Enable uninstall;
Enable network share;
Enable network interface;
Enable control panel;
Installation settings
The Installation settings control the installation settings for senhasegura.go client.
Allow self-approval of workstations links: Indicates whether a workstation should be automatically approved when receiving a valid license from senhasegura.go ;
Allow self-approval of user's first link: Indicates whether the first user should be automatically approved if you use the senhasegura.go on a previously approved machine;
Allow self-approval of all others links: Indicates if all other users who come to use senhasegura.go on a previously approved machine will also be automatically approved;
Enable client software automatic update: Indicates if the senhasegura.go should be automatically updated if a new version is available on the server;
Enable user expiration: Indicates whether it will be mandatory to set an expiration date for the user's authorization;
Days interval to expire users: It will be the number of days that the user will expire after approval. This value will determine the end date on the user approval form;
General settings
The general settings are a generic section in the settings for senhasegura.go client.
Enable recording session: By default inactive, it indicates if the recording of high applications should be recorded on video during its execution. At the end, the video will be sent to the senhasegura server;
Enable Single Sign-On: If active, it allows the senhasegura.go to start an authenticated session of the senhasegura web in the user's default browser, without the user having to enter a password. If the user is required to have a 2FA token, it will be requested in the web system;
Enable UAC integration: If active, the senhasegura will intercede at UAC moments allowing the user to type a credential that can continue the process;
Enable control of applications integrated to the operating system: If active, senhasegura.go will activate the driver that monitors the applications running in Windows and will interfere if the application is outside the allowlist or inside the denylist. Only applications from user sessions will be evaluated;
These parameters are linked to the installation and approval process:
- Enable automatic certificate inactivation by intrusion attempt: Indicates if the single communication certificate between workstation and server will be inactivated in case the server detects an intrusion in the senhasegura.go ;
These parameters are linked to special features of senhasegura.go :
Enable vault: Indicates whether the senhasegura.go Offline is allowed. This feature will be discussed in more detail later on.
- Minutes interval to request credentials: While the workstation is online, a secure cache of credential information will be updated within this time frame.
Block access to network: Indicates whether the user will be blocked from any attempt to access a TCP or UDP network address.
Block user: Indicates if the senhasegura user linked to the action will be blocked after exceeding a number of network access attempts;
Occurrences (minimum): These are the quantities of times to consider before blocking the senhasegura user;
Elevation of privilege: Indicates if the senhasegura will monitor applications that try to execute privilege elevation outside the senhasegura.go . If active, the attempt will be prevented.
Block user: Indicates if the user senhasegura linked to the action will be blocked after exceeding a number of elevation attempts;
Occurrences (minimum): These are the quantities of times to consider before blocking the user senhasegura ;
Enable multi-factor authentication at login: If active and the user linked to the senhasegura has 2FA token configured, this token will be requested when performing local login on the workstation or access via RDP;
Enable JIT access: If active, the user using senhasegura.go will be added to the local Windows administrators group and their actions will be audited by video while they remain in this group.
If the user exits the JIT using the same activation button, perform a log off, or shutdown the computer, the user will be removed from the group immediately;
Segregated configurations
Segregated settings are used especially to deal with specific scenarios of a workstation. Sometimes the workstation belongs to a user who demands special attention or a differentiated use.
All previously seen settings are from a global context. That is, once determined it will be valid for all users. The administrator can then define a restrictive strategy at a global level and create permissive exceptions in a segregated context. Or, create a permissive context at a global level and create restrictive segregations in a segregated context.
To access the segregation settings, access the report in the menu "go ➔ Settings ➔ Segregated parameters". You can change an existing segregation in the "Edit" register action or create new segregations in the New segregation for workstation report action.
The configuration of a segregation should have the descriptive name for its purpose, to facilitate the tracking of a certain behavior of a workstation. For example, a configuration that requires the use of the 2FA token, should have in its name something like "Mandatory use of 2FA". This way, if any workstation presents this behavior, it is possible that it is within this segregation.
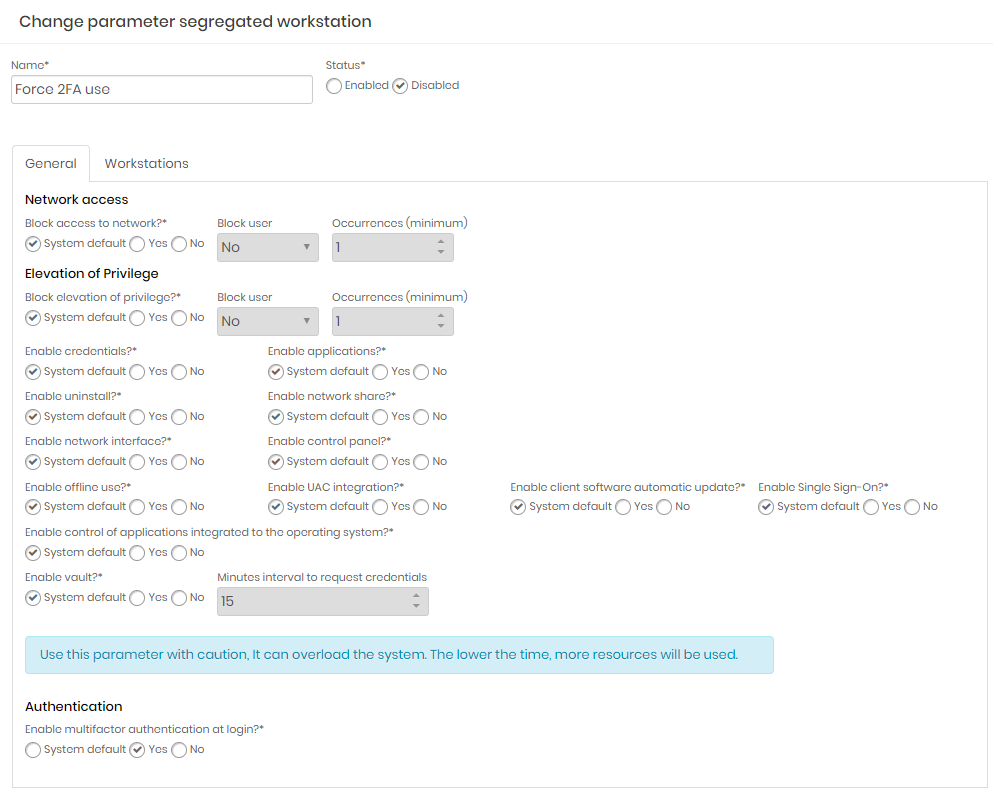
The configurations are similar to the global settings. The only difference is in the possibility of maintaining the value of the global settings or setting a fixed value that will take precedence over the global value.
System default: It will use the value from the global settings;
Yes or No: Overlap the value of the global settings by the chosen value;
After creating the rules on the General tab, it is necessary to save the record before linking the workstations on the Workstations tab. When you return the saved setting, go to the Workstations tab and add the workstations that will have the global settings overwritten by segregation.
Segregation will only be applied to the client when the application is started. In case of a segregation change, the user must load the application again for the new rules to be applied.