Registering Credentials
The limit of Credentials to be registered in senhasegura depends on the licensing contracted. Contact the senhasegura Support for more information.
The credential can be registered via the shortcut in the quick actions menu, or through the Credentials ➔ All report.
To register a credential it is mandatory to fill in the fields Username , Password type and Device . Let's understand each tab of the form and its fields.
Credential settings
At the information tab we have the following fields:
Username: It is the credential username. Must match the credential on the remote system;
Password type: It is the credential type. You can register new types through the Settings ➔ Credentials ➔ Credential types menu; The Domain user type enables proxy use of the credential on other devices. But it is necessary to inform the domain in the field Domain ;
Domain: Credential domain;
Device: Device that holds the credential;
Additional information: Additional information that complements the use of the credential on the target device. This field is available for use in automated password exchange, RemoteApp macros, and database connections; In the case of database connections, the name of the database must be populated in this field;
Status: Flag whether the credential is active for use or not;
Password: Credential password up to 256 characters; If automated password change is configured, this limit will be reduced to 70 characters to prevent character repetition;
Set current password: Indicative that the user wants to change the value of the password that is already registered in senhasegura . For new registrations, allows the editing of the password;
Show password: Display the password plaintext during editing;
Generate password: Will generate a random password respecting the password strength described in the table below the form;
Tags: Identifiers for credential segregation;
Note that there is a section named Password policy from this settings senhasegura determines how the password will be generated and used in automated exchanges.
Execution settings
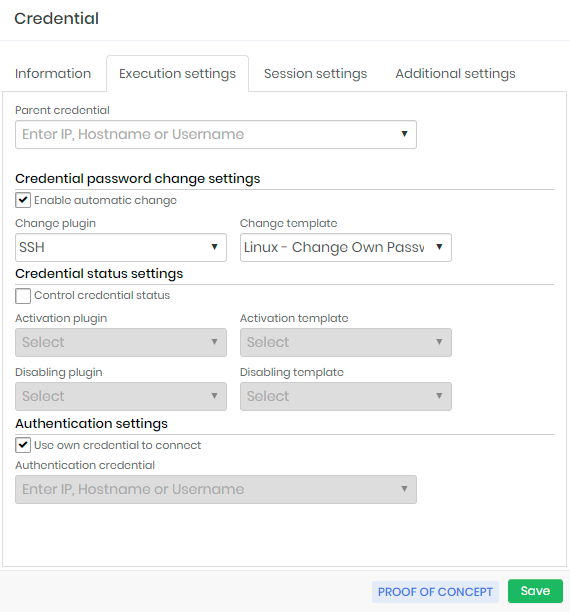
The Execution settings tab contains the configuration to the credential automated password change procedure.
Parent credential: When selecting a credential to be Parent this credential will always change the password to match the same for the Parent password. It works as a password change chain, where the change of a parent credential initiates the process of all its child credentials password.
The existence of a parent credential does not prevent the child credential from being changed manually or automatically;
Credential automatic password change settings
Enable automatic change: Flag to enable automatic credential change using Password policy rules;
Change plugin: The plugin will be used by senhasegura to connect and run the commands into the device to perform the password change.
Change template: Here is an Execution Template that will be executed by the executor plugin.
:::info senhasegura is installed with more than 250 templates out-of-the-box. And inside senhasegura PAM Solution our clients and partners can be updated with more templates developed by the senhasegura team and partners community. :::
Authentication settings
Use own credential to connect: Flag whether the credential itself should be used to connect to the device to perform the password change;
Authentication credential: If the credential itself is not used to perform the automated change, you must indicate which credential will be used to connect to the device; You can use a credential to connect to the device and still use your target credential to perform the change. This is possible due to the template system;
Session settings
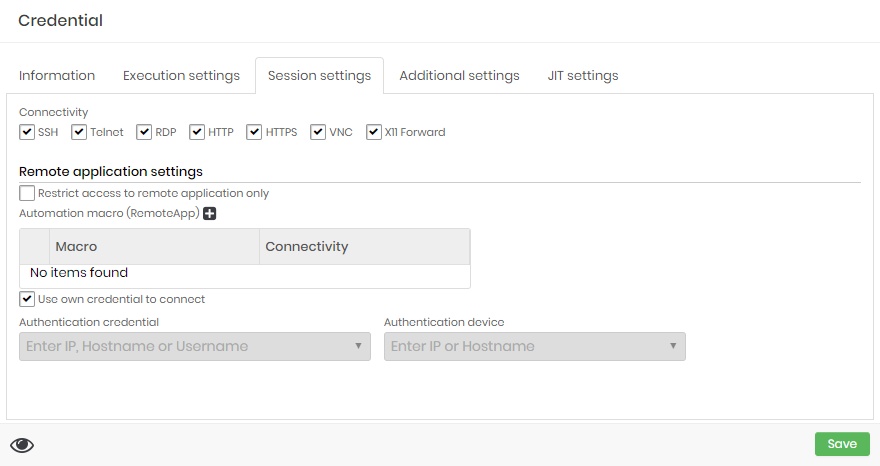
At this tab you can configure the usage of this credential at proxy sessions.
Connectivity
You can select which protocols this credential can be used. The target device also need be configured with one or more selected protocols to enable this credential for proxy usage.
Remote application settings
At the same Session settings you can configure RemoteApp settings for this credential.
Restrict access to remote application only: If active, the credential can only be used for RemoteApp proxy sessions. You cannot use a proxy session that delivers the desktop or terminal of the device. This does not prevent password withdrawal;
Automation macro RemoteApp (grid): You can relate which RemoteApp macros are linked to the credential and available to proxy users; :::info For a complete list of supported protocols and ports, see: Technical Specification. :::
Use own credential to connect: Flag the same credential will be used to authenticate to the target device and RemoteApp;
Authentication credential: If the authentication credential on the device is different from the RemoteApp credential, indicate which credential will be used in the authentication step;
Authentication device: The device where the credential will be authenticated and the macro will run. If filled, the original credential device we are registering will be ignored;
You can complete the registration of the credential through the Save button.
Now senhasegura will process the access groups that allow the viewing of the credential and make available to users. Every stage of registration is reported by SIEM. If a manual password change occurs, the child credentials won't be notified.
Additional settings
In the Additional settings you can set the following:
Identifiers (for web services): Alias to identify the credential when triggered via A2A web services;
User credential owner -: You can define a senhasegura user owner of the credential. When determined, only the owner user will always have access to the credential and can make changes to it;
senhasegura Administrator can change the owner at any time, but you can use Notification to alert the user owner if some administrator changed thecredential owner, it also possible to check any change in Reports ➔ Traceability ➔ Credential.
Server path: Path that is used in password exchange templates when the credential is registered into a physical file;
Additional authentication fields (grid): Additional fields for authentication on websites. Some sites require a lot of additional information to complete the login steps. You can give an alias to the values to complement the web authentication script;
Notes: General credential Notes;
Criticality: Set the criticality of the credential by choosing one of the following options: High, Medium, or Low, this will affect the Behavior functionality.