Microsoft®Azure DevOps
Microsoft®Azure Pipelines automatically builds and tests code projects to make them available to others. It works with just about any language or project type. Microsoft®Azure Pipelines combines continuous integration (CI) and continuous delivery (CD) to constantly and consistently test and build your code and ship it to any target.
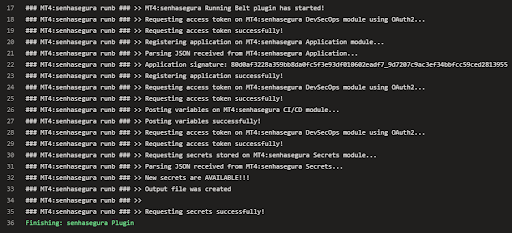
With the senhasegura Azure DevOps Plugin plugin, it is possible to inject secrets in real time during the execution of a pipeline without the need to expose sensitive information.
In addition, the plugin will intercept all variables in the pipeline so that administrators can identify if there is sensitive information not managed by the solution. It also register all secrets as environment variables transparently for developers.
Installing Microsoft®Azure DevOps plugin
To install the senhasegura Azure DevOps Plugin plugin, follow these steps:
Login into a project in your Microsoft®Azure DevOps account;
Add the binary and the
senhasegura-mapping.jsonfile to the project repository;infoThe
senhasegura-mapping.jsonfile could be used to report senhasegura DSM which variables should be faced as secrets.Edit the
azure-pipelines.ymlfile, located at your project folder;Into the steps section, input the code below as an example:
- task: Bash@3
displayName: 'senhasegura Plugin'
inputs:
targetType: filePath
filePath: ./senhasegura
arguments: '${APP} ${SYSTEM} ${ENVIRONMENT}'
env:
APP: <app_name>
SYSTEM: <app_system>
ENVIRONMENT: <app_environment>Save it;
infoThe variables
APP,ENVIRONMENTandSYSTEMwill be used to identify and report to senhasegura DSM , what is the application and in which environment and system it will be running.Execute the pipeline;
Secrets injection into Microsoft®Azure DevOps pipelines
After installing the plugin in the target project, follow the steps to inject the secrets into your pipeline:
Follow the menu Pipelines ➔ Pipelines;
Select the pipeline and click Run Pipeline;
In the next step, click Run;
Click on the Job name to display the result;