Authenticators
Authenticators provide a secure way to guarantee trust between different applications for the purpose of exchanging secrets and to manage applications, authorizations and related functions. DevOps Secret Management module provides integration with the most used authenticators as described in the following section.
OAuth 1.0 Authenticator
OAuth 1.0 is an authentication method that consists in using a set of Consumer Key, Consumer Secret, Access Token and Token Secret to identify and authorize an application access. When using OAuth 1.0 as authentication method make sure to select HMAC-SHA1 as Signature Method and 1.0 as Version. Also make sure to provide Timestamp, Nonce and a Signature since they are mandatory.
Configure OAuth 1.0 Authenticator
To use OAuth 1.0 as authentication method for an application follow the menu DSM ➔ Applications ➔ Applications.
- Edit or create an application and select OAuth 1.0 as authentication method;
- Provide the required data in case of a new application as mentioned in the Applications guide;
- To finish, click on Save;.
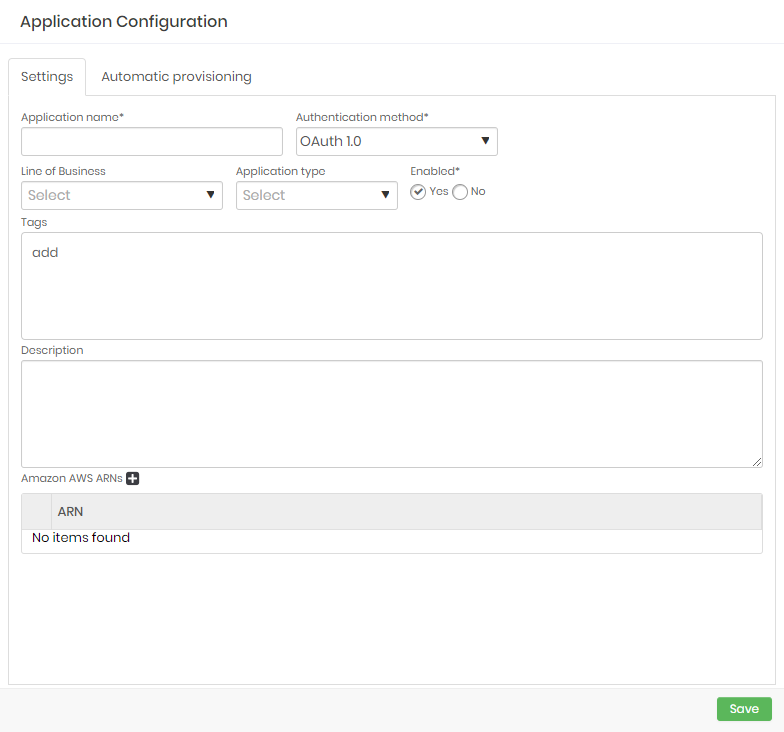
When a resource needs to retrieve data from a secret, it can use its OAuth 1.0 tokens to request the information from senhasegura DSM. If the data provided is valid, DSM will authorize the application to access its secrets.
Use always modern authentication types that guarantee data integrity. The possibility of authenticating through OAuth 1.0 exists due to the impossibility of updating legacy applications and senhasegura strongly discourage its use.
For more information on how to retrieve the tokens depending on the configured authentication method, please check the Authorizations guide.
OAuth 2.0 Authenticator
OAuth 2.0 is an authentication method that consists in using a Client ID and a Client Secret to request a time limited token and use it to access senhasegura resources. When using OAuth 2.0 as authentication method make sure to select Client Credentials as Grant Type.
Configure OAuth 2.0 Authenticator
To use OAuth 2.0 as authentication method for an application follow the menu DSM ➔ Applications ➔ Applications.
- Edit or create an application and select OAuth 2.0 as authentication method;
- Provide the required data in case of a new application as mentioned in the Applications guide;
- To finish, click on Save;.
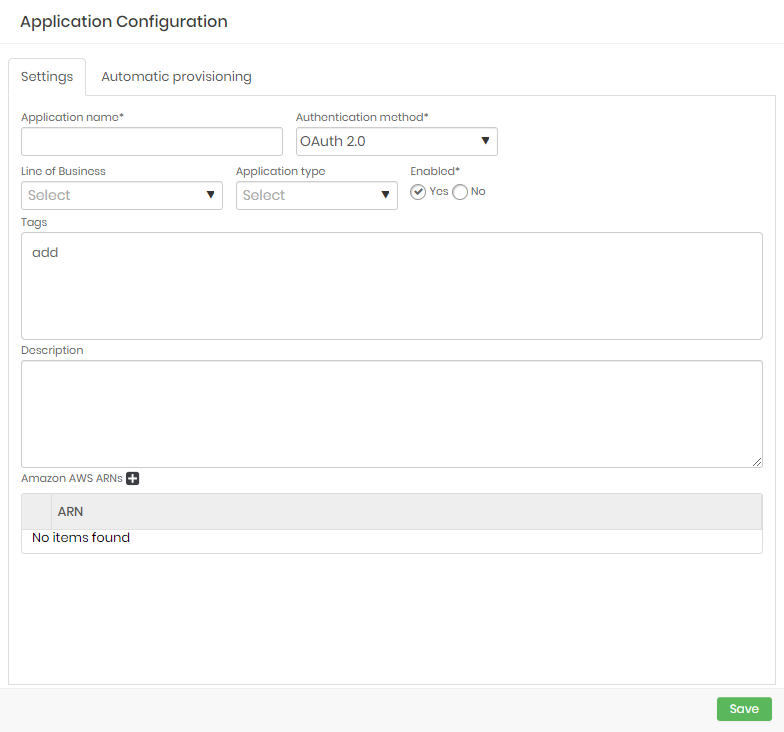
When a resource needs to retrieve data from a secret, it can use its OAuth 2.0 clients to request an time limited token and use it to request the information from senhasegura DSM. If the token provided is valid, DSM will authorize the application to access its secrets.
For more information on how to retrieve the tokens depending on the configured authentication method, please check the Authorizations guide.
AWS Authenticator
AWS is an authentication method that enables applications to retrieve stored data through the use of AWS Access Keys ID and Secret Access Keys together with a unique key generated by senhasegura DSM.
Configure AWS Authenticator
To use AWS as authentication method for an application follow the menu DSM ➔ Application ➔ Application.
- Edit or create an application and select AWS as authentication method;
- On the Amazon AWS ARNs section, provide a valid credential ARN;
- Provide the required data in case of a new application as mentioned in the Applications guide;
- To finish, click on Save;.
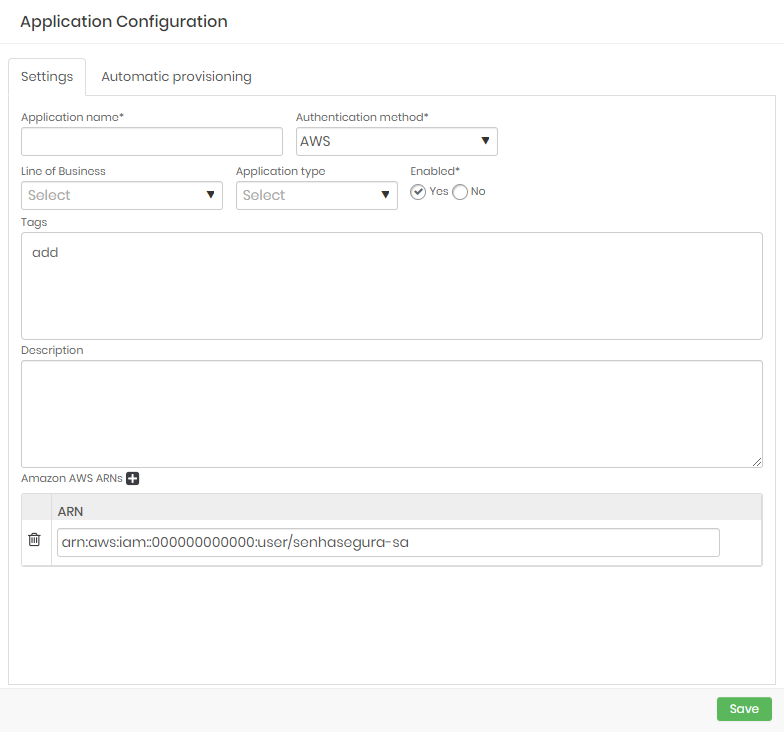
When a resource needs to retrieve data from a secret, it can use its AWS Access Key ID, Secret Access Key and a unique key generated by senhasegura DSM to request the information from senhasegura DSM. Once the request is sent, senhasegura will validate if the provided information matches based on the AWS ARNs configured in the application and if it does, DSM will authorize the application to access its secrets.
For more information on how to retrieve the tokens depending on the configured authentication method, please check the Authorizations guide.
DSM uses Programmatic Access to check if the provided information is valid. For more information on how to generate an AWS Access Keys, please visit the AWS Understanding and getting your AWS credential: